Microsoft Azure Active Directory
This is a legacy connectivity package for Azure Active Directory. To onboard a new Entra ID system and utilize all connectivity features, use the Entra ID connector.
To migrate from the existing Azure Active Directory connector to the new Entra ID connector, see Migrating from the existing Azure Active Directory connector to Entra ID.
The Omada Microsoft Azure Active Directory connectivity is used for governing and managing Microsoft Azure Active Directory instances. It is based solely on Microsoft Graph API. By using this package you can:
- Register and onboard any number of Azure Active Directory instances.
- Load information about users, groups, group memberships, and used licenses.
- Automate the provisioning and de-provisioning of Azure Active Directory users, groups, and memberships.
Each Azure Active Directory instance must be onboarded in a separate onboarding process.
Supported objects and operations
This connectivity package allows you to manage both identity data and access rights. However, the default mappings are provided only for access rights as this connectivity is typically used for that type of data.
| Object | Possible operations |
|---|---|
| Users | Create, read, update, delete |
| User passwords | Create, update |
| Assignments | Create, delete |
| Groups | Create, read, update, delete |
| Group Memberships | Create, read, update, delete |
| Directory Roles | read |
| Directory Roles Assignments | Create, read, update, delete |
In addition, this connectivity package supports the following scenarios:
- Extraction of assignments between
- Groups and users
- Directory roles and users
- Groups and groups
- Extraction of Stock Keeping Units (SKUs) and included service plans
- Extraction of a user’s assigned licenses
- Extraction of a user’s assigned service plans
- User provisioning
- Password reset
- Assignments
- Add and remove assignments between groups and users
- Add and remove assignments between directory roles and users
Minimum required permissions
None.
Implementation notes
The Microsoft Azure Active Directory connectivity package only includes directory roles that are enabled. You must create and enable directory roles - both custom directory roles and from templates – in the Microsoft Azure Portal.
Prerequisites
Before importing information from Azure Active Directory to Omada Identity, perform the following setps in the Microsoft Azure Portal.
Register a new application in Azure Portal
Create an application registration to authenticate and authorize Omada Identity with Azure Active Directory:
-
In the Azure portal, go to your directory. In the Manage section, find the App registrations, then click New registration.
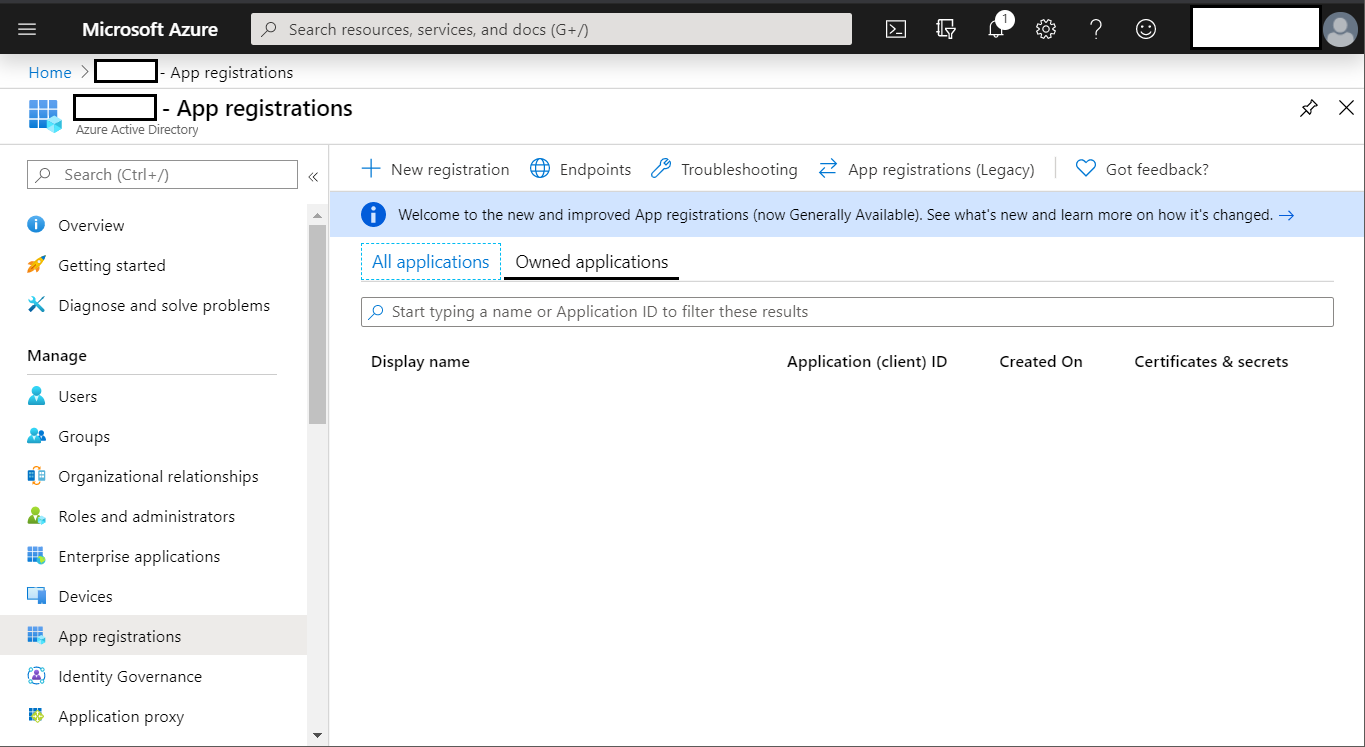
-
In the Register an application dialog box, enter a Name, select Accounts in any organizational directory as Supported account types, and enter a Redirect URI. You can enter any value that you want to use, as long as it is in a valid URL format.
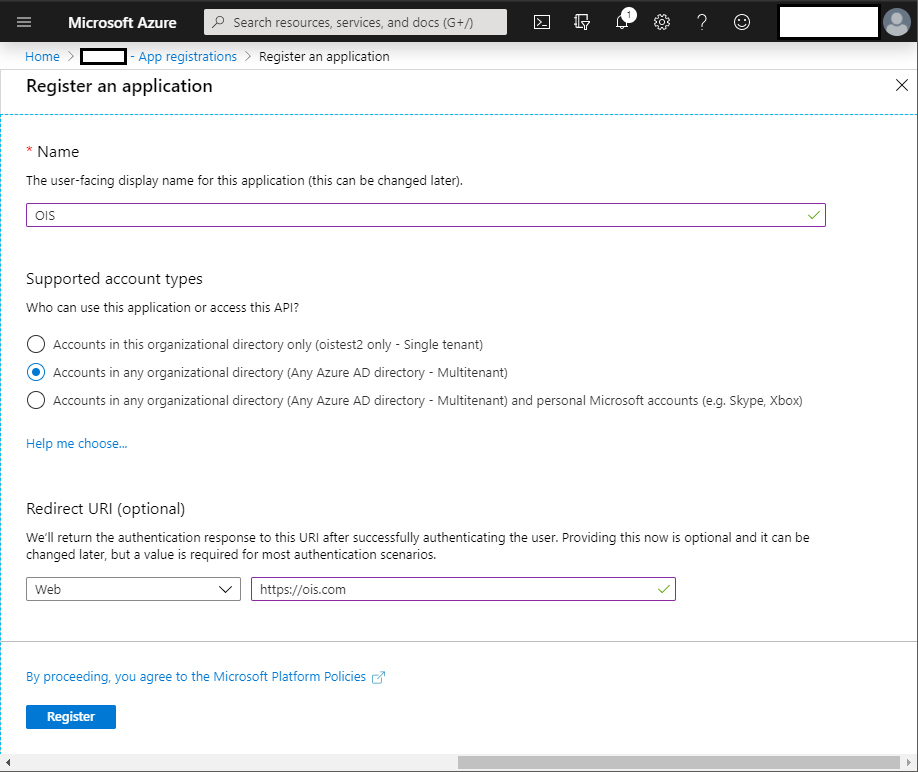
-
When you click Register, the application is registered. Make a note of the Application ID. You must use the Application (client) ID when you onboard the system to Omada Identity.
infoThe Application ID shown in the following image is only an example. Your Application ID contains a different value.
