Data import
Connection details
| Parameter | Value |
|---|---|
| Base URL | https://{yourtenant}/scim/v2/ |
| Authentication type | OAuth2 Client Credentials |
| Token endpoint | https://https://{yourtenant}/oauth2/token/{yourappid} |
| Client ID | Your client id |
| Client Secret | Your client secret |
| OAuth token type | Bearer |
| Scope | SCIM |
| Test connection | Select the checkbox |
| Test query | Users |
Queries and mappings
Users - Accounts
Parameters:
| Tab | Parameter | Value |
|---|---|---|
| General | URL | Users |
| General | Collection | Resources |
| Advanced | http verb | GET |
Mappings:
| Destination | Operator | Source |
|---|---|---|
| Business key | Map | id |
| Unique ID | Map | userName |
| Account Name | Map | userName |
| Display Name | Map | displayName |
| Status | Expression | active ? "Active" : "Inactive" |
| Distinguished name | Map | id |
Groups – Resources
Parameters:
| Tab | Parameter | Value |
|---|---|---|
| General | URL | Groups |
| General | Collection | Resources |
| Advanced | http verb | GET |
Mappings:
| Destination | Operator | Source |
|---|---|---|
| Business key | Map | id |
| Security resource business key | Map | id |
| Name | Map | displayName |
| Category | Constant | Group |
| Type | Constant | CyberArk Privileged Cloud - Group |
| Display name | Expression | urnietfparamsscimschemascyberark10Group_description != null ? urnietfparamsscimschemascyberark10Group_description : displayName |
| Short name | Map | id |
| Logical Key | Map | displayName |
| Description* | Map | id |
*Do not use the Description field on resources, as Omada uses this field to prevent duplication during resource import.
Containers – Resources
Parameters:
| Tab | Parameter | Value |
|---|---|---|
| General | URL | Containers |
| General | Collection | Resources |
| Advanced | http verb | GET |
Mappings:
| Destination | Operator | Source |
|---|---|---|
| Business key | Map | id |
| Security resource business key | Map | id |
| Name | Map | displayName |
| Category | Constant | Group |
| Type | Constant | CyberArk Privileged Cloud - Container |
| Display name | Map | displayName |
| Short name | Map | id |
| Logical Key | Map | displayName |
| Description* | Map | id |
| Location | Map | urnietfparamsscimschemascyberark10Safe_location |
| Supportolac | Map | urnietfparamsscimschemascyberark10Safe_supportOLAC |
*Do not use the Description field on resources, as Omada uses this field to prevent duplication during resource import.
Rights – Resources
Parameters:
| Tab | Parameter | Value |
|---|---|---|
| General | URL | ContainerPermissions |
| General | Collection | Resources |
| Advanced | http verb | GET |
Mappings:
| Destination | Operator | Source |
|---|---|---|
| Business key | Map | rights |
| Security resource business key | Map | rights |
| Name | Map | rights |
| Category | Constant | Permission |
| Type | Constant | CyberArk Privileged Cloud - rights |
| Short name | Map | rights |
Privileged Data – Resources
Parameters:
| Tab | Parameter | Value |
|---|---|---|
| General | URL | PrivilegedData |
| General | Collection | Resources |
| Advanced | http verb | GET |
Mappings:
| Destination | Operator | Source |
|---|---|---|
| Business key | Map | id |
| Security resource business key | Map | id |
| Name | Map | name |
| Category | Constant | Group |
| Type | Constant | CyberArk Privileged Cloud - Privileged Data |
| Display Name | Map | name |
| Short name | Map | id |
| Logical Key | Map | name |
| Description | Map | description |
| privilegeddatatype | Map | type |
| safe | Map | urnietfparamsscimschemascyberark10PrivilegedData_safe |
| propertieskey | Map | urnietfparamsscimschemascyberark10PrivilegedData_properties_key |
Users to Containers (Safes) – Resource Assignments
Parameters:
| Tab | Parameter | Value |
|---|---|---|
| General | URL | ContainerPermissions |
| General | Collection | Resources |
| Advanced | http verb | GET |
Mappings:
| Destination | Operator | Source |
|---|---|---|
| Resource business key | Expression | user_value != null ? container_value : null |
| Account – business key | Expression | user_value != null ? user_value : null |
