SAP GRC Relay
The SAP GRC Relay connector is based on the generic SOAP connector and in a provisioning context, SAP GRC Relay connectivity works in the same way as generic SOAP connectivity. However, the connector only relays provisioning tasks (requests) to the external provisioning system.
Out of the box, the SAP GRC Relay connector is capable of creating Requests and Request Line Items. When the job is relayed to SAP GRC, the connector queries and determines the job status based on the Request state, as well as, task status based on the Request Line Item state. Thanks to that capability, it is possible to recognize which Requests are completed, failed, pending, and partially completed.
As the basic prerequisite for the SAP GRC connectivity, you need to onboard the SAP backend system.
Supported objects and operations
The SAP GRC Relay Connectivity allows you to create and relay request and request line item objects to SAP GRC, and indirectly manage access rights.
| Resource | Possible operations |
|---|---|
| Request | Create, read |
| Request Line Item | Create, read |
Supported scenarios:
Create User
When an Identity is required to have an SAP Account as result of an access request or policy a request is sent to SAP GRC.
Change User
When Accounts Master data is required to be changed a request is sent to SAP GRC.
Delete User
When SAP Accounts is required to be removed a request is sent to SAP GRC.
Lock/Unlock User
When an Account must be locked or unlocked a request is sent to SAP GRC.
Assign/unassign Role
Roles to be assigned or unassigned, as a result of an Identity calculation, will be sent in a request to SAP GRC.
If a role assignment is rejected in SAP GRC, the corresponding resource assignment in Omada Identity is set to obsolete and Validto set to date of rejection in SAP GRC.
| Role Types | Provisioning | Reconciliation |
|---|---|---|
| Single Roles | Yes | Yes |
| Composite Roles | Yes | Yes |
| Business Roles (exist only in SAP GRC) | Yes | No |
Bear in mind that the connector imports all roles, both single and composite, just as roles. During the import, the SAP GRC connector does not register which roles are single and which are composite.
Assumptions:
- Request in Omada Identity are on Business Role Level and Single Role Level
- Decision in SAP GRC must be on the requested role level
- Requests in SAP GRC must not be extended (cannot add) additional roles
- There must be clear yes/no decision
- SoD Check shall be handled in case of policy and direct assignments
- Provisioning can still be done by SAP GRC
- Changes in SAP GRC ruleset will not affect Omada Identity
- Post Validity MUST be set on resource type that is a part of SAP GRC scenario – that is, 10 days
Minimum required permissions
You need to have access to the SAP GRC system.
The SAP GRC administrator must provide a user account with appropriate access to call the SAP GRAC web services, create requests, and query for status on these. In addition, it is also required to have access to user management in SAP GRC itself if it is a part of the scope for SAP user provisioning.
SAP provides several standard roles for SAP GRC Access Control. If you search for SAP_GRAC* in transaction PFCG within SAP GRC you will find 27 single roles related to SAP GRC Access Control, we recommend assigning SAP_GRAC_ACCESS_REQUEST_ADMIN to the user account used by the relay connector and choose the User Type Service.
SAP GRC will already be configured with connectivity to the SAP backend systems in order to perform User Provisioning.
Implementation notes
The following image presents the process flow of SAP GRC provisioning performed within Omada Identity.
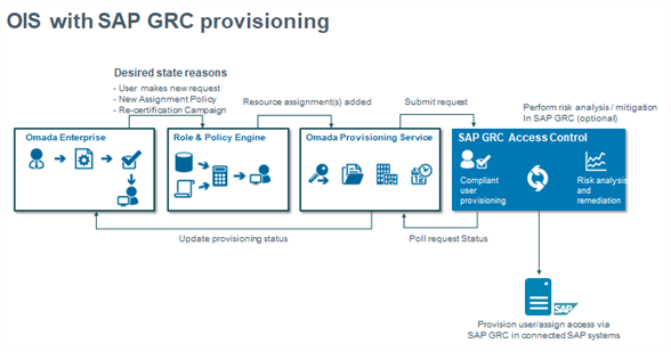
The following presumptions are implied for the correct SAP GRC configuration for User provisioning:
- User provisioning into the SAP backend systems must be performed by SAP GRC.
