Standard extensions
Generic extension for mapping ODW attributes to OPS provisioning attributes
The extension is typically used when a target system requires an internal identifier to modify or deprovision an account and this identifier is not represented in the ES. In that situation the extension can be used to fetch the identifier directly from the ODW and assign it to a RoPE attribute which can then be used by the OPS. Any attribute to be mapped to RoPE needs to be specified using the following format:
<add key="**UNIQUE KEY (e.g. number)**" extraInfo="**RESOURCE TYPE DISPLAY NAME**" name="**ODW ATTRIBUTE NAME**" value="**ROPE PROVISIONING ATTRIBUTE NAME**" />
Alternatively, if you want to refer to the resource directly (e.g. due to ambiguous resource type names), use the following format:
<add key="**UNIQUE KEY (e.g. number)**" extraInfo="UID:**RESOURCE TYPE UID**" name="**ODW ATTRIBUTE NAME**" value="**ROPE PROVISIONING ATTRIBUTE NAME**" />
<add type="Omada.RoPE.Controller.OISX.Extensions.MapAttributesFromActualDataExtension, Omada.RoPE.Controller.OISX">
<settings>
<add key="1" extraInfo="ServiceNow Group" name="snowAssignmentID" value="SERVICENOW_ASSIGNMENT_ID" />
<add key="2" extraInfo="ServiceNow Role" name="snowAssignmentID" value="SERVICENOW_ASSIGNMENT_ID" />
</settings>
</add>
Actual account name
Configuration and example
The Actual Account Name extension is configured by default when installing RoPE version v14. The extension is configured through the C:\\Program Files\\Omada Identity Suite\\Role and Policy Engine\\Service\\ConfigFiles\\EngineConfiguration.config file.
<add type="Omada.RoPE.Controller.OISX.Extensions.ActualAccountNameComputer, Omada.RoPE.Controller.OISX\" />
The extension has no configuration options.
The extension can be removed from the configuration if you do not wish to use it. This will save computation time and storage.
Additional assignment creator for context resources
This extension adds additional resource assignments for resources that are referred by the contexts in which an identity is. You can use the concept together with the assignment policies or as an alternative to the assignment policies.
The extension works for all types of context objects, not just org. units.
Organizational unit data object type has built in Resource reference property (with system name: ROLESREF) that links Resource data objects to Org. unit data objects. You must use the extension in order to have the referred resources assigned to the identities in an org. unit.
Configuration and example
You must adjust the RoPE configuration, to make sure it uses the extension:
<add type="Omada.RoPE.Controller.OISX.Extensions.AdditionalAssignmentCreatorForOrgUnitRoles, Omada.RoPE.Controller.OISX" >
<settings>
<add key="ResourceAttributes" value="ROLESREF"/>
</settings>
</add>
ResourceAttributes is comma-delimited list of reference properties present on context objects to use to refer to resources that should be assigned to the identities in the contexts.
For the extension to work properly, you must register all reference properties specified in the ResourceAttributes extension setting and also in the customer setting RoPEReferenceAttribs. This change will force RoPE to treat them as reference type attributes.
Attestation survey
The extension creates CRAs with the reason Review OK if the identity has CRAs that have been approved in a verdict survey.
Note that a CRA caused solely by a Review OK reason cannot stand alone. There have to be other reasons as well. Otherwise, the extension removes the added CRAs again.
The extension disables assignments where you have selected Remove in the Verdict survey. The extension also adds an attribute called ApprovalInfo to the CRAs that have a verdict.
Configuration and example
The extension does not support any configuration settings.
<add type="Omada.RoPE.Controller.OISX.Extensions.AttestationSurveyExtension, Omada.RoPE.Controller.OISX" />
Attribute value resolver
The extension resolves and assigns the value(s) for assignment attributes based on configured data object reference paths and dynamic expressions. You can configure it with a number of attributes and corresponding reference paths or dynamic expressions.
Attribute values resolved with the Attribute Value Resolver extension takes precedence over existing attribute values for a CRA.