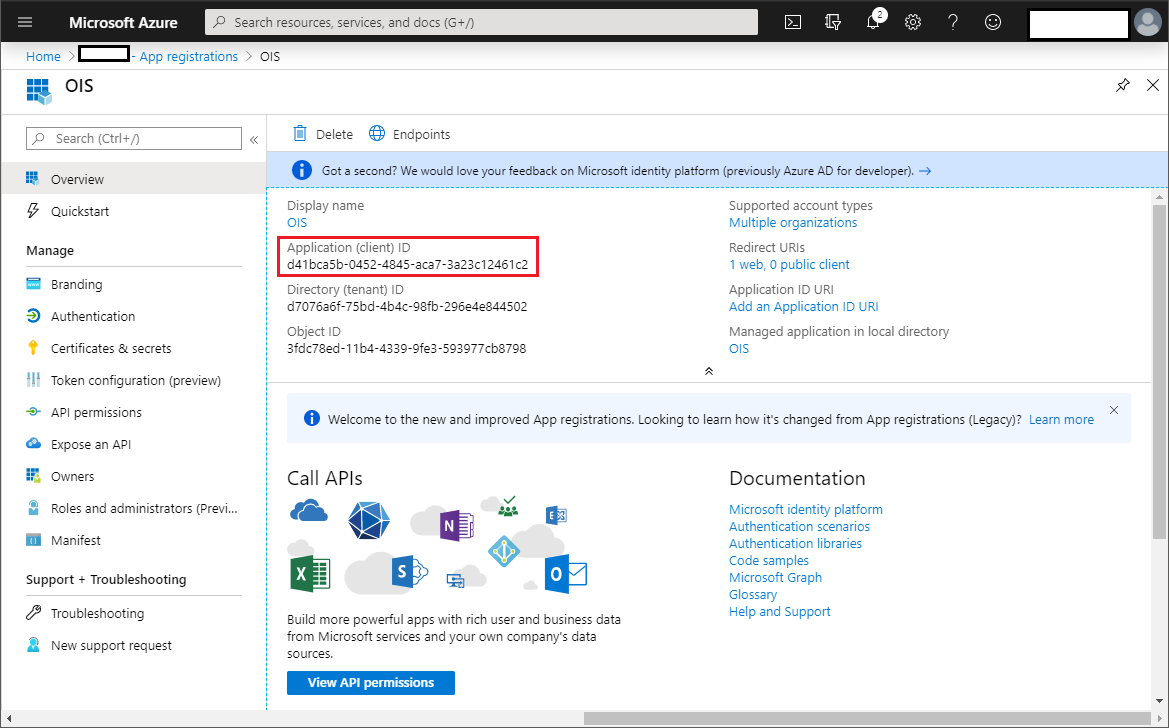
Add Graph API
The connectivity add-on uses the Microsoft Graph API to read and write information to the directory. Add the Graph API for the registered application:
-
Go to API permissions and select +Add a permission.
-
Choose Microsoft Graph from Commonly used Microsoft APIs from the Supported legacy APIs and click Select.
-
Select all needed Application permissions.
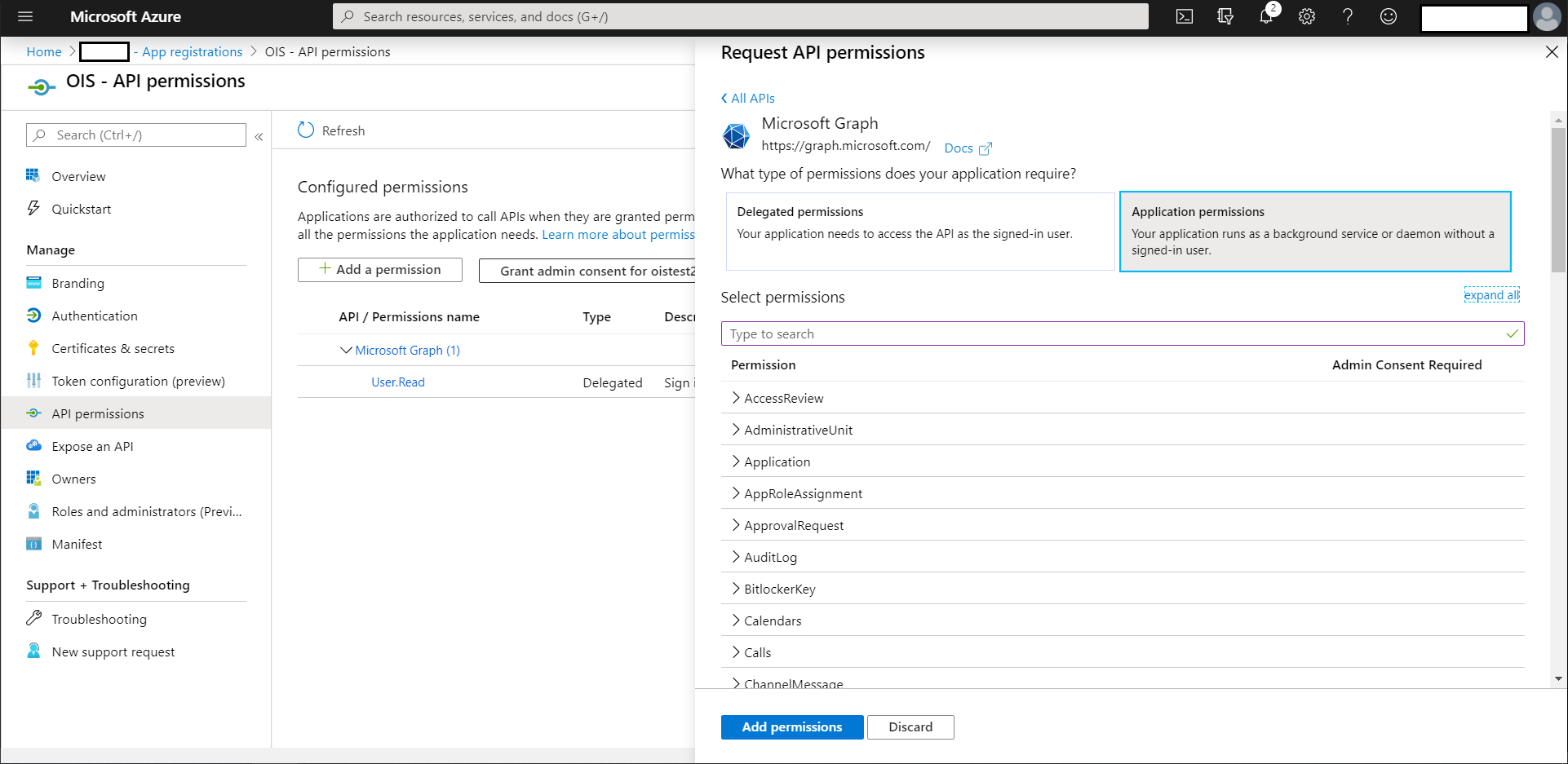
-
Click the Add permissions button.
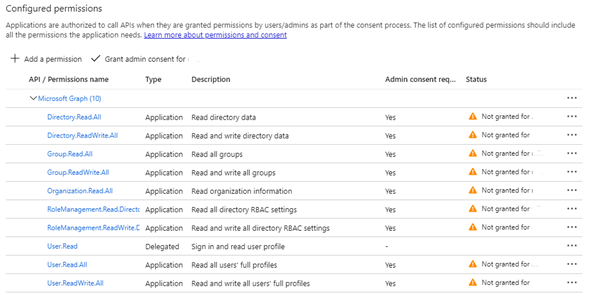
The table below presents the minimum required permissions for the correct connection between Microsoft Azure Active Directory and Omada Identity.
MICROSOFT GRAPH
Permission Type Directory.Read.All Application Directory.ReadWrite.All Application Group.Read.All Application Group.ReadWrite.All Application User.Read.All Application User.ReadWrite.All Application RoleManagement.Read.Directory Application RoleManagement.ReadWrite.Directory Application OFFICE 365 RELATED PERMISSIONS
To import SKUs or service plans you must also include the following permission:
- Organization.Read.All - type: Application
-
After adding the permission, you must grant consent to the permissions. To do that, click Grant admin consent for button.
