SAP SuccessFactors

This connectivity package provides support for managing users and groups in SAP SuccessFactors through SCIM API.
Supported objects and operations
| SuccessFactors | Omada Identity data model | Operations |
|---|---|---|
| Users | Account | Read |
| Groups (Dynamic) | Resource | Read |
| Groups (Static) | Resource | Read |
| Groups Assignment (Dynamic) | Resource assignment | Read |
| Groups Assignment (Static) | Resource assignment | Create, read, delete |
Minimum required permissions
You need to have access to the API, including relevant permissions.
Implementation notes
SAP SuccessFactors has an important limitation: the API allows reading dynamic groups but does not support writing (provisioning or deprovisioning) to them. Reading and writing are only possible for static groups. Additionally, SAP SuccessFactors does not recommend using the SCIM API for user creation.
Network requirements
None.
Prerequisites
Depending on when you activated Identity Authentication, you might have already received the latest updates included in this upgrade. These updates involve X.509 certificate-based authentication along with the SCIM API, which are advanced methods for authentication and integration with Identity Authentication and Identity Provisioning. These features are automatically activated for upgrades that took place from December 9 2022 onward.
Perform the following steps to confirm you enabled this feature:
-
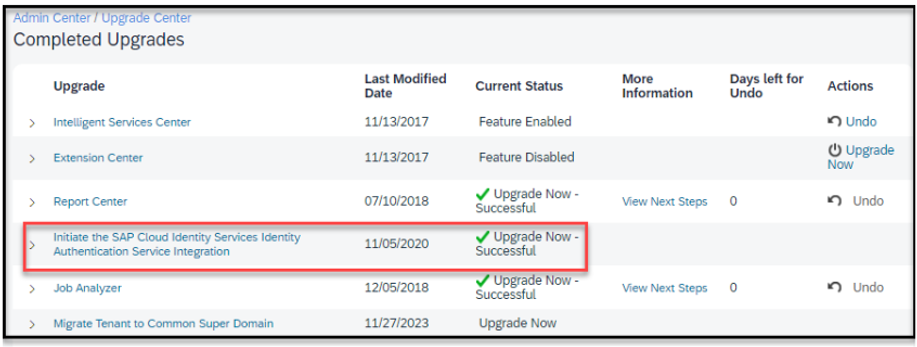
In SAP, navigate to Admin Center > Upgrade Center > View Recently Completed Upgrades.
-
Locate the upgrade titled Initiate the SAP Cloud Identity Services Identity Authentication Service Integration.
-
In the Current Status column, check the Upgrade Now - Successful status.
-
In the Last Modified Date column next to the status, confirm whether the date is before or after December 9 2022.
-
Choose one of the following steps:
- If you enabled Identity Authentication from December 9 2022 or later, see Getting Started with Identity Authentication Already Enabled in SAP documentation.
- If you enabled Identity Authentication before December 9 2022 or you did not enable it at all, see Existing Customers (Before December 9, 2022) in SAP documentation.
Cloud Identity Services configuration
SCIM APIs don’t support case-sensitive usernames. Check the following prerequisites:
- Check for duplicate usernames in Admin Center > Check Tool > Migration > Application > User Account Management.
- Go to Admin Center -> Company System and Logo Settings. Select the Enable Case-Insensitive Usernames option.
The Identity Authentication Service Administrator system is automatically created when you initiate the upgrade process in the Upgrade Center of SAP SuccessFactors. See SAP Cloud Identity Services for details what you can modify or add in the Identity Authentication Service.
Cloud Identity Services - source system
-
Log in to the Administration Console. Access the Identity Authentication Administration Console (ensure you have administrative permissions).
-
Navigate to the Source Systems section.
-
In the left-hand navigation panel, go to Identity Providers. Select Source Systems.