Reference path resolution
A reference path is resolved using the CRA as starting point. A reference path must start with either #IDENTITY", #RESOURCE, or #ASSIGNMENTS_PER_RESOURCETYPE.
A reference path can have a display name format. Use the prefix #ASSIGNMENTS_PER_RESOURCETYPE to resolve attribute values for values assigned using the Resource driven attributes concept.
Reference path elements are evaluated before Expressions, which are described in the next section.
Expression resolution
The resolution of dynamic expressions use Dynamic Expresso which is an interpreter for simple C# statements.
An expression must return one of the supported data types:
boolDateTimeintStringGuid(reference)
The returned value of an expression must match the data type of the attribute which the resolved value is for. If it doesn't match, it will result in an error.
The following parameters can be used in an expression:
Built-in RoPE assignment data:
ROPE_AssignmentKeyROPE_IdentityIdROPE_AccountTypeIdROPE_AccountNameROPE_AccountAssignmentKeyROPE_DifferentiatorROPE_ResourceIdROPE_ResourcePoolIdROPE_AssignmentTypeIdROPE_ValidFromROPE_ValidToROPE_DisabledROPE_PreValidROPE_ReasonTypes
RoPE assignment attribute values on the form ROPE_ATTR_<attribute name, for instance:
ROPE_ATTR_FIRSTNAMEROPE_ATTR_LASTNAMEROPE_ATTR_IDENTITYIDROPE_ATTR_OUIDROPE_ATTR_INITIALPASSWORD
Customer settings on the form CUSTSETTING_<customer setting key>:
CUSTSETTING_ContractorMaxValidity
Data connections on the form DATACONNECTION_<data connection_name>_<data connection_element>, for instance:
DATACONNECTION_RoPE_InitialCatalog
Expression elements are evaluated after Reference path elements. It means that the result of a Reference path can be used inside an Expression element. Moreover, Expression elements are evaluated in the order of appearance in the configuration file. An expression can use the result of another expression configured above it in the configuration file.
More information about Dynamic Expresso can be found in the GitHub documentation.
Configuration and example
The extension can be configured with a number of settings. Each setting represents how the value for an attribute should be resolved.
This extension supports the following configuration settings:
| XML attribute on a setting | Description |
|---|---|
| key | Unique key for the setting. |
| name | Specifies the attribute to resolve value(s) for. You can optionally specify that it should only be done for CRAs for resources of a specific resource type. However, it is recommended that you specify this in extraInfo instead. Has the format: [Resource type name]:[attribute property system name] |
| extraInfo | Semicolon-delimited key value pairs. The supported keys are: - Type (required) : must specify either ReferencePath or Expression.- ResourceType (optional): must specify the name of a resource type. - MultiValue (optional): When set to True, all available resource driven attributes will be applied and not only the value with the highest priority. Examples: Type:Expression;ResourceType:GroupType:ReferencePathType:ReferencePath; MultiValue:True Note: In versions earlier than May 2025 Cloud Update, Type:ReferencePath;MultiValue:True must be written without a space. For more information, see Resolved issues and bugs fixed for May 2025. |
| value | Specifies how the attribute value should be resolved. If the resolution is of type ReferencePath then the value must specify a reference path that is evaluated with the CRA as starting point. A reference path must start with either #IDENTITY, #RESOURCE, or #ASSIGNMENTS_PER_RESOURCETYPE. A reference path can have a display name format. If the resolution is of type Expression then value must specify a dynamic expression. |
Example 1
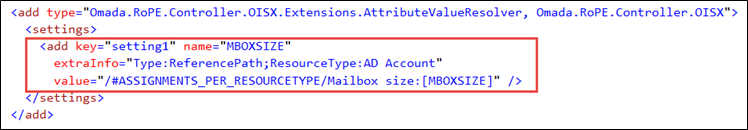
We resolve and assign the value of the CRA attribute MBOXSIZE by evaluating a Reference path. Resolution is only done if the CRA is for a resource of the type AD account.