Create a Client Secret
-
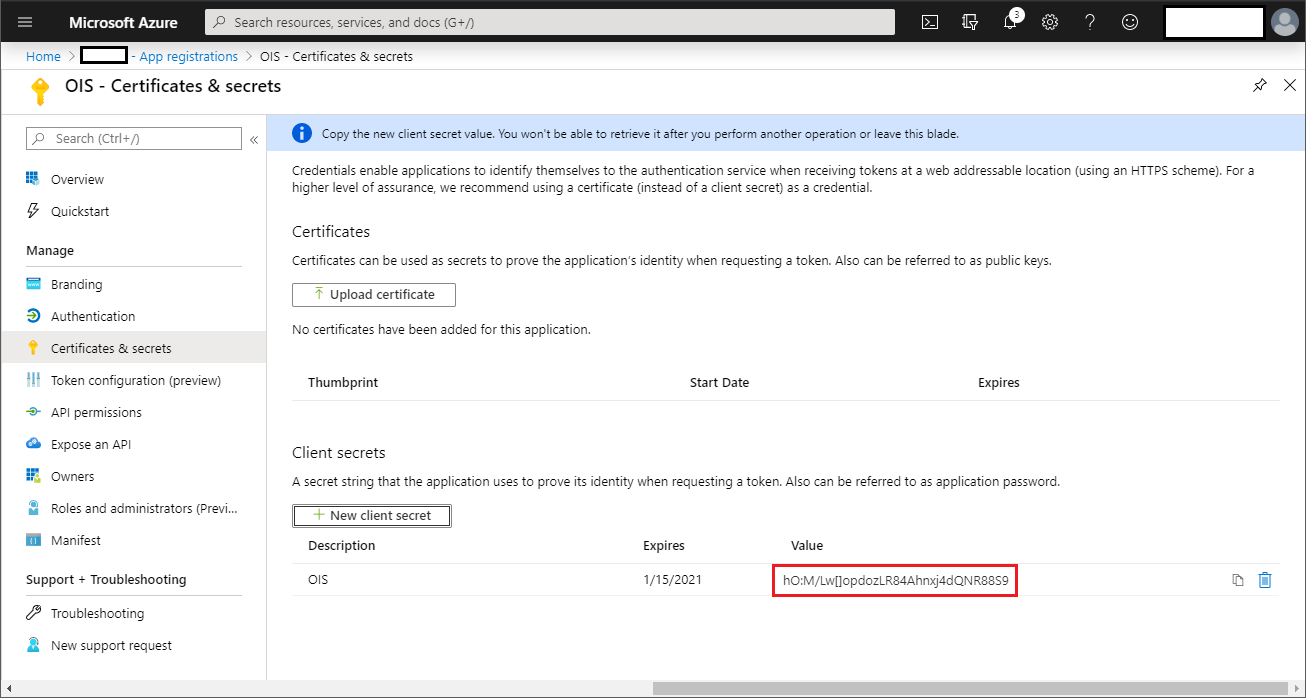
Go to Certificates & secrets select + New client secret.
-
If you want to, type a description for the secret key, for example, to identify one secret key from other keys.
-
If you want to, chose an expiration time for the secret, then click Add.
-
Copy the generated key shown under Value. You cannot see the value again when you have left the screen, so you can only use this key if you copy it now and paste it in Omada Identity after setting up the Omada Identity application on Azure.
-
Your Microsoft Entra ID is now ready to be registered with Omada Identity. You can create as many secret keys as you require.
Allow password reset and deletion of users and group assignments in Microsoft Azure Active Directory
To delete a user or group in Microsoft Azure Active Directory, you must first assign your application’s principal a User Account Administrator role. If you use Microsoft Graph, perform the same operation for the password reset to work. Choose one of the following options:
- Using the portal
- Using the script
-
Go to https://portal.azure.com.
-
Click Microsoft Entra ID.
-
Click Roles and administrators.
-
Click User administrator role.
-
Click + Add assignments.
-
In the search box, enter the name of the application you have created in the Register a new application in Azure Portal step.
-
Click Add.
Ensure you have installed MSOnline PowerShell.
- In Windows, open a PowerShell window.
- Enter the following command, ensuring you first change the highlighted parameters, and then run the command:
# 1. Log me into my MSDN tenant using an account I set up as "global admin".
Connect-MsolService
# 2. Replace the ApplicationID value and use it to get MsolServicePrincipal.
$ApplicationID = 'c3969eb4-c227-4211-9eef-32a8d18b053a'
$webApp = Get-MsolServicePrioncipal -AppPrincipalId $ApplicationID
# 3. Use Add-MsolRoleMember to add it to "User Administrator" role.
Add-MsolRoleMember -RoleName "User Administrator"
-RoleMemberType ServicePrincipal -RoleMemberObjectId $webApp .ObjectId