-
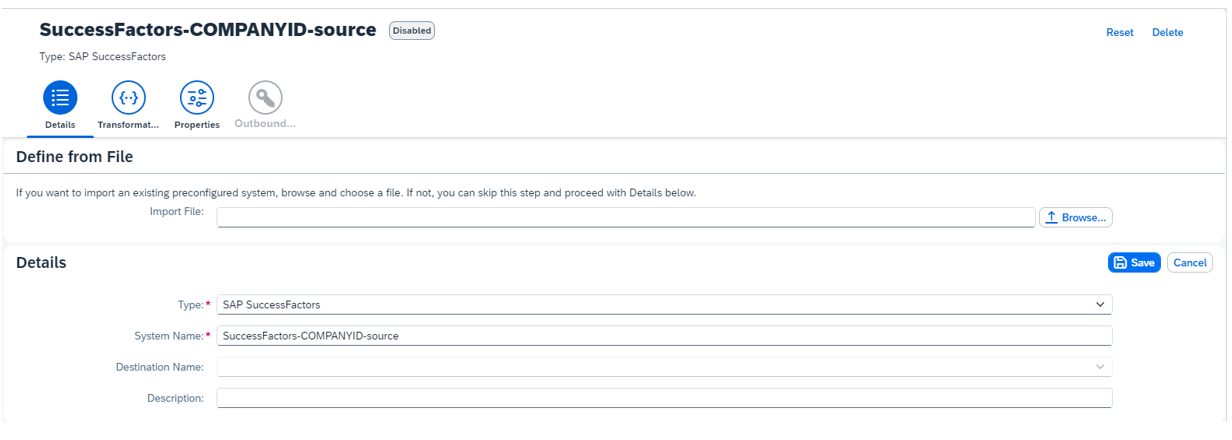
Click Add to create a new source system and enter the source system details:
- type: SAP SuccessFactors
- system name:
SuccessFactors-<COMPANYID>-source
-
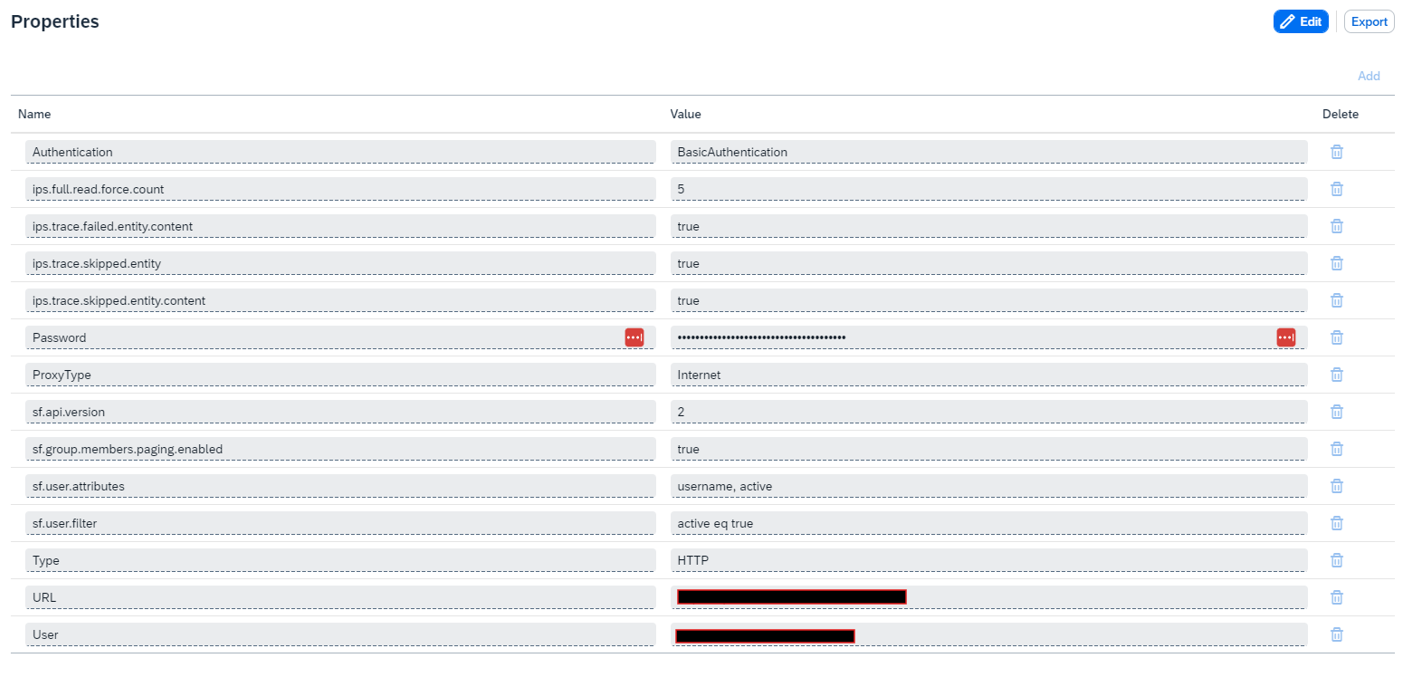
Go to the Properties tab. At the top right corner, click Add.
-
Use the following properties (see the List of properties for the full list of options):
- Authentication: BasicAuthentication
- ips.full.read.force.count: 5
- ips.trace.failed.entity.content: true
- ips.trace.skipped.entity: true
- ips.trace.skipped.entity.content: true
- Password:
{Password} - ProxyType: Internet
- sf.api.version: 2
- sf.group.members.paging.enabled: true
- sf.user.attributes: username, active
- sf.user.filter: active eq true
- Type: HTTP
- URL:
{URL} - User: user@companyId
-
Go to the Transformation tab. When you create a source system, a standard mapping is automatically provided. This default mapping often requires modifications to align with your specific needs (see Upgrade from ODATA IPS Connector to SCIM IPS Connector for the default transformation). Review the following example of a transformation that you can adapt:
{
"user": {
"mappings": [
{
"sourcePath": "$.schemas",
"preserveArrayWithSingleElement": true,
"targetPath": "$.schemas"
},
{
"sourcePath": "$.id",
"targetVariable": "entityIdSourceSystem"
},
{
"sourcePath": "$.userName",
"targetPath": "$.userName",
"correlationAttribute": true
},
{
"sourcePath": "$.name.familyName",
"optional": true,
"targetPath": "$.name.familyName"
},
{
"sourcePath": "$.name.givenName",
"optional": true,
"targetPath": "$.name.givenName"
},
{
"sourcePath": "$.userType",
"optional": true,
"targetPath": "$.userType"
},
{
"sourcePath": "$.displayName",
"optional": true,
"targetPath": "$.displayName"
},
{
"sourcePath": "$.emails[?(@.primary == true)].value",
"optional": true,
"targetPath": "$.emails[?(@.primary == true)].value",
"correlationAttribute": true
},
{
"sourcePath": "$.active",
"targetPath": "$.active"
},
{
"sourcePath": "$['urn:ietf:params:scim:schemas:extension:enterprise:2.0:User']['employeeNumber']",
"optional": true,
"targetPath": "$['urn:ietf:params:scim:schemas:extension:enterprise:2.0:User']['employeeNumber']"
},
{
"sourcePath": "$['urn:ietf:params:scim:schemas:extension:enterprise:2.0:User']['division']",
"optional": true,
"targetPath": "$['urn:ietf:params:scim:schemas:extension:enterprise:2.0:User']['division']"
},
{
"sourcePath": "$['urn:ietf:params:scim:schemas:extension:sap:2.0:User']['userUuid']",
"optional": true,
"targetPath": "$['urn:ietf:params:scim:schemas:extension:sap:2.0:User']['userUuid']"
},
{
"sourcePath": "$.groups",
"preserveArrayWithSingleElement": true,
"optional": true,
"targetPath": "$.groups"
}
]
},
"group": {
"mappings": [
{
"sourcePath": "$.id",
"targetPath": "$.id",
"targetVariable": "entityIdSourceSystem"
},
{
"sourcePath": "$.schemas",
"targetPath": "$.schemas"
},
{
"sourcePath": "$.displayName",
"targetPath": "$.displayName"
},
{
"sourcePath": "$.members",
"preserveArrayWithSingleElement": true,
"optional": true,
"targetPath": "$.members"
}
]
}
}
Cloud Identity Services - target system
-
Log in to the Identity Authentication Administration Console (ensure you have administrative permissions).
