Lifecycle management
Resource Lifecycle Management
Through Resource Lifecycle Management, OPS provides a simple way of creating, updating, and removing resources in target systems. RLM employs the logical key - or ODWLOGICKEY - which is a configurable key that can be used to match resource objects. This logical key works across Omada Identity components and is therefore relevant for OPS, ODW, and ES.
Creating resources in Active Directory is the primary scenario where Resource Lifecycle Management (RLM) is used. In the RLM, a resource is first created in ES and then in the target system through the OPS. When the resource is imported and subsequently exported, the ODWLOGICKEY helps to ensure that the resources are linked to each other as they represent the same object in the target system.
Data Object Lifecycle Management
The Data Object Lifecycle Management (DOLM) is similar to the Resource Lifecycle Management, allowing however to create, update, and remove all types of data objects in the target system. It is utilized in the Active Directory to manage organizational units.
Shadow data objects

Shadow data objects, although they are not real data objects, can be used in many cases like standard data objects (for example, in the Data Object Lifecycle Management). You can create provisioning tasks for calculated resource assignment types and define task mappings for them using Data Object Lifecycle Management code methods. This opens up new possibilities:
- creation/single change in the calculated resource assignment (CRA) may trigger the creation of several provisioning tasks
- change in the CRA in one system may create provisioning tasks in the other system
- event definition filters provide control when the provisioning task should be created
Shadow data objects provide support for various scenarios that wouldn't otherwise be possible:
- performing additional actions after an account is created (in the same or other system)
- sending initial passwords to users using customer APIs
- performing an update action only when a specific property is changed (for example, activating/deactivating)
Shadow data objects' advantages:
- Improved automation: eliminates manual intervention by automatically creating provisioning tasks.
- Enhanced security: ensures controlled password distribution.
- Flexibility: supports advanced mapping (shadow objects) and custom workflows.
- Reliability: prevents failure scenarios by ensuring accounts are created before credentials are sent.
- Scalability: allows integration with additional APIs and external task management platforms.
Selecting the Data Object mapping type displays data objects prefixed with Calculated assignment for in the dropdown menu, indicating their nature.
- In the system onboarding view, enable provisioning. Configure all connector settings the and data model. Set
secureStringTypefor password, for example:
<connectorDataModel xmlns="http://schemas.omada.net/ops/2015/ConnectorDataModelML" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<properties>
<property name="user" />
<property name="pass" dataType="secureStringType" />
</properties>
<objects>
<object name="Password">
<objectProperties>
<objectProperty>user</objectProperty>
<objectProperty>pass</objectProperty>
</objectProperties>
</object>
</objects>
</connectorDataModel>
-
Add the task mapping for the calculated assignment account (from the system of your choice). You may need to set the
Intial Passwordattribute on the account resource type attribute set for the attribute to be visible as the source in the task.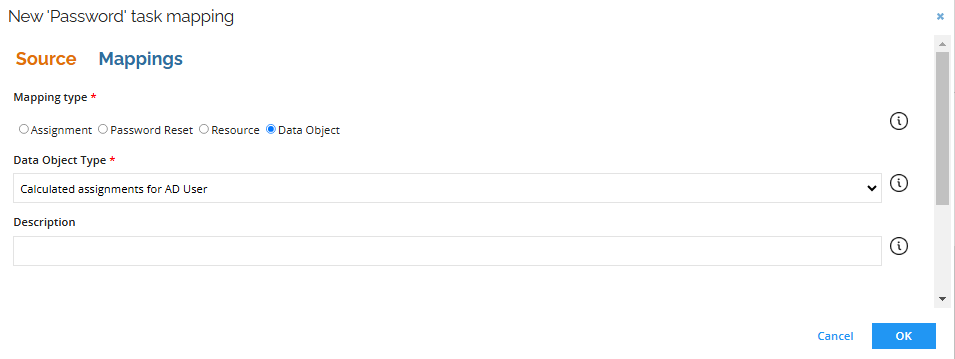
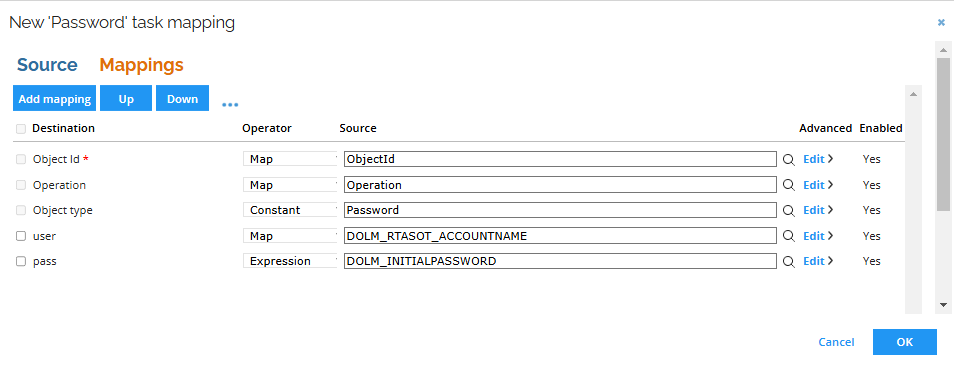
-
Commit the settings.
-
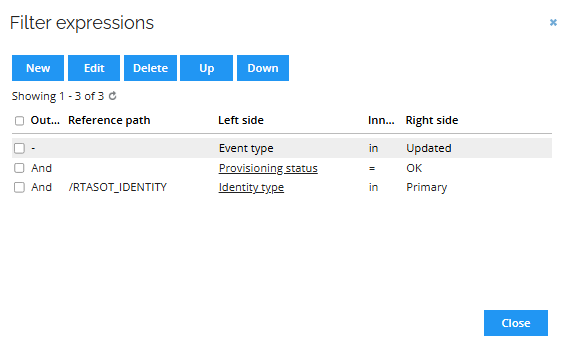
Go to Setup > Event definitions and click New. Enter the following details:
-
Event is triggered when: Choose the option matching your use case (for example, creation of calculated resource assignments). Use filters for all conditions. If the notification time is crucial, select on create or on update with the OK - pending confirmation filter.
-
Triggers on objects of type: Choose the same object type as used in the task mappings.
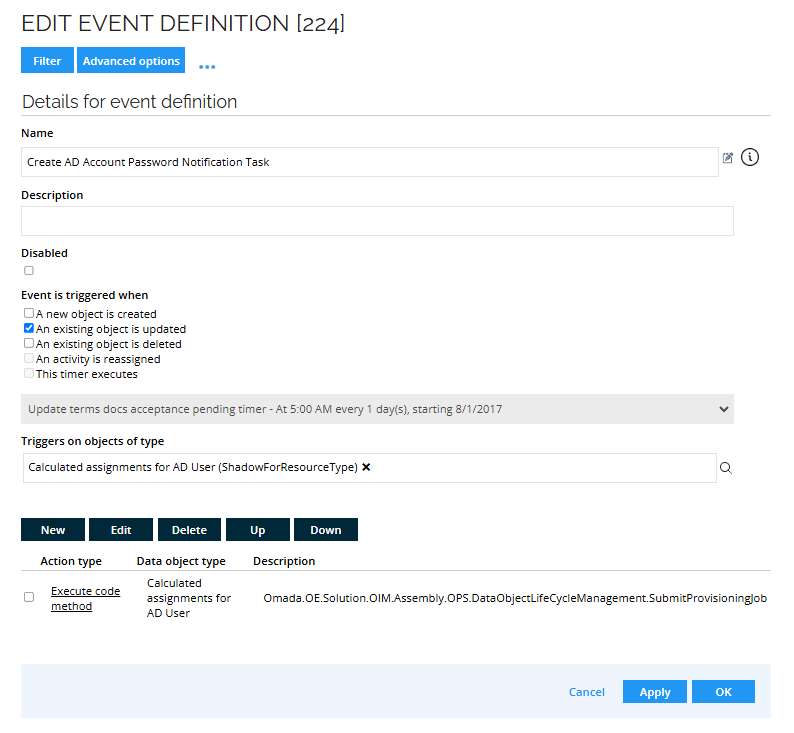
-
-
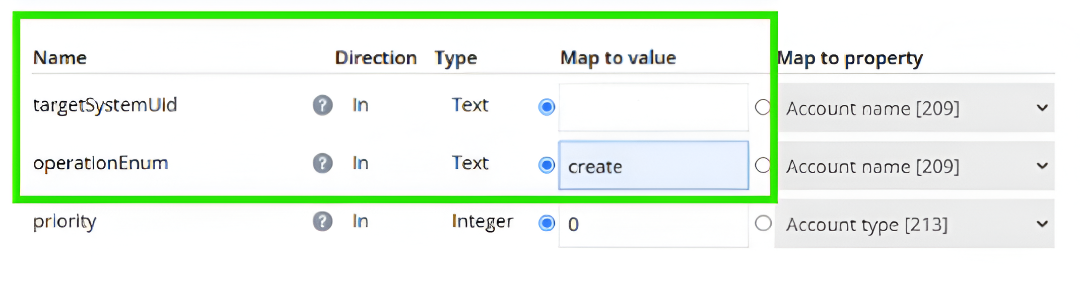
Add a new action. Select the option to execute the
DataObjectLifeCycleManagement.SubmitProvisioningJobcode method. In the code method parameters, provide UID of your password notification system (targetSystemUid) andoperationEnum, setting the Map to value tocreate.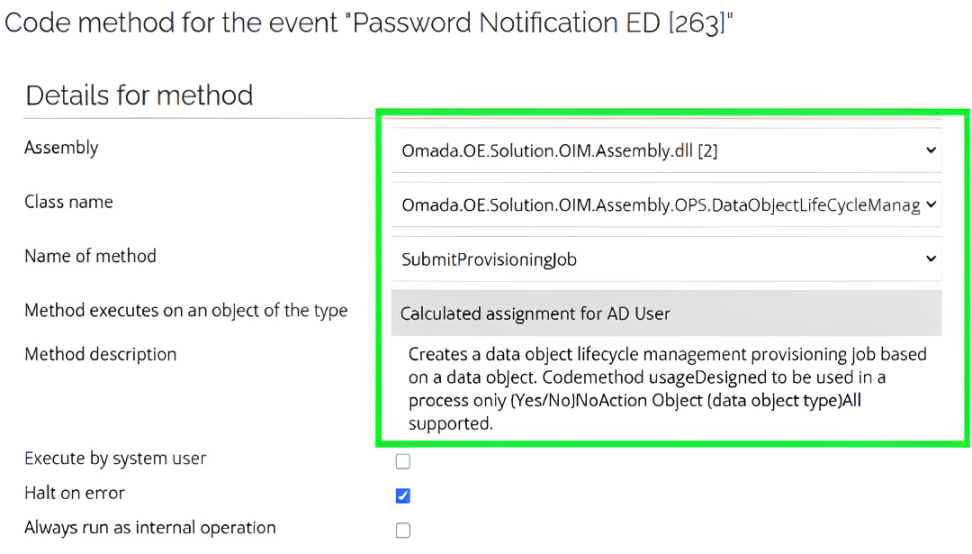
Result: From now on, provisioning tasks for password notifications are created for new accounts.
