Data provisioning
Connector settings
| Parameter | Description |
|---|---|
| Base address | https://[domain].Aha/api/v1/ |
| Authentication mode | OAuth2 |
| OAuth Grant Type | Static token |
| OAuth Static Token | Your Aha! token |
| OAuth Static Token Type | Bearer |
| Content type header | application/json |
| Accept header | application/json |
| Test Connection | select the checkbox |
| Test query | users |
Task mappings
Aha! User
The object is used to create, update, and deactivate user (account).
| Parameter | Operator | Source |
|---|---|---|
| Object Id | Map | ObjectId |
| Object type | Constant | AhaUser |
| Operation | Map | Operation |
| user.email | Map | ROPE_ATTR_EMAIL |
| user.first_name | Map | ROPE_ATTR_FIRSTNAME |
| User.last_name | Map | ROPE_ATTR_LASTNAME |
| user.role | Expression | Operation=="Create" ? ROPE_ATTR_C_AHA_PERMISSION : null |
| user.enabled | Expression | ROPE_Disabled ? false : true |
| productid | Expression | Operation=="Create" ? ROPE_ATTR_C_AHA_WORKSPACE : null |
| userid | Expression | Extensions.GetFirstValue(ROPE_DistinguisedName,ROPE_ExternalAnchor,JobAnchor) |
The identity_provider_id field in Aha! links users to an external identity provider in SSO-enabled environments, enabling secure authentication. It can be added to your AhaUser task mapping and is represented by a fixed string value provided by the identity provider.
Aha! Role Assignment
The object is used to create and delete role and workspace assignments.
| Parameter | Operator | Source |
|---|---|---|
| Object Id | Map | ObjectId |
| Object type | Constant | AhaRoleAssignment |
| Operation | Map | Operation |
| product_role.role | Map | ROPE_ATTR_C_AHA_ACCESS_PERMISSION |
| product_role.product_id | Map | ROPE_ATTR_C_AHA_PRODUCTID |
| userid | Expression | Extensions.GetFirstValue(ROPE_DistinguisedName,ROPE_AccountExternalAnchor,JobAnchor) |
Aha! Administrative Role Assignments
The object is used to create and delete users assignments to a group.
| Parameter | Operator | Source |
|---|---|---|
| Object Id | Map | ObjectId |
| Object type | Constant | AhaAdminRoleAssignment |
| Operation | Map | Operation |
| userid | Expression | Extensions.GetFirstValue(ROPE_DistinguisedName,ROPE_AccountExternalAnchor,JobAnchor) |
| user.administrator_roles.administer_account | Expression | (Operation=="Create" || Operation=="Update") && ROPE_Resource == "administer_account" ? "true" : null |
| user.administrator_roles.administer_billing | Expression | (Operation=="Create" || Operation=="Update") && ROPE_Resource == "administer_billing" ? "true" : null |
| user.administrator_roles.administer_configuration | Expression | (Operation=="Create" || Operation=="Update") && ROPE_Resource == "administer_configuration" ? "true" : null |
| user.administrator_roles.administer_account | Expression | Operation=="Delete" && ROPE_Resource == "administer_account" ? "false" : null |
| user.administrator_roles.administer_billing | Expression | Operation=="Delete" && ROPE_Resource == "administer_billing" ? "false" : null |
| user.administrator_roles.administer_configuration | Expression | Operation=="Delete" && ROPE_Resource == "administer_configuration" ? "false" : null |
Adding Aha! permissions to the data object type resources
-
Go to Setup > Data Object Type. Select Resource from the list, and then Properties > Add. Select Aha Permission (C_AHA_ACCESS_PERMISSION). Click OK.
-
Go to Setup > All Systems > Omada Identity > Export queries and mappings. From the list, choose Resources (with the Update or create operation) and click Edit. In the Mappings tab, search for the Aha Permission field. Follow the example below:
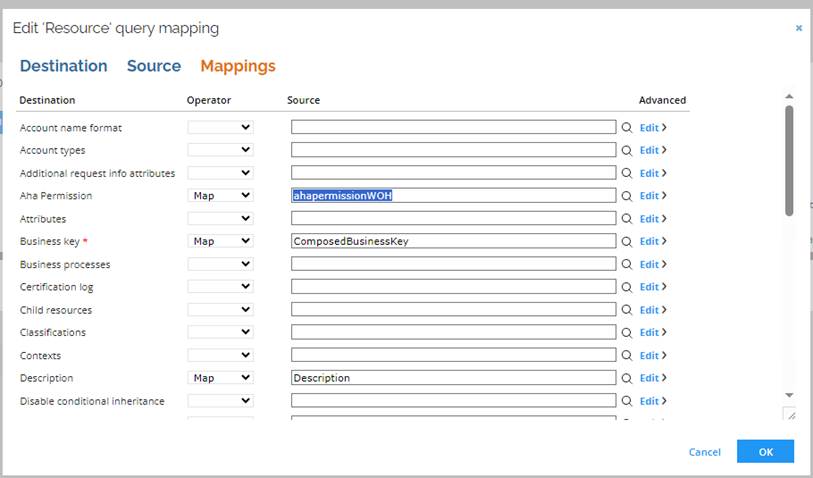
-
Click OK.
RoPE configuration
Products (workspace) and roles are managed via an attribute on the User object (as resource-driven attributes). After importing the products and roles objects, perform the following steps to set up resource-drive attributes:
-
Open the RoPE configuration file:
- On-prem:
\Omada Identity Suite\Role and Policy Engine\Service\ConfigFiles - Cloud: In the Cloud Management Portal, navigate to Environments. In the environment row, from the drop-down menu, select Configure. Choose the RoPE configuration tab.