-
Navigate to the Target Systems section.
-
In the left-hand navigation panel, go to Identity Providers and select Target Systems.
-
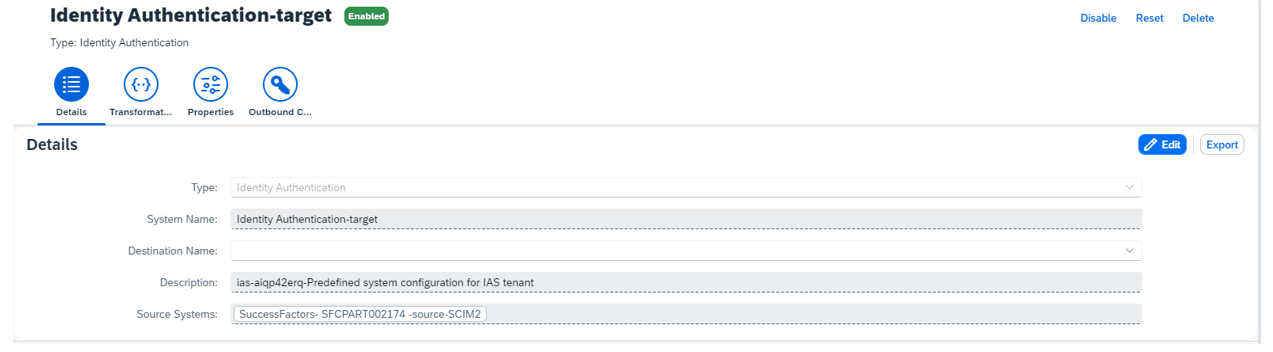
Click Add to create a new target system. Enter the following details:
- Type: Identity Authentication-target
- Source systems:
SuccessFactors-<COMPANYID>-source
-
Go to the Properties tab. At the top right corner, click Add to add new properties.
-
Use the following properties (see the List of properties for the full list of options):
- Authentication: BasicAuthentication
- ias.api.version: 2
- ips.delete.threshold.users: true
- ips.failed.request.retry.attempts: 2
- ips.trace.skipped.entity.content: true
- ips.failed.request.retry.attempts.interval: 60
- ips.trace.failed.entity.content: true
- sf.api.version: 2
- Password:
{Client_secret} - ProxyType: Internet
- scim.user.unique.attribute: userName
- Type: HTTP
- URL:
{URL} - User:
{Client_id}
-
Go to the Transformation tab. When you create a target system, a standard mapping is automatically provided. This default mapping often requires modifications to align with your specific needs (see Upgrade from ODATA IPS Connector to SCIM IPS Connector for the default transformation). Review the following example of a transformation that you can adapt:
{
"user": {
"condition": "($.emails.length() > 0)",
"mappings": [
{
"targetPath": "$.id",
"sourceVariable": "entityIdTargetSystem"
},
{
"targetPath": "$.schemas[0]",
"constant": "urn:ietf:params:scim:schemas:core:2.0:User"
},
{
"targetPath": "$.schemas[1]",
"constant": "urn:ietf:params:scim:schemas:extension:enterprise:2.0:User"
},
{
"targetPath": "$.schemas[2]",
"constant": "urn:sap:cloud:scim:schemas:extension:custom:2.0:User"
},
{
"sourcePath": "$.active",
"targetPath": "$.active",
"optional": true
},
{
"sourcePath": "$.userName",
"targetPath": "$.userName",
"optional": true
},
{
"sourcePath": "$.emails[*].value",
"targetPath": "$.emails[?(@.value)]",
"preserveArrayWithSingleElement": true
},
{
"sourcePath": "$.userType",
"targetPath": "$.userType","optional": true
},
{
"sourcePath": "$.name.givenName",
"targetPath": "$.name.givenName",
"optional": true
},
{
"sourcePath": "$.name.middleName",
"targetPath": "$.name.middleName",
"optional": true
},
{
"sourcePath": "$.name.familyName",
"targetPath": "$.name.familyName"
},
{
"sourcePath": "$.displayName",
"targetPath": "$.displayName",
"optional": true
},
{
"sourcePath": "$['urn:ietf:params:scim:schemas:extension:enterprise:2.0:User']['employeeNumber']",
"targetPath": "$['urn:ietf:params:scim:schemas:extension:enterprise:2.0:User']['employeeNumber']",
"optional": true
},
{
"sourcePath": "$['urn:ietf:params:scim:schemas:extension:enterprise:2.0:User']['division']",
"targetPath": "$['urn:ietf:params:scim:schemas:extension:enterprise:2.0:User']['division']",