- Reconciliation for the Requests and Request Line Items is done by the SAP GRC OPS Relay Connector.
- Reconciliation of the actual assignments in the SAP backend system is performed by the SAP collector.
Network requirements
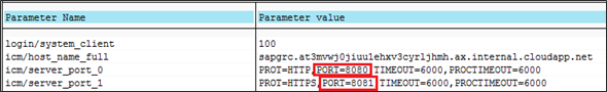
The connector requires the port to the SAP GRC web services to be open. The TCP/IP ports used by the SAP system are customer specific, typically the SAP Basic administrator can provide this information. The port numbers used for http and https are maintained in the SAP instance profile, which is maintained via transaction code RZ10. The parameter names are:
- icm/server_port_0
- icm/server_port_1
Example of port numbers used by SAP application server shown below.
Prerequisites
Target system configuration
The standard SAP GRC web services for Access Control must be enabled by the SAP GRC administrator.
-
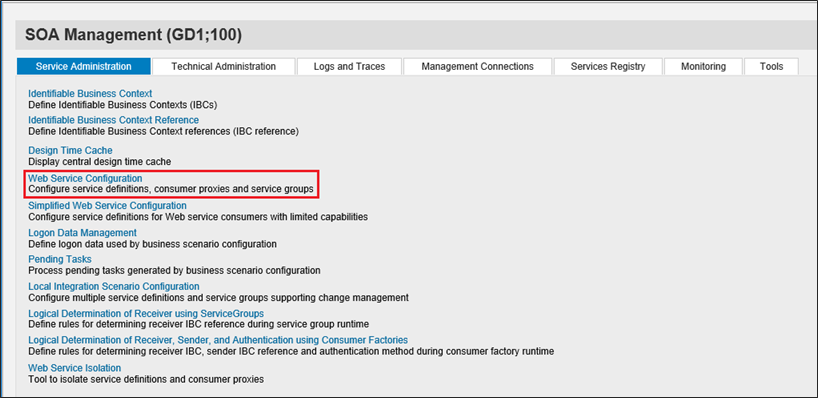