Resolution is done as follows: Look in the other CRAs in the calculation > Find the subset that are for resources of the resource type Mailbox size > Get the value of the assignment's MBOXSIZE attribute.
Example 2
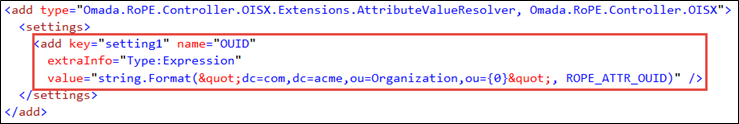
We resolve and assign the value of the CRA attribute OUID by evaluating an Expression.
Resolution is done by executing the C# string.Format method and using the current value of the OUID attribute as the parameter.
Business context
The extension disables all calculated assignments for an identity if the identity has no primary context. More specifically, if the identity has a primary context type specified, but is not a member of the context, all assignments are disabled.
The purpose is to handle a scenario with a contractor that works for a business partner (primary context) and has assignments for a project. If the organization terminates the business partner, this extension helps you to remove the contractor's access.
Configuration and example
The extension does not support any configuration settings.
<add type="Omada.RoPE.Controller.OISX.Extensions.BusinessContextExtension, Omada.RoPE.Controller.OISX" />
Conditional inheritance evaluator
You can apply the ConditionalInheritanceEvaluator extension to implement Conditional inheritance in, for example, SAP scenarios. The goal of conditional inheritance is that a child resource is only assigned to an identity if it has the same attribute as the identity (either inherited from the identity object or one of its context assignments).
Configuration
You can configure the attributes to match on and whether just a single match is required, or all attributes must match.
<add type="Omada.RoPE.Controller.OISX.Extensions.ConditionalInheritanceEvaluator, Omada.RoPE.Controller.OISX">
<settings>
<add key="ObjectType:Resource" value="OUREF"/>
<add key="MatchContextMembershipTo" value="OUREF"/>
<add key="RequireFullMatch" value="false"/>
</settings>
</add>
This extension supports the following configuration settings:
ObjectType:Resource- type a comma-delimited list of system names of properties that are on the data object type, for example the resource data object type.MatchContextMembershipTo- if defined, the child resource value is matched towards all the context assignments of the identity. The child resource value is configured as a custom reference property on the resource data object type.RequireFullMatch- set it to True to require a match on all the stated properties. If you set it to false, only one match is required.
The value configured in MatchContextMembershipTo and ObjectType:Resource is a (single value) property system name.
If the rules defined with ObjectType:Resource is combined with the MatchContextMembershipTo rule, then the RequireFullMatch setting defines the result. If full match is required, all rules must resolve true. If not set, at least one of the rules must resolve true.
Example
In the RoPE extension configuration, we set the MatchContextMembershipTo to OUREF and we add the OUREF property to the Resources data object type.
When RoPE then traverses the child resources of a role, it will only assign the child resource if the OUREF of the child resource is within the context memberships of the identity. Only direct context memberships are evaluated, i.e., not parent contexts.
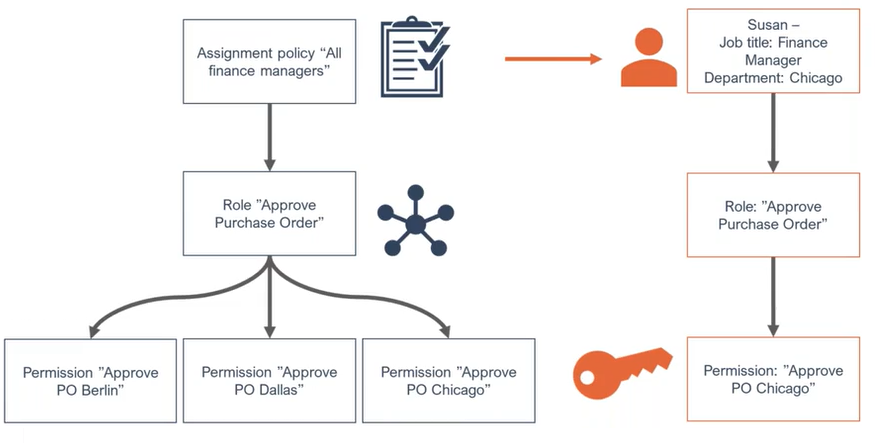
Consider an SAP system in which a number of functionally equivalent SAP roles exist which are created for various departments. The SAP roles are grouped in functional enterprise roles that are assigned to the employees.
The goal is that an employee only gets the SAP roles contained in their functional roles that are defined for their department. That's why in the example below, Susan gets the Approve Purchase Order role specifically for Chicago:
Disable conditional inheritance
When the extension is enabled, it is evaluated for all resource parent child relations unless disabled with the Boolean property Disable conditional inheritance available on the data object type Resources.
As its name imply, when Disable conditional inheritance available is set to True on the parent resource, the conditional inheritance is disabled, and the child resources are assigned unconditionally (even if the rules of the extension are not met).
Constraint evaluator
The extension is part of the Separation of Duties feature in Omada Identity.
Configuration and example
In this extension, specify the following attribute: CalculateSurvivor.
If a survivor is calculated (set to true): In case of a violation between two resource assignments, one of the resource assignments is allowed and the other one is blocked.
If a survivor is not calculated (set to false): the assignments in violation are immediately blocked. However, if one or more of these assignments are already provisioned into the target systems, they will not be deprovisioned before the blocking of the assignments has been approved in the violation evaluation process. They are sent to the "Pending deprovisioning" state.
<add type="Omada.RoPE.Controller.OISX.Extensions.ConstraintEvaluatorExtension, Omada.RoPE.Controller.OISX">
<settings>
<add key="CalculateSurvivor" value="false"/>
</settings>
</add>
Default account name resolver
This extension computes the default account names for an identity. An identity can have a default account name per account resource defined in Omada Identity. A default account name is calculated using the account name format specified in the resource type.
Due to a data model change in the April Cloud release, the previously customized extension does not work anymore and has to be updated.
Configuration and example
The extension does not support any configuration settings.
<add type="Omada.RoPE.Controller.OISX.Extensions.DefaultAccountNameResolver, Omada.RoPE.Controller.OISX" />
Delegate access
The extension is part of the Delegate access feature in Omada Identity.
Configuration and example
The extension does not support any configuration settings.
<add type="Omada.RoPE.Controller.OISX.Extensions.DelegateAccessExtension, Omada.RoPE.Controller.OISX" />
Differentiator
The purpose of the Differentiator RoPE extension is to define the differentiator concept for resource assignments to avoid its automatic merging to the same resource based on the attributes.
If the attribute values are different, then, the Differentiator extension creates separate CRA's for the same resource.
The Differentiator was designed for short ID values.
Configuration and example
Using the extension, you can configure the differentiator attributes per resource type in the RoPE configuration.
To do so, add the following code snippet to the RoPE configuration and adjust the differentiator attributes as needed:
<add type="Omada.RoPE.Controller.OISX.Extensions.AssignmentAttributeValueDifferentiator, Omada.RoPE.Controller.OISX" >
<settings>
<add key="<resource type unique identifier>" value="<comma-separated list of attribute system names>"/>
</settings>
</add>
For example, for the Exchange Mailbox Access resource type and the Mailbox Location and Mailbox reference attributes, the code snippet looks as follows:
<add type="Omada.RoPE.Controller.OISX.Extensions.AssignmentAttributeValueDifferentiator, Omada.RoPE.Controller.OISX" >
<settings>
<add key="24bc28da-1b36-40bd-95a3-d4b5d344553d" value="MAILBOXLOCATION,MAILBOXREF"/>
</settings>
</add>
Usage example
For a reporting platform, the security model is defined by group permissions assigned per report, granting access to the particular report. When assigning a group to an account, a data set is assigned to scope the data presented in the report.