| Description | Expression | container_display + " -> user: " + user_display |
| rights | Map | rights |
| assignmentId | Constant | id |
Users to Groups (Roles) – Resource Assignments
Parameters:
| Tab | Parameter | Value |
|---|---|---|
| General | URL | Groups |
| General | Collection | Resources |
| General | Filter | type != "Group" |
| Advanced | http verb | GET |
Mappings:
| Destination | Operator | Source |
|---|---|---|
| Resource business key | Map | id |
| Account – business key | Expression | (members_ref != null && members_ref.ToString().Contains("Group")) ? null : members_value |
| Description | Expression | displayName + " -> user: " + members_display |
Groups assigned to Groups – Resource parent/child
Parameters:
| Tab | Parameter | Value |
|---|---|---|
| General | URL | Groups |
| General | Collection | Resources |
| Advanced | http verb | GET |
Mappings:
| Destination | Operator | Source |
|---|---|---|
| Indirect | Constant | false |
| Parent resource business key | Expression | (members_ref != null && members_ref.ToString().Contains("Group")) ? id : null |
| Child resource – business key | Expression | (members_ref != null && members_ref.ToString().Contains("Group")) ? members_value : null |
Privileged data assigned to Containers – Resource parent/child
Parameters:
| Tab | Parameter | Value |
|---|---|---|
| General | URL | Containers |
| General | Collection | Resources |
| Advanced | http verb | GET |
Mappings:
| Destination | Operator | Source |
|---|---|---|
| Indirect | Constant | false |
| Parent resource business key | Expression | (privilegedData_ref != null) ? privilegedData_value : null |
| Child resource – business key | Expression | (privilegedData_ref != null) ? id : null |
Containers assigned via Groups – Resource parent/child
Parameters:
| Tab | Parameter | Value |
|---|---|---|
| General | URL | ContainerPermissions |
| General | Collection | Resources |
| Advanced | http verb | GET |
Mappings:
| Destination | Operator | Source |
|---|---|---|
| Indirect | Constant | false |
| Parent resource business key | Expression | group_value != null ? container_value : null |
| Child resource – business key | Expression | group_value != null ? group_value : null |
Account rules
The CyberArk Privileged Cloud connectivity includes the ownership and classification account rules.
Ownership rule
The account owner is set to the identity where the Identity's unique ID value of the identity matches the Account UID value of the account.
| Field | Value |
|---|---|
| Type | Identity lookup |
| Join reason | Exact Match |
| Account attribute | Account UID |
| Identity attribute | Identity’s unique ID |
Classification rule
If an account with the account attribute Identity join reason equals Exact Match, the account type is set to Persona.
| Field | Value |
|---|---|
| Account type | Personal |
| Scope attribute | Identity join reason |
| Scope operator | Equals |
| Scope value | Exact Match |
Before enabling provisioning and after the initial import, perform the following actions:
RoPE configuration
-
Open the RoPE configuration file:
- On-prem:
\Omada Identity Suite\Role and Policy Engine\Service\ConfigFiles - Cloud: In the Cloud Management Portal, navigate to Environments. In the environment row, from the drop-down menu, select Configure. Choose the RoPE configuration tab.
- On-prem:
-
Add the following lines under the Attribute Value Resolver extension (change the key value in case you already have that specific key defined):
<add key="5" extraInfo="CyberArk Privileged Cloud - Container" name="assignmentId" value="CYBERARK_ASSIGNMENT_ID" />
Events Definition
For efficient resource provisioning (covering groups, containers and privileged data), create event definitions that trigger create and delete operations.
CyberArk Container and Groups - Create
-
In Omada Identity, go to Setup > Administration > Process configuration > Event definitions. Click New.
-
Enter the following details:
- Name: Provision CyberArk Container (Safe) and Groups
- Description: When a new resource of type CyberArk Privilege Cloud - Container or CyberArk Privilege Cloud - Group is created, trigger provisioning.