"optional": true
},
{
"sourcePath": "$['urn:ietf:params:scim:schemas:extension:enterprise:2.0:User']['department']",
"targetPath": "$['urn:ietf:params:scim:schemas:extension:enterprise:2.0:User']['department']",
"optional": true
},
{
"sourcePath": "$['urn:sap:cloud:scim:schemas:extension:sfsf:2.0:User']['personGUID']",
"targetPath": "$['urn:sap:cloud:scim:schemas:extension:custom:2.0:User']['attributes'][0]['value']","optional": true
},
{
"targetPath": "$['urn:sap:cloud:scim:schemas:extension:custom:2.0:User']['attributes'][0]['name']",
"condition": "$['urn:sap:cloud:scim:schemas:extension:sfsf:2.0:User']['personGUID'] EMPTY false",
"constant": "customAttribute1"
},
{
"targetPath": "$.password",
"constant": "Part@dc57",
"scope": "createEntity"
}
]
},
"group": {
"mappings": [
{
"targetPath": "$.id",
"sourceVariable": "entityIdTargetSystem"
},
{
"sourcePath": "$.displayName",
"targetPath": "$.displayName"
},
{
"targetPath": "$.schemas[0]",
"constant": "urn:ietf:params:scim:schemas:core:2.0:Group"
},
{
"targetPath": "$.schemas[1]",
"constant": "urn:ietf:params:scim:schemas:extension:sap:2.0:Group"
},
{
"targetPath": "$.schemas[2]",
"constant": "urn:sap:cloud:scim:schemas:extension:custom:2.0:Group"
},
{
"sourcePath": "$.displayName",
"targetPath": "$['urn:sap:cloud:scim:schemas:extension:custom:2.0:Group']['name']",
"scope": "createEntity",
"functions": [
{
"function": "replaceAllString",
"regex": "[\\s\\p{Punct}]","replacement": "_"
}
]
},
{
"sourcePath": "$['urn:sap:cloud:scim:schemas:extension:custom:2.0:Group']['name']",
"targetPath": "$['urn:sap:cloud:scim:schemas:extension:custom:2.0:Group']['name']",
"optional": true,
"scope": "createEntity"
},
{
"sourcePath": "$['urn:sap:cloud:scim:schemas:extension:custom:2.0:Group']['description']",
"targetPath": "$['urn:sap:cloud:scim:schemas:extension:custom:2.0:Group']['description']",
"optional": true
},
{
"sourcePath": "$.members[*].value",
"targetPath": "$.members[?(@.value)]",
"optional": true,
"preserveArrayWithSingleElement": true,
"functions": [
{
"function": "resolveEntityIds"
}
]
}
]
}
}
Testing the system
To test if the synchronization between SAP SuccessFactors and IPS is working, navigate to Identity Provisioning > Source System and go to the Jobs tab. Locate the Read Job row and click Run Now.
Checking Client ID and Client Secret
- Navigate to the Applications and Resources menu. Go to the Applications and Resources section.
- Search for
Applications. - In the Applications and Resources menu, click Applications.
- Access the application which was created with the Upgrade Center of SAP SuccessFactors Center.
- Inside the Applications section, locate and select Client Authentication. In the Client Authentication page, you will see your Client ID listed.