For example, a time registration report is scoped per organizational unit to allow granting permission to a manager to view the data report only for the people for whom the manager is responsible.
Since a manager may be responsible for more than one org. unit, there can be several assignments for one identity. Each assignment should be visible in Omada for access reviews, reporting, and such.
The Differentiator extension allows splitting multiple assignments to the same report on the organizational identifier used in the assignment by specifying the attribute in the configuration.
Exchange integration
The purpose of this extension is to prevent resource assignments to Exchange Mailbox resources from being merged into one resource assignment.
Configuration and example
The extension does not support any configuration settings.
<add type="Omada.RoPE.Controller.OISX.Extensions.ExchangeIntegrationExtension, Omada.RoPE.Controller.OISX" />
Exchange Hybrid
The Exchange Hybrid relies on the Exchange system trusting two account systems - Azure Directory and Active Azure Directory. By that means, RoPE will calculate two exchange mailboxes, one for each account, if the user has an account in both places.
The Exchange Integration Extension enables and disables the mailbox assignment based on where the mailbox is actually located. Initially the mailbox will be provisioned to the location stated in the MAILBOXLOCATION attribute.
The extension supports multiple exchange systems and multiple mailboxes resource types.
The functionality is only designed to work when the account systems trusted by exchange are configured with the standard AD and AAD collectors named:
- Microsoft Active Directory
- Microsoft Entra ID
Initial password
The extension calculates the content of the INITIALPASSWORD attribute on the account assignment if the attribute is present on the resource type, and only if it is a new account.
The password adheres to the password policy defined on the account resource or on the system if it is not present on the account resource.
When the account has been provisioned (or when provisioning status is set to OK) the initial password attribute value is removed from the assignment.
Event definitions and notifications
The notification through e-mail to the user of their initial password is based on the new event concept for calculated assignments.
When the provisioning status for an account assignment is updated to OK and the password is present on the assignment, sends out an e-mail notification that contains the randomized password that the user can use.
Below is a list of six event definitions created for each resource type, and each with their own event definition and e-mail action, such as e-mail notifications.
- Personal account notifications are sent to the manager.
- Initial password notifications for personal accounts are sent to the manager.
- Non-personal account notifications are sent to the identity.
- Passwords for non-personal accounts are sent to the identity
- Technical account notifications are sent to the identity owner.
- Passwords for technical accounts are sent to the identity owner.
The event definitions including e-mail actions and e-mail templates are created whenever a resource type is being edited.
You can disable the list of events and notifications mentioned above by disabling the customer setting EnableAccountCreationNotification.
If a custom solution requires a more advanced notification scheme, the event definitions can be extended. For example, it could be a requirement for a personal account notification to be sent directly to the identity.
Manual provisioning
The extension is part of the Manual provisioning feature in Omada Identity.
Configuration and example
The extension does not support any configuration settings.
<add type="Omada.RoPE.Controller.OISX.Extensions.ManualProvisioningExtension, Omada.RoPE.Controller.OISX" />
Provisioning service
The purpose of the Provisioning Service extension is to exclude certain identities from being provisioned by OPS.
Configuration and example
<add type="Omada.OPS.Integration.PolicyEngine.ProvisioningServiceExtension, Omada.OPS.Integration.PolicyEngine"" />
<settings>
<add key="IdentitiesToIgnore" value="dfc2ea28-b6c2-432d-aa55-7ade9dc93ba9,cbf14eb6-72b4-42d2-a5fc-eb0f12a37fac,86c3204a-1d33-48e9-a73a-ee9845b86c2a"/>
</settings>
</add>
If an account does not have a desired state, RoPE creates an Update provisioning task to disable the account after the identity is terminated. By default, this task is ordered the same as other update tasks, before the permission-related tasks.
However, this ordering may cause issues in systems that require permissions to be removed before the account is disabled, or that disallow permission changes on already-disabled accounts.
To address this, RoPE allows configuration of the task ordering to place disabled account updates after permission tasks. This behavior is disabled by default and can be enabled by setting the OrderDisabledAccountsLikeDeletedForSystems parameter in the ProvisioningServiceExtension.