Launch transaction code SOAMANAGER and select Web Service Configuration
-
Search for
GRAC*.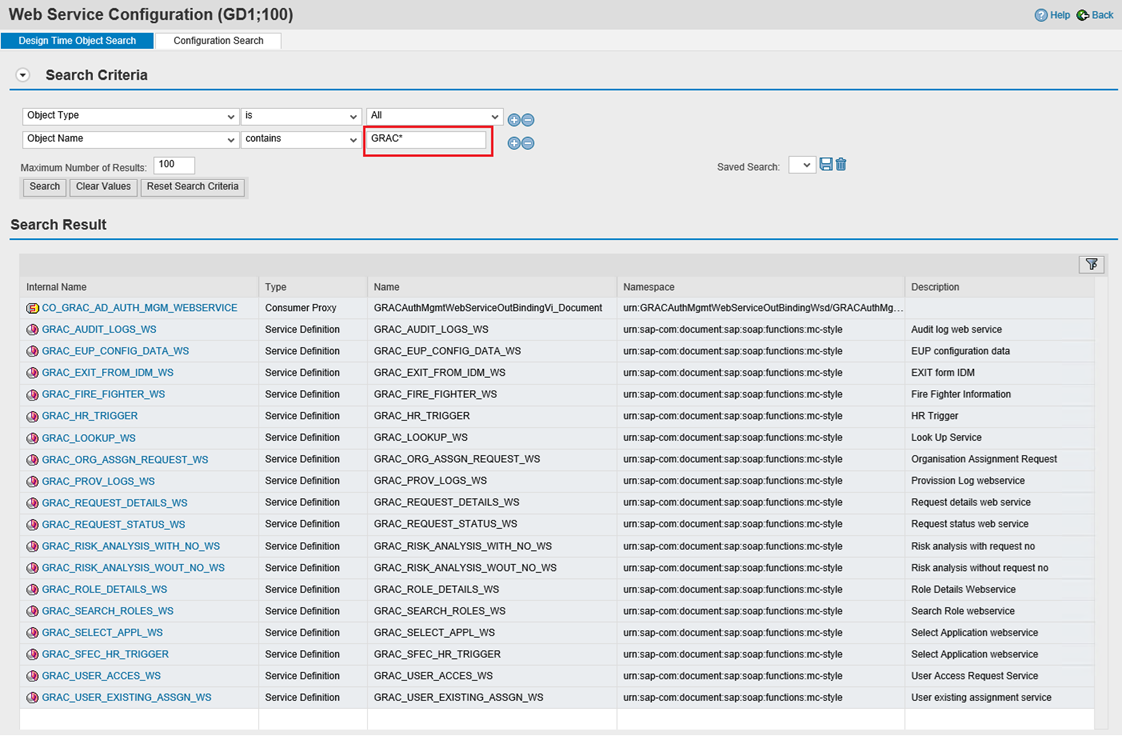
The below services are used by the Omada Identity SAP GRC Relay Connector, verify the below services are configured:
- GRAC_USER_ACCESS_WS
- GRAC_REQUEST_DETAILS_WS
In Transport Level Security, the SAP GRC administrator determines if SSL is required, which must then be selected in the relay connector as well under Webservice settings. The relay connector is only supporting userid/password, which must be selected under Transport Channel Authentication. The following screenshot shows the above-mentioned configuration in SAP GRC.
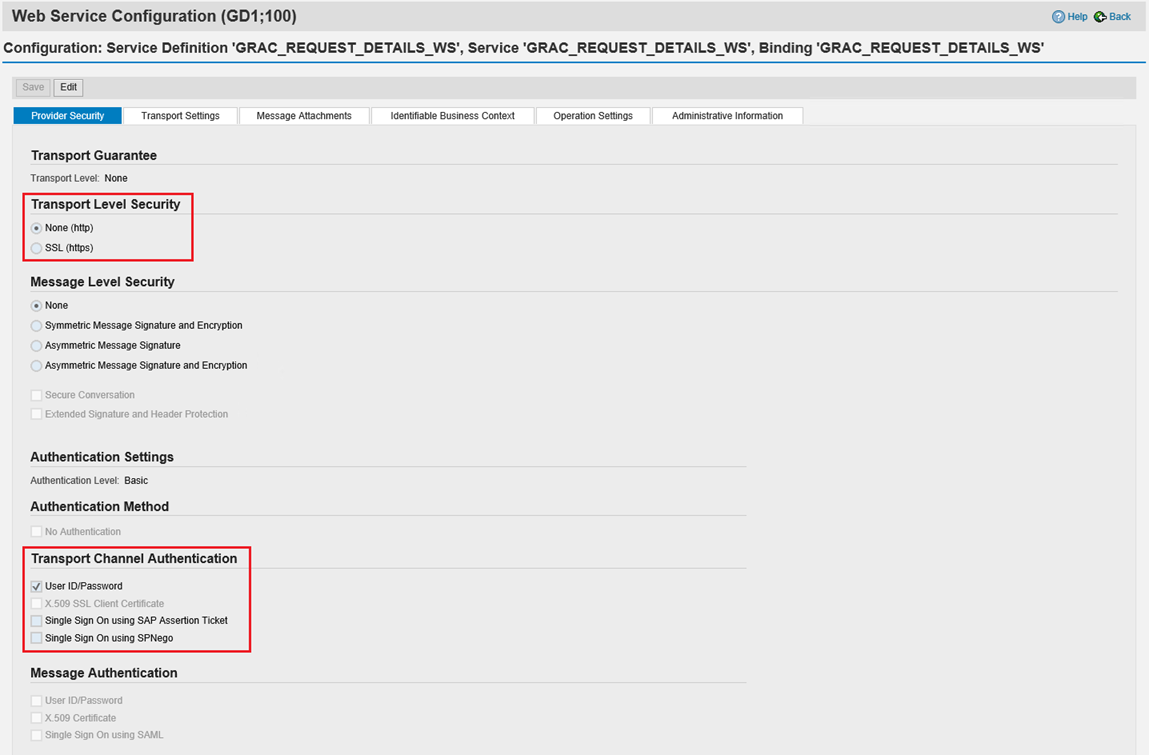
SAP GRC user setup
For the SAP GRC Relay Connector to work correctly, you need to configure SAP GRC to authorize the Omada Identity user to log in and access the SAP GRC web services as mentioned in the section Minimum required permissions.