- Event is triggered when: A new object is created
- Triggers on objects of type: Resources
-
Click Apply.
-
Create a new code method. Click New.
-
Select Execute code method. Enter the following details and click OK:
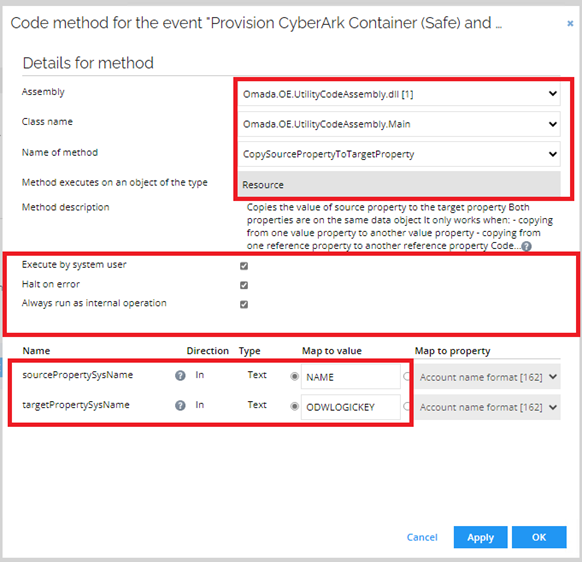
-
Create a new code method. Click New.
-
Select Execute code method. Enter the following details and click OK:
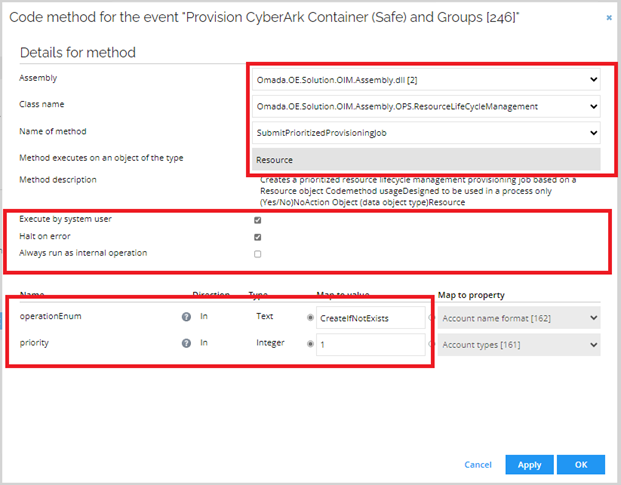
-
In the upper left corner, click Filter.
-
Create a new filter and enter the following details:
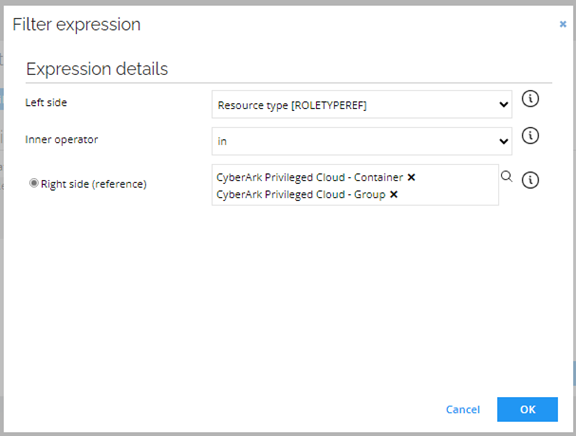
-
Click OK. In the Event definition view, click OK.
CyberArk Container and Groups - Delete
-
In Omada Identity, go to Setup > Administration > Process configuration > Event definitions. Click New.
-
Enter the following details:
- Name: Provision CyberArk Container (Safe) and Groups
- Description: When a new resource of type CyberArk Privilege Cloud - Container or CyberArk Privilege Cloud - Group is deleted, trigger provisioning.
- Event is triggered when: A new object is deleted
- Triggers on objects of type: Resources
-
Click Apply.
-
Create a new code method. Click New.
