Data import
Connection details
If the addresses for query and for entities are the same, you must leave the Entity root and Query address fields blank or empty. Instead, enter the full address in the Base URL field.
| Parameter | Description |
|---|---|
| Base URL | This field is optional. You can specify the Base URL of the service. When you specify a Base URL, this URL will be used for all defined queries if these do not specify a full URL of their own. The Base URL is part of the data connection data, and the Base URL should not be transported between environments. You must enter the URL that ends before the SCIM entity’s name. For example, the URL for users is http://10.16.2.1/scim/users and the base URI is http://10.16.2.1/scim. |
| Authentication type | Choose the type of authentication to use for theREST system. The available options are: - AWS Signature – adds authentication information to the HTTP header of Amazon Web Services requests. - Basic – uses Base64-encoded string that contains a username and password. - Negotiate – automatically selects between NTLM and Kerberos, depending on availability. - NTLM – NT LAN Manager authentication uses Windows credentials to transform the challenge data. - Digest – a challenge-response authentication that uses a nonce which is a string of random data. - Kerberos – uses ticket granting system for authenticating users. - OAuth2 Custom - authentication server provides token required for the authentication request. - OAuth2 Client Credentials – uses access token. - OAuth2 Password – uses user’s credentials to acquire access token. - OAuth2 JWT – uses JSON web token. - OAuth2 SAP Username and password - uses SAP Username and password - OAuth2 client credentials using basic authentication - uses SAP Username and password. - OAuth2 Static Token - uses statically generated bearer token. Depending on the type of authentication that you choose to use with the system, you may see more or fewer settings appear in the dialog box. |
| User | This is the user name. |
| Password | This is the password. Each time you make a change to any of the settings in the Connection details dialog box, you must provide your password again. |
| Domain | This field is optional. Here, you can specify the domain name for the user. |
| Headers | This field is optional. Here, you can provide JSON document specifying custom headers. For example:sql{"Request": {"Accept": " text/html","content-type": "application/json","SomeCustomHeaderWithValue": "custom value","SomeCustomHeaderWithoutValue": null}} |
| Include certificate | If selected, a client certificate will be attached to the HTTP requests. Three additional parameters are required: - Certificate (in the PEM format) -----BEGIN CERTIFICATE----- <contents> -----END CERTIFICATE----- - Private Key (in the PEM format) -----BEGIN PRIVATE KEY----- .... -----END PRIVATE KEY----- - Passphrase for private key (optional, use it if the private key was created with the passphrase ) |
| Auth request body | This field applies only to OAuth2 Custom authentication option. Raw body of the request sent to authentication server to get the access token. Sensitive values should be replaced with the placeholders starting with #SECURE. |
| Placeholder values | Key value pairs, one per line, for sensitive data used in the request body to get the access token. Key names should start from #SECURE. #SECURE1=MySecurePass123! |
| Auth request content type | This field applies only to OAuth2 Custom authentication option. Content type of the request sent to authentication server to get the access token. |
| Authentication server response format | This field applies only to OAuth2 Custom authentication option. The available options are: - Access token only - JSON - Other - XML |
| Access token Location | Required field for OAuth2 Custom if the Authentication server response format setting has value other than Access token only configured. Location of the access token in the response. Depending on the format, different kind of information is expected in this field: - property name if it is JSON - XPath if it is XML - regular expression with group if it is other, unknown format. |
| Token endpoint | This field applies only to OAuth2 authentication options. Enter the URL used to exchange an authorization grant for an access token. |
| Client ID | This field applies only to OAuth2 authentication options. Enter the client registered with the service. |