SAP GRC configuration
Configuration of SAP GRC is done via transaction SPRO, where you can enter the SAP Reference IMG (Implementation Guide) by clicking the icon or by pressing F5.
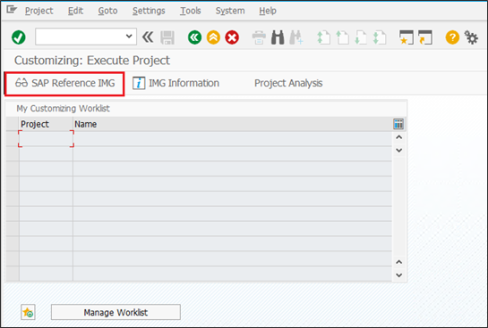
In the IMG go to/expand Governance, Risk and Compliance > Access Control > User Provisioning.
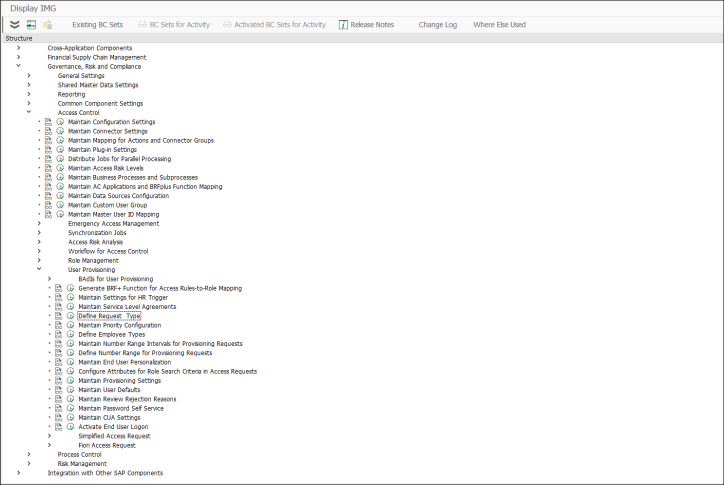
Request Type
We recommend creating a new Request Type for the Omada -> SAP GRC integration and allow all actions to be executed for this Request Type.
-
Click to enter Define Request Type.
-
Select New Entries.
-
Provide the details:
- Description = free text
- Active = True
- Process ID = SAP_GRAC_ACCESS_REQUEST
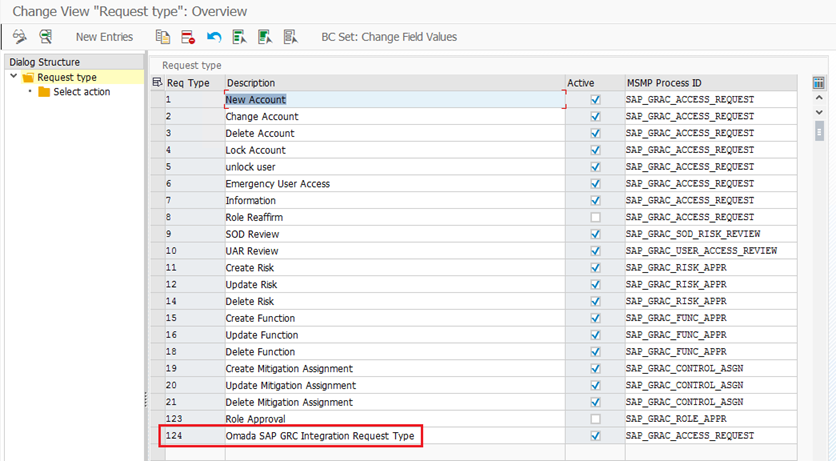
-
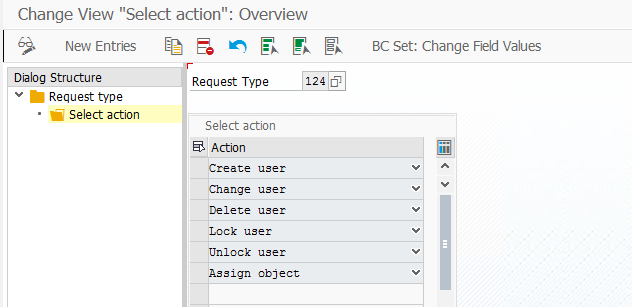
Select the Request Type and double-click on Select action.
-
Add all the supported actions as shown below.
-
Save and exit.
Initialization system
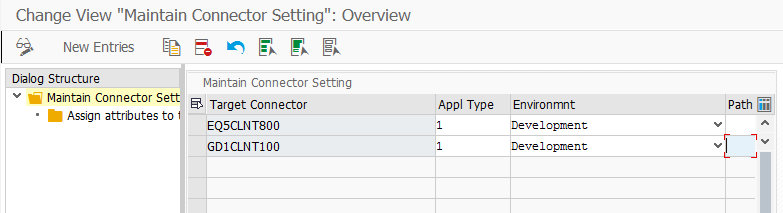
The list of connected systems in SAP GRC is found in the Access Control section under Maintain Connector Settings in the IMG, the SAP GRC administrator can inform about the connector name for each SAP backend system in scope.
Find example of connector names in below screenshot.
Request business process
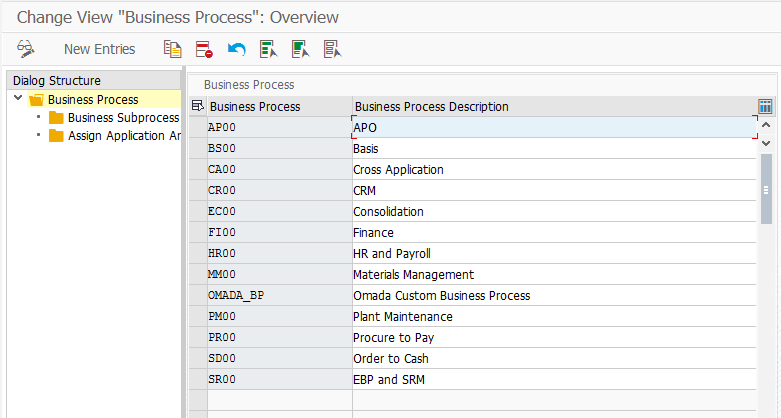
The Business Process is maintained in the Maintain Business Processes and Subprocesses section under Access Control in the IMG.
SAP provides a number of predefined values processes but allows for custom values to be created. Per default Business Process is a mandatory field in the request but this can be changed in the setting Maintain End User Personalization.
Request reason
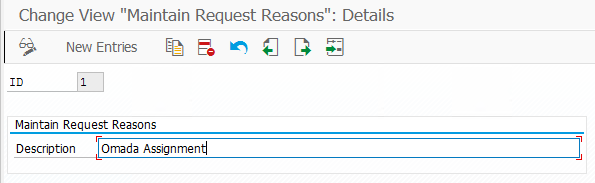
The Request Reason is maintained in the Maintain Request Reasons section under Simplified Access Request in the IMG, we recommend creating a Request Reason specific for the requests originating from Omada Identity, find example below.
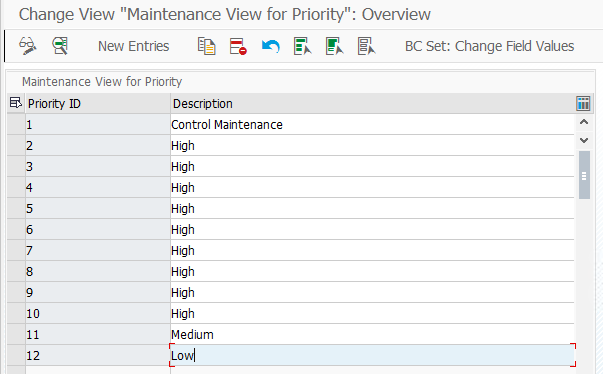
Request priority
The Request Priority is maintained in the Maintain Priority Configuration section under User Provisioning in the IMG, create a new priority or use any of the standard provided.
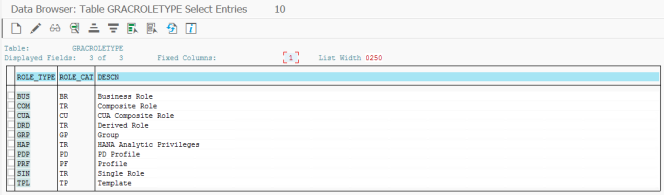
Role Type
In the Task Mapping for role assignment the Role Type must be provided. It is 3 character based on table GRACROLETYPE and from column ROLE_TYPE, see below for default configuration.
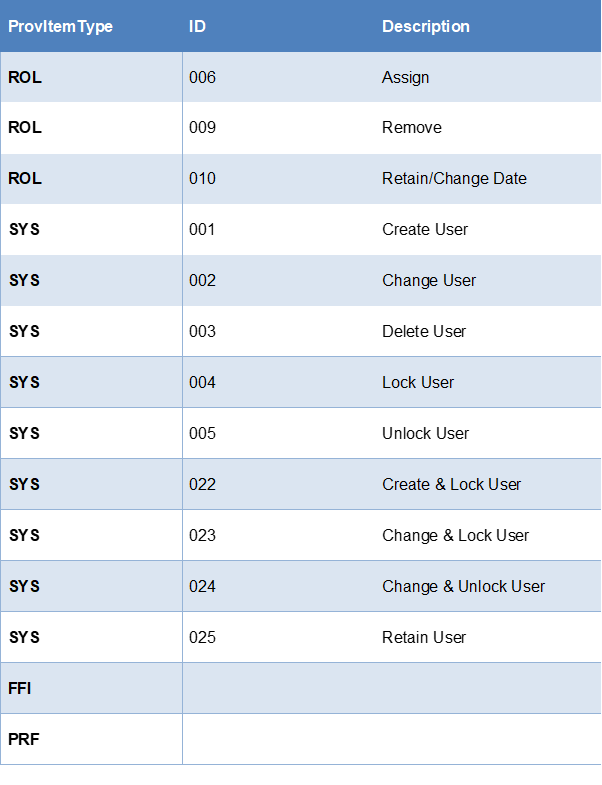
ProvItemType and its relation to ProvAction
Used in the Task Mapping.
A-Attributes and Attribute Sets
Importing role types
-
To create a new set property SAP Role Type, add the values:
- BUS – Business Role
- COM – Composite Role
- SIN – Single Role
-
Add a new property to DOT Resource. Add compositeRole as an extension attribute for SAP Roles in System Onboarding Queries and Mappings.
-
Extend ODW to Portal mapping for Resources to include a mapping from compositeRole to SAP Role Type.
-
Create new Attributes:
- ValidTo
- ValidFrom
- SAP Role Type
-
Create new Attribute Set for SAP User:
- ValidTo
- ValidFrom
- First Name
- Last Name
-
Create new Attribute Set for SAP Role:
- ValidTo
- ValidFrom
- SAP Role
- Type
- First
- Name
- Last Name
-
Assign attribute set SAP User to resource type(s) SAP User/SAP Account.
-
Assign attribute set SAP Role to resource type(s) SAP Role.
-2ea44f)