-
Select Execute code method. Enter the following details and click OK:
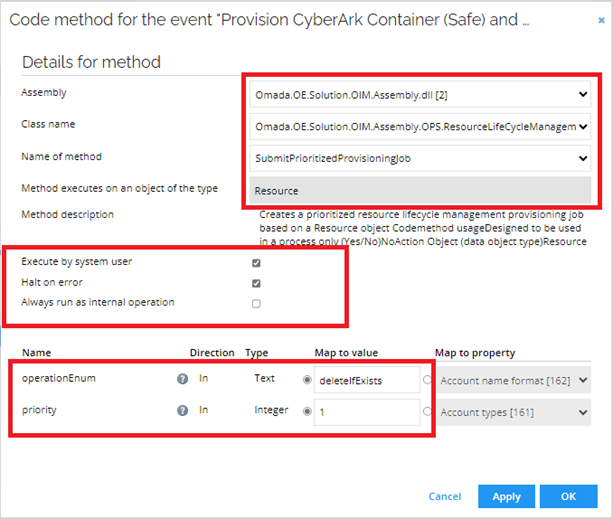
-
In the upper left corner, click Filter.
-
Create a new filter and enter the following details:
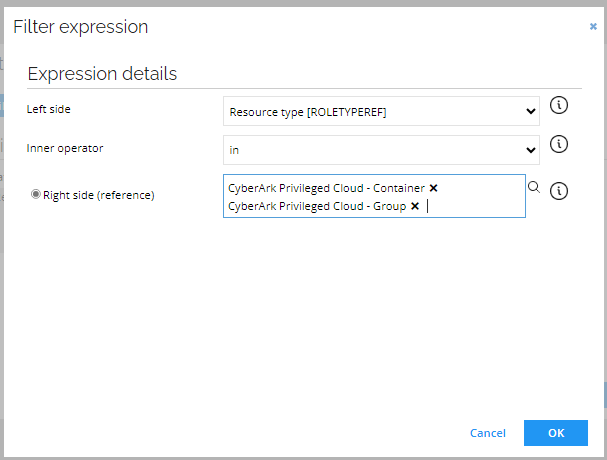
-
Click OK. In the Event definition view, click OK.
CyberArk Privileged Data - Create
-
In Omada Identity, go to Setup > Administration > Process configuration > Event definitions. Click New.
-
Enter the following details:
- Name: Provision CyberArk Privileged Data
- Description: When a new resource of type CyberArk Privilege Cloud - Privileged Data is created, trigger provisioning.
- Event is triggered when: A new object is created
- Triggers on objects of type: Resources
-
Click Apply.
-
Create a new code method. Click New.
-
Select Execute code method. Enter the following details:
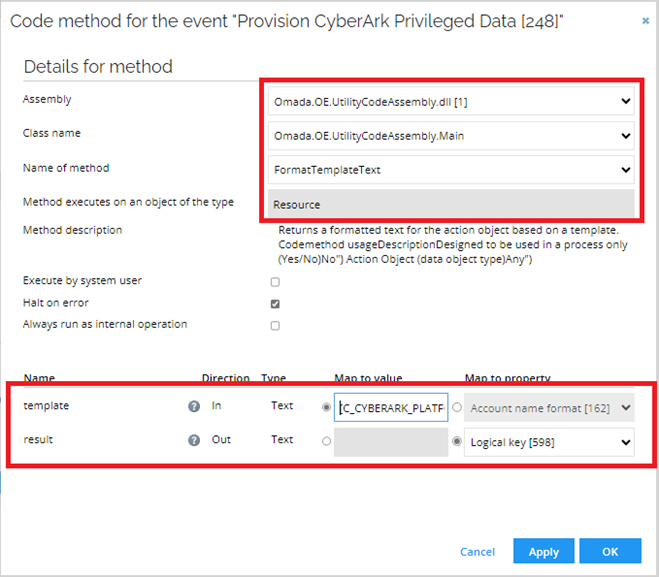
-
In the template field, enter the following value and click OK:
[C_CYBERARK_PLATFORMID]-[C_CYBERARK_USERNAME]-[C_CYBERARK_ADDRESS] -
Create a new code method. Click New.