- On-prem:
-
Add the following lines under the Attribute Value Resolver extension (change the key value in case you already have that specific key defined):
<add key="AHA_permission" name="Aha Account:C_AHA_PERMISSION" extraInfo="Type:ReferencePath" value="/#ASSIGNMENTS_PER_RESOURCETYPE/Aha Workspace:[C_AHA_ACCESS_PERMISSION]"></add>
<add key="AHA_permissioncompany" name="Aha Account:C_AHA_PERMISSION" extraInfo="Type:ReferencePath" value="/#ASSIGNMENTS_PER_RESOURCETYPE/Aha Company:[C_AHA_ACCESS_PERMISSION]"></add>
<add key="AHA_workspace" name="Aha Account:C_AHA_WORKSPACE" extraInfo="Type:ReferencePath" value="/#ASSIGNMENTS_PER_RESOURCETYPE/Aha Workspace:[DESCRIPTION]"></add>
<add key="AHA_company" name="Aha Account:C_AHA_WORKSPACE" extraInfo="Type:ReferencePath" value="/#ASSIGNMENTS_PER_RESOURCETYPE/Aha Company:[DESCRIPTION]"></add>
Advanced configuration
Select the Prioritize delete tasks checkbox:
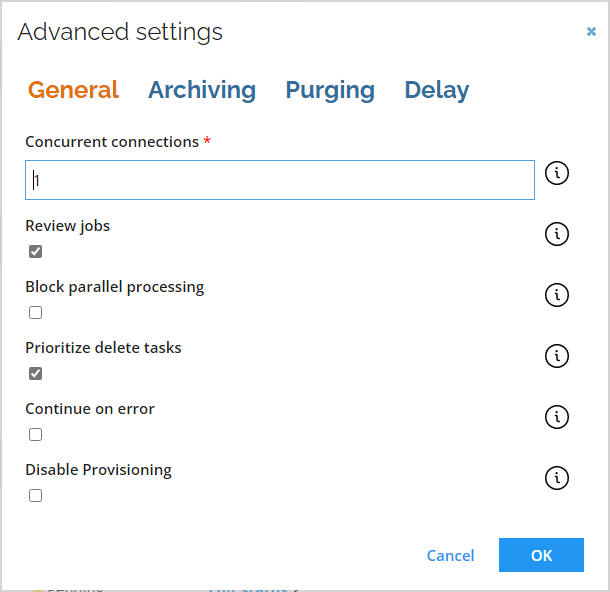
Additional configuration
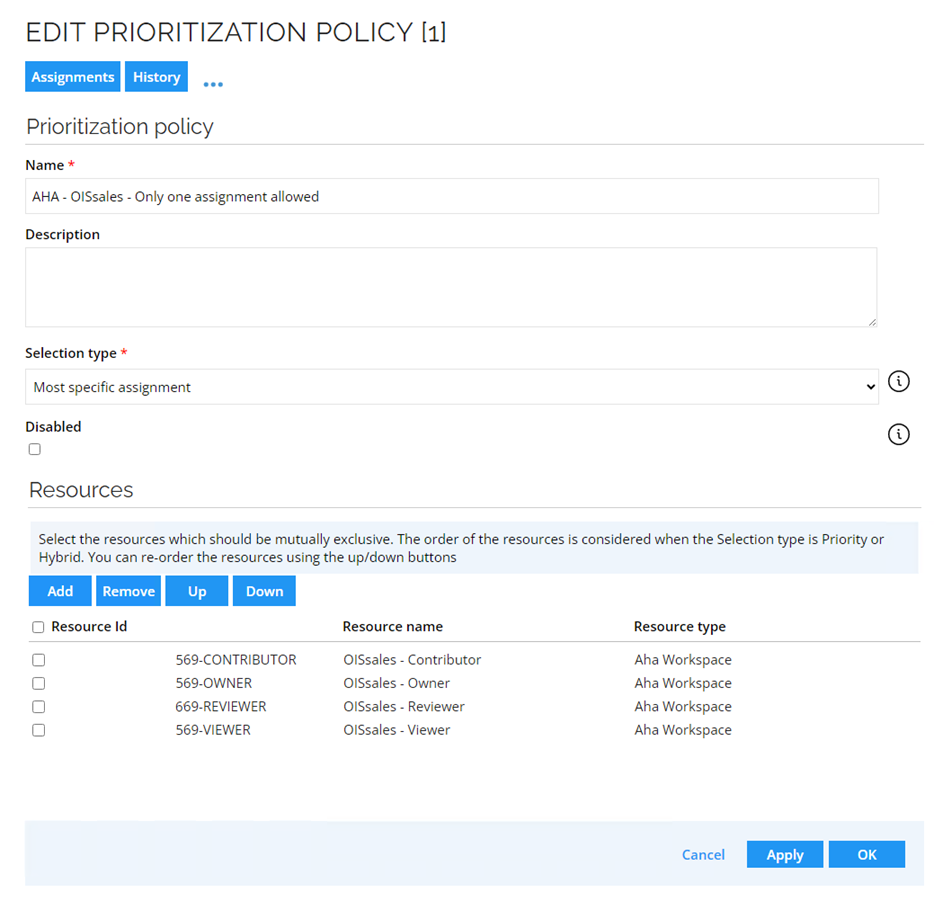
Aha! does not allow users to have more than one role per workspace/company. For Omada to function correctly, configure the prioritization policies. Create a separate prioritization policy for each workspace/company you have in Aha!:
-
Go to Setup -> Policies -> Prioritization policies and click New. Review the example below: