Data import
Prerequisites
The Omada Identity's customer setting Active Directory category ID defines the ID of the system category, that contains Active Directory accounts used to log in to Omada Identity. The setting affects authorization when users access My reports with the use of integrated authentication.
The default value is AD, which reflects that the Active Directory Collector is used. The value must be changed if the Microsoft Active Directory Collector is used instead. Run the configuration import profile for the setting to take effect.
General settings
| Setting | Description |
|---|---|
| Name | Type a unique name for the system. Two systems cannot have the same name. |
| System ID | Type a unique System ID for the system. Two systems cannot have the same System ID. You cannot change this setting. |
| Description | Type an optional description of the system. |
| Status | Status of the system. Set the status to Removed to ensure the system is no longer included in warehouse imports, reconciliation or provisioning. Setting a system as removed will delete all objects referring to the system, including resources, manual and automated provisioning tasks, and assignment policies. |
| Content | The type of content to import. You can choose: - Identity data - Access rights - Both (Identity data and access rights) |
| Trusts | Optionally, select one or more trusted systems to associate with the system. |
Trust is specifically designed for use between physical systems. It is not intended for use between logical and physical systems.
Connection details
| Parameter | Description |
|---|---|
| Authentication type | Choose type of authentication used for the connection to Active Directory. The authentication type determines how the user, domain, and password settings are used. |
| Username | Enter the username of the Active Directory user utilized for reading information from the domain. Specify the sAMAccountName of the user, for example,administrator. The specified user must have read access and the Replicating Directory Changes permission assigned to the root of the partition. |
| Password | Enter the password to use with the AD user entered above. Each time you make a change to any of the settings in the Connection details dialog box, you must enter your password again. |
| Domain | Enter the DNS name of the domain, for example, corporate.com or the IP address. |
| Distinguished name of root | Enter the distinguished name of the root on the domain, for example, DC=corporate,DC=com. |
| SSL | The SSL encryption of the communication with Active Directory is optional, but recommended. This option requires a valid certificate to be installed on the Domain Controller(s) and on the Omada servers where OPS and ODW resides. For the Omada Identity Cloud, the certificates are imported via the Management Portal. |
| Skip certificate check | Select this checkbox to ignore any certificate check when connecting using SSL. |
| Port number | Specify the TCP port number used for connecting to Active Directory. The default port is 389. If SSL is used, the default port is 636. |
| Test connection | Enable this setting to allow the system to check if the connection details are correct. |
| Test filter | Provide an LDAP filter for the Test connection option, for example, objectClass=user. |
Queries and mappings
In the case of the Microsoft Active Directory connectivity, the following parameters can be defined for each query.
| Parameter | Description |
|---|---|
| LDAP Filter | Specify an LDAP filter to import specific objects. The filter must follow the LDAP filter specification, for example, (objectClass=person). For more information, go to https://ldap.com/ldap-filters/. The LDAP filter is required. |
| Sub-tree filter | Specify a sub-tree filter to import only objects from a specific sub-tree, for example, OU=users,DC=corporate,DC=com. This filter would ensure that only objects for organizational unit Users, or any OU below it, are imported. The Sub-tree filter is optional; if it is not specified, all objects in the domain matching the LDAP filter are imported. |
| Filter | Logical expression for each imported row. If evaluated to false - the row is skipped. |
| Description | Type an optional description of the query. |
Depending on the target object type, that is, Account or Resource, a set of mappings must be defined.
It is possible to use almost any LDAP attribute in your mappings, either by directly mapping the attribute to the destination or using it as part of an expression or lookup. Attributes that cannot be used in mappings are binary attributes.
For queries yielding multiple staged rows based in a reference attribute in Active Directory, that is, Resource assignments, Resource parent/children, or resource owners, the reference value will be available as attribute valuesid. As the name implies, the value will be available as the objectsid of the reference object.
Another special attribute is isUserAccountDisabled, which is available on account queries. The attribute has the value true if the account is disabled, and false if it is enabled.
Exercise caution when modifying the queries and mappings provided as the default.
- For accounts, the objectsid attribute of the account is imported as the Unique ID. Note that the resource assignment query relies on this mapping.
- For accounts, the msDS-PrincipalName attribute is mapped to the Account name. The msDS-PrincipalName attribute returns the account name supplied with the domain name. This supplementation is essential in a multi-domain environment where the same account name can be used for different accounts and domains.
- For account mappings, Account name, Distinguished name, and Path should be changed if you also import mailbox information using the Exchange collector. The exchange collector relies on these three property values to identify which account a mailbox belongs to.
- For accounts, the attribute sAMAccountName is imported as an extension attribute with the same name. This extension attribute is, by default, used for account ownership matching. If you change this mapping, make sure to adjust the account matching rules as well.
- For resources, the objectsid attribute of the group is imported as an extension attribute ResourceObjectSid. This extension attribute is, by default, used in the child resource lookup in the Parent/Child query.
- Business keys for accounts and resources are mapped using an expression. The expression is constructed, so the business key is similar to the business key used by the legacy AD collector. If you use the legacy AD collector and wish to migrate the data, do not change the business key mappings
There are default queries provided for the import of computers, parent-child relationships, and resource owners. It is highly recommended to disable or remove these queries if the data is not relevant to you. Removing these queries, especially resource parent-child and resource owners, will increase performance noticeably.
Provided mappings
The following queries and mappings are provided out of the box for the Microsoft Active Directory Connectivity.:
- Users - Accounts
- Computers - Accounts
- Security groups and Distribution groups - Resources
- Security group memberships - Resource assignments
- Nested groups - Resource parent/child relationships
- Group managers - Resource owners
Users - Accounts
With this mapping, Active Directory users are imported as accounts in the Data Warehouse.
When importing accounts, you can add manager attributes using the prefix manager_ + attributeName. For example, to add the attribute sAMAccountName of the manager, use the following mapping:
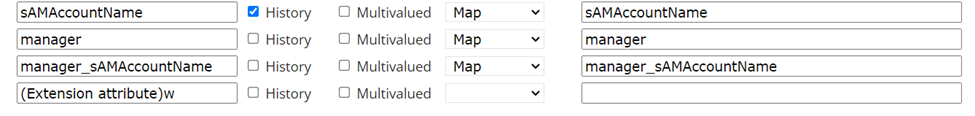
A manager is represented by an account. The attribute names must be the same as for user accounts (to add the attribute sAMAccountName, configure the attribute manager_sAMAccountName).
| Parameter | Value |
|---|---|
| LDAP filter | (objectCategory=person)(objectClass=user)(!objectClass=computer) |
| Active Directory | Data Warehouse | Comment |
|---|---|---|
| <system>"+BuiltIn.SystemShortName+"</system><sid>"+ objectsid+"</sid>" | BusinessKey | The expression used for the business key is constructed to be identical as in the old collector. Don’t change it if you need to migrate. |
| objectsid | UID | The unique id is mapped to the objectsid. This value is expected by the resource assignment query. |
| msDS-PrincipalName | AccountName | Account name is mapped to msDS-PrincipalName, to support multiple accounts from different domains with the same sAMAccountName. |
| distinguishedName | DistinguishedName | Do not change this mapping if you’re importing Microsoft Exchange mailbox information using the Exchange collector. |
| canonicalName | Path | Do not change this mapping if you’re importing Microsoft Exchange mailbox information using the Exchange collector. |
| sAMAccountName | sAMAccountName | The sAMAccountName is imported as an extension attribute. Note that the value is used by the account rules to detect ownership. The mapping can be changed, but the account rules must subsequently be adjusted. |
| name | Description | |
| isUserAccountDisabled == null ? null : (Convert.ToBoolean(isUserAccountDisabled) ? "Disabled" : "Active") | Status | |
| whenCreated | ValidFrom | |
| accountExpires | ValidTo | |
| domain | Domain | |
| displayName | DisplayName | |
| userAccountControl | StatusMask | |
| lastLogonTimestamp | LastLogon | |
| pwdLastSet | LastPasswordChange | |
| givenName | givenname | |
| sn | sn | |
| - | Category |
Computers - Account
With this mapping, Active Directory computers are imported as accounts in the Data Warehouse.
| Parameter | Value |
|---|---|
| LDAP filter | (objectCategory=computer)(objectClass=computer) |
| Active Directory | Data Warehouse |
|---|---|
| "<system>"+BuiltIn.SystemShortName+ "</system><sid>"+objectsid+"</sid>" | BusinessKey |
| The expression used for the business key is constructed to be identical as in the old collector. Don’t change it if you need to migrate. | |
| Computer | Category |
| The category is set to Computer in order to distinguish these from actual accounts. | |
| objectsid | UID |
| sAMAccountName | AccountName |
| displayName | DisplayName |
| name | Description |
| whenCreated | ValidFrom |
| accountExpires | ValidTo |
| domain | Domain |
| distinguishedName | DistinguishedName |
| canonicalName | Path |
| userAccountControl | StatusMask |
| lastLogonTimestamp | LastLogon |
| pwdLastSet | LastPasswordChange |
| - | Status |
Security groups and Distribution groups - Resources
Active Directory security groups and distributions groups are imported as resources in the data warehouse using a single query.