-
Select Execute code method. Enter the following details and click OK:
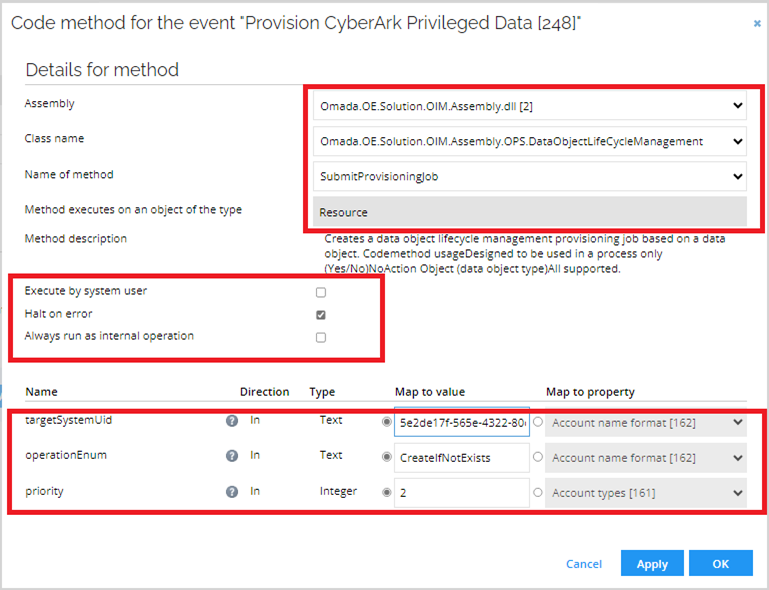 note
noteTo find your targetSystemUid, navigate to your CyberArk system then press Ctrl + right-click. Select Form data uid. Copy the UID and paste it into the targetSystemUid field.
-
In the upper left corner, click Filter.
-
Create a new filter and enter the following details:
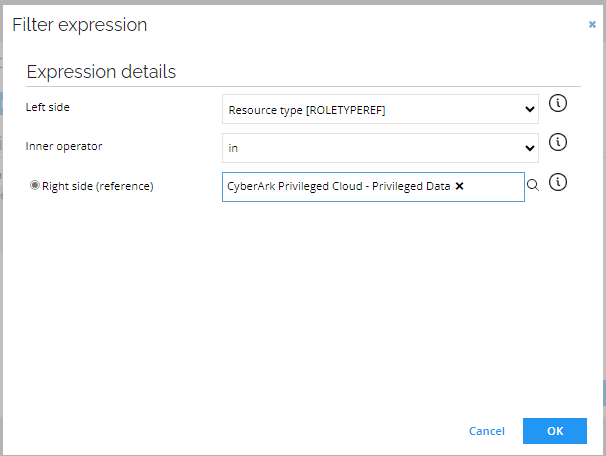
- Click OK. In the Event definition view, click OK.
CyberArk Privileged Data - Delete
-
In Omada Identity, go to Setup > Administration > Process configuration > Event definitions. Click New.
-
Enter the following details:
- Name: Provision CyberArk Privileged Data
- Description: When a new resource of type CyberArk Privilege Cloud - Privileged Data is deleted, trigger provisioning.
- Event is triggered when: A new object is deleted
- Triggers on objects of type: Resources
-
Click Apply.
-
Create a new code method. Click New.