| Client secret | This field applies only to OAuth2 authentication options. Enter the generated secret for the Client ID. |
| OAuth static token | This field applies only to OAuth2 Static Token authentication option. Enter a statically generated bearer token. The value will be encrypted upon storage. |
| OAuth static token type | Provide a custom keyword that will be supplied in front of the static token, for example, _SSWS_ for OKTA or _AFAS_ for Afas integration. If the field is left blank, the default Bearer value is used. |
| Resource | This field is optional. Here, you can specify the Resource for which authorization will be granted. |
| JWT Encryption algorithm | This field applies only to OAuth2 JWT authentication options. Select the encryption algorithm used when signing the token. For example, RSASSA-PKCS1-v1_5 using SHA-256 (RS256) |
| JWT Type | This field applies only to OAuth2 JWT authentication options. Enter a JWT Type (Header parameter) |
| JWT Public key ID | This field applies only to OAuth2 JWT authentication options. Enter a public key ID for signing the JWT (Header parameter) |
| JWT Issuer | This field applies only to OAuth2 JWT authentication options. Enter a JWT Issuer claim. |
| JWT Subject | This field applies only to OAuth2 JWT authentication options. Enter a JWT Subject claim. |
| JWT Audience | This field applies only to OAuth2 JWT authentication options. Enter a JWT Audience claim. |
| JWT Expiration time | This field applies only to OAuth2 JWT authentication options. Set a JWT Expiration time. |
| JWT Additional claims | This field applies only to OAuth2 JWT authentication options. Enter a JWT Additional claims in the format: key1,value1;key2,value2;... |
| JWT Private key (PEM format) | This field applies only to OAuth2 JWT authentication options. Enter a JWT Private key is in the PEM format:-----BEGIN PRIVATE KEY----- .... -----END PRIVATE KEY----- or -----BEGINENCRYPTED PRIVATE KEY----- .... -----END ENCRYPTED PRIVATE KEY-----and then Passphrase for Private Key needs to be provided. |
| JWT Passphrase for private key | This field applies only to OAuth2 JWT authentication options. Enter a Passphrase for the provided Private key. |
| Username | This field applies only to OAuth2 client credentials using basic authentication authentication option. Provide the SAP username for a SAP Cloud system like SAP Cloud Identity Authentication Service (IAS). |
| Password | This field applies only to OAuth2 client credentials using basic authentication authentication option. Provide the SAP password for a SAP Cloud system like SAP Cloud Identity Authentication Service (IAS). |
| Test connection | Enable this setting to allow the system to check if the connection details are correct. |
Mappings
When you onboard a system based on SCIM 2.0, a number of default queries and mappings are set up:
- Accounts - users are imported into Omada Identity as accounts.
- Resource - groups are imported into Omada Identity as resources with the resource type "SCIM Group".
- Resource Assignment - user memberships in groups are imported into Omada Identity as resource assignments.
- Resource Parent/Child - group memberships in other groups are imported into Omada Identity as resource parent/child relationships.
When configuring mappings (in OSI SCIM 2.0 connectivity) the dot character "." and the colon character ":" are illegal and are by default removed from the SCIM properties. These changes mean that SCIM property urn:ietf:params:scim:schemas:cyberark:1.0:User_cyberarkUserType in the Omada Identity mapping should have the form urnietfparamsscimschemascyberark10User_cyberarkUserType.
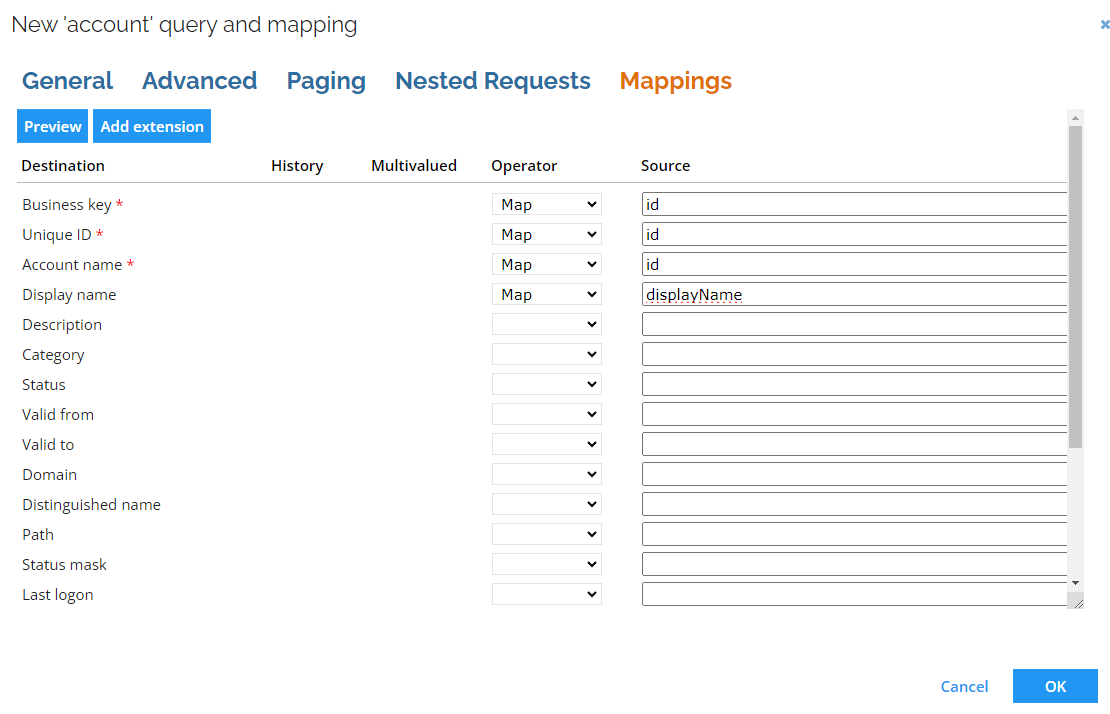
Since the release of the Omada Identity v14.0.7 and its updated version of REST-based collectors, arrays of source values cannot be mapped to a destination other than extension. An example of such an array of values might look like the following JSON document:
{
"itemsPerPage": 10,
"startIndex": 1,
"schemas": [
"urn:ietf:params:scim:api:messages:2.0:ListResponse"
],
"totalResults": 1,
"Resources": [
{
"userName": "slobij3",
"externalId": "slobij",
"id": "d0ba43d0-d939-443c-b5f2-084e118afaa7",
"name": {
"formatted": "IJsbrand Slob",
"familyName": "IJsbrand Slob",
"givenName": "IJsbrand"
},
"emails": [
"user1@omada.net",
"user2@omada.net",
"user3Omada.net""
],
}
]
}
In the previous version of REST-based collectors, the last email address would be mapped to a destination.
The collector performs a get request on a specific URL. The final URL is created by adding the Query URL to the base URL. The Query URL must contain at least the name of the entity that you would like to collect data from. The schema for the entity confirms that properties are present in a specific entity and describes how to access them.
You must investigate the schema for the response as well as the schema for each of the entities that comes out of the SCIM server. You can do this by reading the documentation for a specific SCIM server or by running a manual get request.
Mapping of resource owners
If you create a query to import resource owners, it is possible to specify the resource's owner in two ways. You can do it either by directly importing the UID of the identity or by specifying the account from which the resolved owner is imported as a resource owner.
When mapping directly to the UID of identity, ensure that identities are already imported to Omada Identity.
When mapping to an owned account, it is possible to either specify the business key of the account or the composed business key. The first one should be used if the account is in the same system as the resource. The second one should be used if the account is imported into any of the trusted systems.
When the account stems from another system, you should use a Lookup mapping.
Advanced configuration
| Parameter | Description |
|---|---|
| Perform unfolding | Enable this setting to unfold users’ access to resources assigned through group-level policies. Such resources will be visible as indirect assignments. |
| Append URL parameter(s) | Optionally, enter any additional query parameters which should be added to any of the queries defined under Queries and Mappings. The value must be entered following standard of the service, for example: parameter1=value¶meter2=value The collector ensures correct formatting of the entire URL. |
| Security protocol | Choose a security protocol to use for an HTTPS connection (TLS 1.2). |
| Paging mechanism | Select the type of paging the service uses.Services may result large datasets and will return data in chunks.The SCIM 2.0 collector is based on REST and offers the following options: - None: Select this option if the service offers no paging and all data is returned. - Paging URL: Use this option if the response contains a field with a URL for the next page. - URL parameters: Use this option if the paging must be specified as URL parameters. |
| Marker element | Type in the name of the response element, whose value will be used in the subsequent pagination requests to obtain the next set of items if the pagination results are truncated. |
| Marker parameter | Type in the name of the parameter that will be used in the subsequent pagination requests, with the Marker element value, to obtain the next set of items. |
| Paging URL field | Use this option if the response contains a field with a URL for the next page. When Paging mechanism is selected as Paging URL, use the Paging URL field to specify the JSON field in the response that contains the URL for the next page of data.The collector will continue querying the service until this field is empty. |
| URL parameters | Use this option if the paging must be specified as URL parameters. When Paging mechanism is selected as URL parameters, use the URL Parameters field to enter the parameters that must be appended to the query to get the next page of data. |
| Starting index | It is the index of the record returned as the first one on the first page of the response. The default value of this is index is 1. |
| Total field | Enter here the JSON field in the response that indicates the total amount of records. This field is optional. If the field is left empty, the service will be called until an empty result set is returned. |
| Timeout in seconds | Specify how long the collector should wait for a response of the AWS service. The default value is set to 3600 seconds (1 hour). |
| Row count per batch | Set the number of objects that will be collected and staged as a batch when paging is implemented in the collector. The default value is 100000. Applying a low value, for example 50 or 500, to this setting may result in extended import time. |
Configure thresholds
The Configure thresholds function allows you to set the amount of changes that cannot be exceeded, relevant to the last import. In the Configure import thresholds view, type a number (integer) in percentage for New objects, Modified objects, and Deleted objects to enable thresholds for the import of objects from this system. The value for each operation is by default set to 0, which means that no threshold calculations take place for the operations until you change the integer.
For all .NET-based collectors, thresholds are calculated in the following relation:
-
If the system category is set to Identity data, the thresholds are calculated.
-
If the system category is set to Access data, the thresholds are calculated.
-
If the system category set to Both, the thresholds only apply to Access data, that is, Accounts, Resources, and ResourceAssignments.