| Parameter | Value |
|---|---|
| LDAP filter | (objectCategory=Group)(objectClass=group) |
| Active Directory | Data Warehouse |
|---|---|
| "<system>"+BuiltIn.SystemShortName+ "</system><sid>"+objectsid+"</sid>" | BusinessKey |
| The expression used for the business key is constructed to be identical as in the old collector. Don’t change it if you need to migrate. | |
| groupType.Contains("214748364")?"Active Directory - Security Group":"Active Directory - Distribution Group" | Type |
| The expression used for Type ensures that groups are represented as Security Groups and Distribution groups in the Warehouse and in the Enterprise Server. | |
| objectsid | ResourceObjectSid |
| The objectsid of the group is imported as an extension attribute. This value is used by the Resource parent/child query to ensure it is possible to import cross-domain relations. | |
| "<system>"+BuiltIn.SystemShortName+ "</system><sid>"+objectsid+"</sid>" | SecurityResource_BusinessKey |
| name | Name |
| domain | Domain |
| sAMAccountName | ShortName |
| sAMAccountName | DisplayName |
| distinguishedName | DistinguishedName |
| canonicalName | Path |
| description | Description |
| Group | Category |
| (groupType.Last()=='0'|groupType.Last()=='8')?"Universal":(groupType.Last()=='4'?"Domain Local":"Global") | Scope |
| - | LogicKey |
Security group memberships - Resource assignments
Members of Active Directory security groups or distribution groups of the Users type are imported as resource assignments with the use of the following mappings.
| Parameter | Value |
|---|---|
| LDAP filter | (objectCategory=Group)(objectClass=group) |
| Active Directory | Data Warehouse |
|---|---|
| "<system>"+BuiltIn.SystemShortName+ "</system><sid>"+objectsid+"</sid>" | Resource_BusinessKey |
| The expression must be similar to the expression used when importing groups. | |
| UID=valuesid | Account_BusinessKey* |
| This lookup uses the built-in collector attribute valuesid to look for the account in the current system using the objectsid. | |
| UID=valuesid | Account_ComposedBusinessKey* |
| This lookup uses the built-in collector attribute valuesid to look for the account in the current system using the objectsid. | |
| - | ValidFrom |
| - | ValidTo |
| - | Status |
| - | Description |
| - | PermissionLevel |
| - | PermissionMask |
| - | AccountIsGroup |
| - | BusinessKey |
* Either Account_BusinessKey or Account_CBK must be filled.
Standard mappings support assignments between different domains in the same forest, and assignment to a domain in an external forest.
If there are cross system assignments, you must configure the trust between the systems under the 1.0.1 General settings task. The trust must be configured on the system with the group or resource.
Nested groups - Resource parent/child relationships
Nested groups, or groups that are members of other groups, are imported as parent/child relationships.
If your Active Directory does not use nested groups it is recommended to disable/delete this query.
| Parameter | Value |
|---|---|
| LDAP filter | (objectCategory=Group)(objectClass=group) |
| Active Directory | Data Warehouse |
|---|---|
| false | Indirect |
| businesskey="<system>"+BuiltIn.SystemShortName+"</system> <sid>"+objectsid+"</sid>" | Parent resource business key |
| ResourceObjectSidWoH=valuesid | Child resource - business key |
| ResourceObjectSidWoH=valuesid | Child resource - CBK |
Standard mappings support nested groups between different domains in the same forest, and nested groups to a domain in an external forest.
If there are cross system relations, you must configure the trust between the systems under the 1.0.1 General settings task. The trust must be configured on the system containing the parent resource.
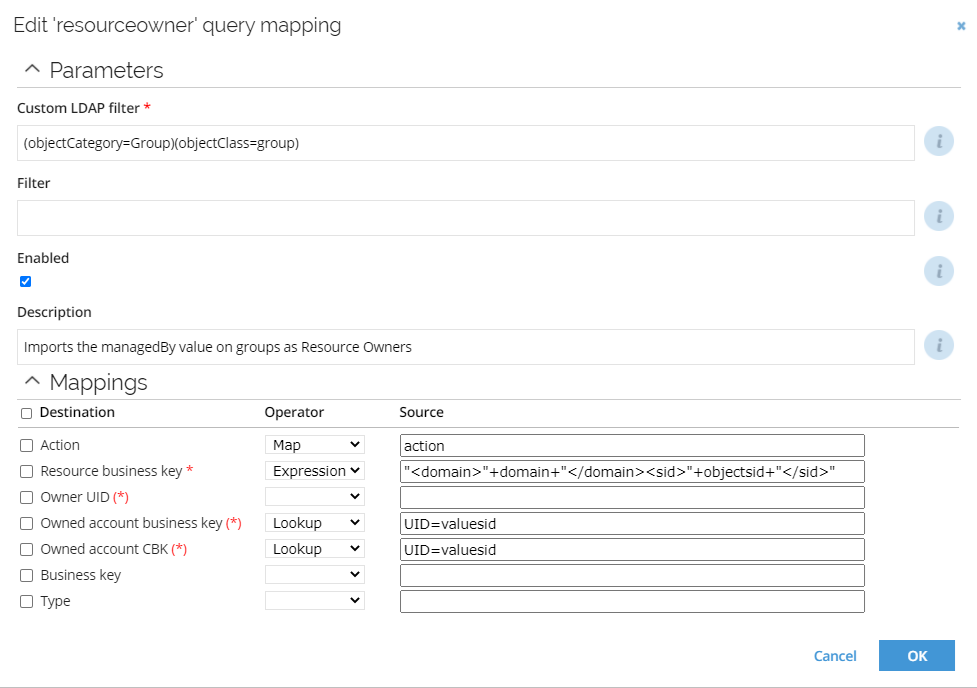
Resource Owner
The managedBy attribute on groups in Active Directory is imported as resource owners in the Data Warehouse. In Active Directory the managedBy can point to a user or to a group, but only users are supported in Omada Identity. The Data Warehouse uses the resolved account user as the resource owner. If the imported account does not have an owner in the Warehouse the information will be ignored.
