Data provisioning
The SSH data provisioning (connector) executes an SSH command, and then checks if the returned code (or, optionally, the result text) matches the expected value.
You can use other commands than the built-in system commands. It can be any kind of command available in the target system (for example, a Python script).
There are four basic properties in the SSH data provisioning process:
- Command - The command to be executed.
- Parameters - The parameters for the command.
- SuccessRegex - (optional) the expected output from the command (regular expression).
- ExitStatus - (optional) the expected code returned from the command. For most commands it returns
0.
Commands and parameter values may contain additional parameters inside curly brackets (for example adduser {Username}). These additional parameters can be provided in the separate object properties. Omada recommends using this approach rather than creating long commands without parameters. It enhances readability, provides an additional validation (if the property value is missing, the task fails), and ensures security.
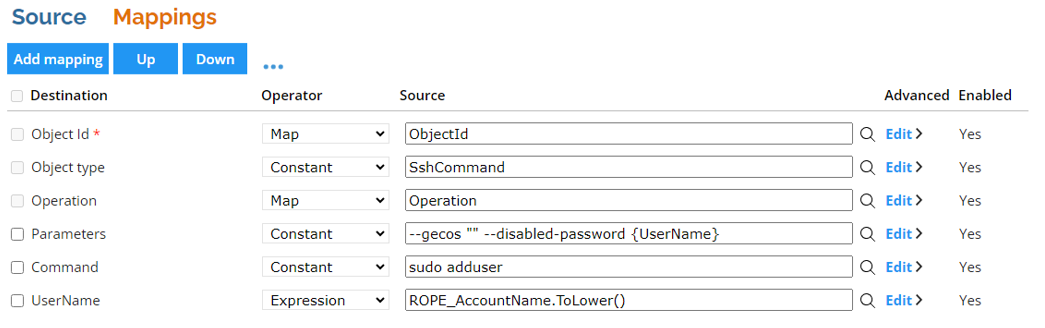
Additional properties that are in the provisioning task, but are not used in the command and its parameters, are ignored.
Security principles
Use the SSH data import (connector) with caution. Building commands, which contain input coming from the users, may be vulnerable to the command injection attacks. Review the following recommendations to ensure security:
- Don't use the administrator account to connect via SSH. Use user accounts with permissions to execute scripts/commands required for the provisioning only.
- Avoid using source attributes which can be modified by users. Avoid using free-form data entry fields (such as description).
- Use parametrized queries.
Use security regular expressions:
-
You can define security regex for each parameter. It can be done by defining additional property value with a postfix
-securityRegex(for example, to validate theusernameparameter, there should be an additional propertyusername-securityRegex). If the username parameter should not contain any single quotes, the value of this property can be:^[^']*$". If the security check fails, the provisioning task fails as well. -
You can define a global property or object detail
ParameterSecurityRegexapplied to all parameters. If the parameter has a dedicated security regex,ParameterSecurityRegexis ignored. If the security check fails, the provisioning task fails as well. -
You can define a global property or object detail
CommandSecurityRegexapplied to the final command with parameters. If the security check fails, the provisioning task fails as well.
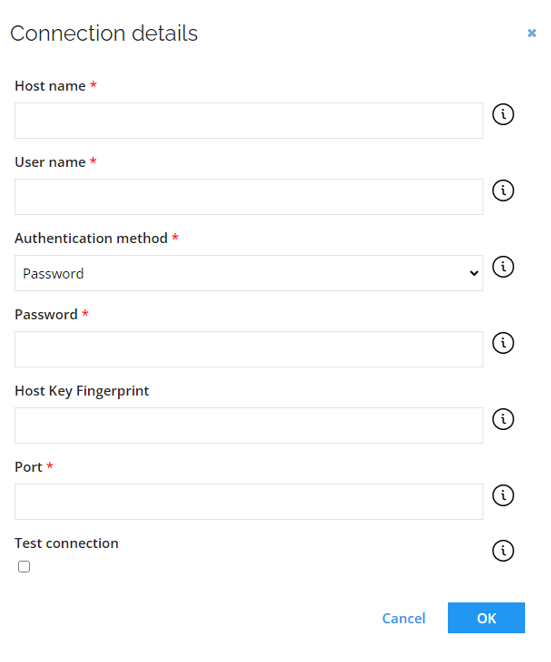
Connection details
| Parameter | Description |
|---|---|
| Host name | Name or IP address of the host. |
| User name | User name used to log to target machine. |
| Authentication method | Authentication method to use for the SSH server. |
| Host Key Fingerprint | Provide the host key fingerprint used for the host key validation. If the value is not provided, validation is skipped. MD5 and SHA256 fingerprints are supported. Format: algorithm:fingerprint Example: SHA256:jlDPKCCRr1TkufVsZJf02ejXNQ7RB/vg09uGwKeSwnU |
| Port | Provides the communication port. Default value is 22. |
| Test connection | Select this option to test the connection to the target system with the connection details you have provided. If the data is correct, the connection will be established. |
Authentication methods
The following authentication methods are provided:
- Password: Used to connect to the SSH server with the password authentication method. If the server is configured with a single method authentication, the server accepts this method, and the password is correct, the connection will be established successfully. If the server is configured with the multifactor authentication, the connection will not be established.
- Password and Private Key: Used to connect to the SSH server with the password and private key authentication methods. If the server is configured with a single method authentication, the connection will be established if at least one of the two methods works successfully. If the server is configured with the multifactor authentication, the connection will be established only if both methods work successfully.
- Private Key: Used to connect to the SSH server with the private key authentication method. If the server is configured with a single method authentication, the server accepts this method, and the private key is correct, the connection will be established successfully. If the server is configured with the multifactor authentication, the connection will not be established.
Sample data model
<connectorDataModel
xmlns="http://schemas.omada.net/ops/2015/ConnectorDataModelML"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<properties>
<!--SshCommand-->
<property name="Command" dataType="stringType" />
<property name="Parameters" dataType="stringType" />
<property name="UserName" dataType="stringType" />
<property name="SuccessRegex" dataType="stringType" />
<property name="ExitStatus" dataType="stringType" />
</properties>
<objects>
<object name="SshCommand">
<objectDetails>
<objectDetail name="ParameterSecurityRegex" value="^[^&]*$" />
</objectDetails>
<objectProperties>
<objectProperty>Command</objectProperty>
<objectProperty>Parameters</objectProperty>
<objectProperty>UserName</objectProperty>
<objectProperty>SuccessRegex</objectProperty>
<objectProperty>ExitStatus</objectProperty>
</objectProperties>
</object>
</objects>
</connectorDataModel>