-
Select Execute code method. Enter the following details:
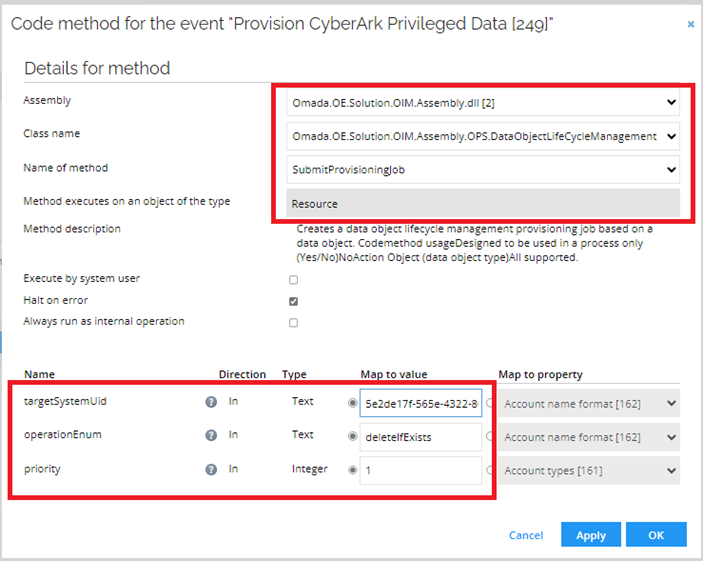 note
noteTo find your targetSystemUid, navigate to your CyberArk system then press Ctrl + right-click. Select Form data uid. Copy the UID and paste it into the targetSystemUid field.
-
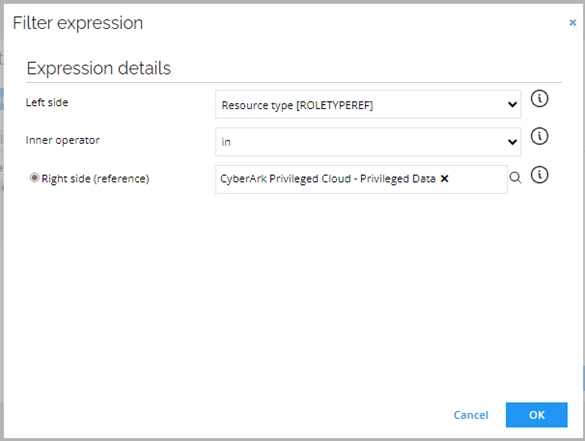
In the upper left corner, click Filter.
-
Create a new filter and enter the following details:
-
Click OK. In the Event definition view, click OK.
Additional configuration
For provisioning to work correctly, configure the additional elements in Omada Identity.
Creating the Safe property
- Go to Setup > Administration > Process configuration > Properties.
- Click New and then Reference property. Enter the following details:
- Name: Safe
- Description: CyberArk Privileged Cloud attribute
- System name: C_CYBERARK_SAFE
- Refers object of type: Resource
- Control type: Lookup (single value)
- In the upper left corner, click Edit lookup view.
- Click Expressions field and then New. Enter the following details:
- Left side: Resource Type
- Inner operator: in
- Right side: CyberArk Privileged Cloud – Container
Adding values to the PlatformId property
- Go to Setup > Administration > Process configuration > Properties.
- Go to the PlatformId property and click it. In the upper left corner, select the Values field.
- Add the platform IDs available in your CyberArk system.
Adding values to the Type property
- Go to Setup > Administration > Process configuration > Properties.
- Go to the Type property and click it. In the upper left corner, select the Values field.
- Add the types available in your CyberArk system.
Adding expression to the CyberArk Rights property
- Go to Setup > Administration > Process configuration > Properties.
- Go to Cyberark Rights and click it. In the upper left corner, select Edit lookup view.
- Click Expressions > New. Enter the following details:
- Left side: Resource Type
- Inner operator: in
- Right side: CyberArk Privileged Cloud – Rights
Adding fields to the Resources form
- Go to Setup > Master data > Resources. Click New.
- Use CRTL + right button and then choose Form designer.
- Click New section > Fields > Name: CyberArk Privileged Cloud.
Configuring the Resources data object type
- Go to Setup > Administration > Process Configuration > Data object types.
- Search the Resource (id 52) object. Click Properties.
- Add the following properties:
- C_CYBERARK_PLATFORMID
- C_CYBERARK_SECRET
- C_CYBERARK_ADDRESS
- C_CYBERARK_USERNAME
- C_CYBERARK_TYPE
- C_CYBERARK_SAFE
- Select the Type form: Resource > Section: CyberArk Privileged Cloud.