If your Active Directory does not use the managedBy attribute, or if you do not wish to use this information is Omada Identity, it is recommended to disable/delete this query.
| Parameter | Value |
|---|---|
| LDAP filter | (objectCategory=Group)(objectClass=group) |
| Active Directory | Data Warehouse |
|---|---|
| - | BusinessKey |
| - | OwnerUID |
| "<system>"+BuiltIn.SystemShortName+ "</system><sid>"+objectsid+"</sid>" | Resource_BusinessKey |
| - | Type |
| UID=valuesid | Owned account business key |
| UID=valuesid | Owned account CBK |
If you create a query to import resource owners, it is possible to specify the resource's owner in two ways. You can do it either by directly importing the UID of the identity or by specifying the account from which the resolved owner is imported as a resource owner. When mapping directly to the UID of identity, ensure that identities are already imported to Omada Identity.
When mapping to an owned account, it is possible to either specify the business key of the account or the composed business key. The former should be used if the account is in the same system as the resource and the latter should be used if the account is imported into any of the trusted systems. When the account stems from another system, you should use a Lookup mapping. Below you can find an example from the Active Directory collector.
Advanced settings
| Parameter | Description |
|---|---|
| Resource assignment attribute prefix | A confirmation of group membership ensuring proper resource assignment. Default value is member;. NOTE: If your domain controller uses the 2012 (or 2012 R2) OS version, change member; to member to ensure the correct resource assignment processing. This change is required for backward-compatibility reasons. |
| Timeout (seconds) | Timeout (in seconds) for establishing connection and for requests. Default value is 180. |
| Batch size | A number of objects to retrieve per request when loading missing attributes. Default value is 100. Due to a limitation in Active Directory LDAP request size, it is not recommended to use values greater than 100. |
| Max degree of parallelism | A number of simultaneous requests to send to Active Directory. Default value is 15. Omada recommends to configure the MaxPoolThreads setting in Active Directory to match the value of this parameter. |
| Retry times | A number of retries in case of connection failure or a timeout. Default value is 0. |
| Sleep before next retry (seconds) | Sleep period (in seconds) before a new import retry. Default value is 10. |
| Full import in case of domain controller change | Enable this checkbox to perform a full import in the case if the Active Directory domain controller changes between imports or if there is a risk of high latency replication between Active Directory controllers. In such situations, this option should be enabled to ensure that data is not lost. |
| Full import in case of domain controller change and error | Enable this checkbox to perform a full import in the case if the Active Directory domain controller changes and an import error occurs. |
| Search option scope | Select a search scope. Domain Scope includes ordinary domain objects (default). Phantom Root includes low-level database objects that Active Directory uses for internal management operations. |
| Use standard string format for SID | The collector, by default, imports objectSid as a hexadecimal representation, for example, 01-05-00-00-00-00-00-05-15-00-00-00-1b-74-08-63-d4-51-e0-4b-bb-38-d4-fc-1c-ca-0d-00. Enable this option to use the standard Active Directory format, such as, S-1-5-21-917267712-1342860078-1792151419-50. |
| Perform unfolding | Enable this to unfold the parent-child hierarchy of the resources (such as groups with members of a group). |
Configuring thresholds (optional)
- Click Configure import to open its settings dialog box.
- In the Configure import thresholds window, type a number (integer) in percentage for New objects, Modified objects, and Deleted objects to enable thresholds for the import of objects from this system.
The value for each operation is by default set to 0, which means that no threshold calculations take place for the operation(s) until you change the integer. See Threshold for more information.
Due to technical reasons, data that exceed the import thresholds set in Microsoft Active Directory Connectivity can only be rejected and another import would be required to extract the exceeding data. In such situations, in order to successfully import all the data, you need to raise the value of the import threshold or disable the threshold by setting it to empty.