This parameter accepts a comma-separated list of system UIDs for which this behavior should apply.
Example configuration:
<add type="Omada.RoPE.Controller.OISX.Extensions.OPS.ProvisioningServiceExtension, Omada.RoPE.Controller.OISX" >
<settings>
<add key="OrderDisabledAccountsLikeDeletedForSystems" value="5e11dcf0-295f-4393-a445-a0087ae887bb,b893756d-a7cd-4140-8f4b-aab4369ab90a" />
</settings>
</add>
Reference path attribute value resolver
The extension resolves and assigns the value(s) for assignment attributes based on the configured data object reference paths. You can configure it with a number of attributes and corresponding reference aths.
A reference path is resolved using the CRA as starting point. A reference path must start with either #IDENTITY, #RESOURCE, or #ASSIGNMENTS_PER_RESOURCETYPE.
This extension only exists for backward compatibility purposes. It is recommended to use AttributeValueResolver instead.
A reference path can have a display name format.
Attribute values resolved with the Reference Path Attribute Value Resolver extension takes precedence over the existing attribute values for a CRA.
Use the prefix #ASSIGNMENTS_PER_RESOURCETYPE to resolve attribute values for values assigned using the Resource driven attributes concept. For this prefix, the target attribute specification is of the
format: [resource type name]:[attribute property system name].
Note that the format is only supported for the #ASSIGNMENTS_PER_RESOURCETYPE prefix.
Configuration and example
Each setting key must be the name of an assignment attribute for which we want the value resolved using a reference path. The setting value is the reference path that we want to have resolved.
<add type="Omada.RoPE.Controller.OISX.Extensions.ReferencePathAttributeValueResolver, Omada.RoPE.Controller.OISX">
<settings>
# We want to assign the "system identifier" as a CRA attribute value
<add key="SYSTEMID" value="/#RESOURCE/SYSTEMREF:[SYSTEMID]" />
# We want to assign the identifier of the identity's orgunit as a CRA attribute value
<add key="OUID" value="/#IDENTITY/OUREF:[OUID]" />
# We want to assign the value of the attribute "Issuewareningquota" stated for resources of the type "Exchange Mailbox Option" that the identity is assigned to
<add key="Exchange User Mailbox:ISSUEWARNINGQUOTA" value="/#ASSIGNMENTS_PER_RESOURCETYPE/Exchange Mailbox Option:[ISSUEWARNINGQUOTA]" />
</settings>
</add>
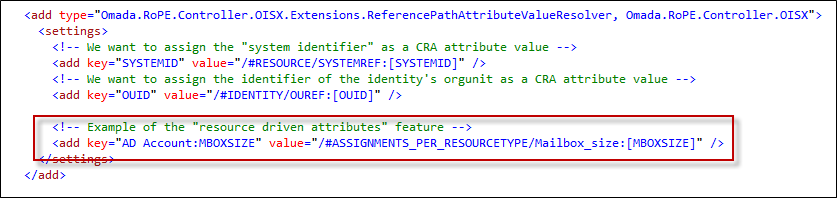
The example below should be read as: Concerning CRAs for resources of the resource type AD account: We assign the value of the CRA attribute MBOXSIZE this way: Look in the other CRAs in the calculation: Only the subset for resources of the resource type Mailbox_size: Get the value of the assigned resource's MBOXSIZE attribute:
RiskScoreCalculator2
This extension calculates the Risk Score and Risk Level for:
- Each Resource that is assigned.
- The Identity being computed.
- Optionally, a Risk Score is calculated for each CRA and assigned to the RISKSCORE attribute.
The extension produces log messages that describe how the Risk Scores of CRAs, identities and resources are computed. The purpose is to make it possible for administrators to gain insight into how Risk Scores are computed.
The log messages are not produced when the AsyncRiskScoreUpdates setting is enabled.
Configuration
The extension has a setting named AssignCRARiskScore. Only if it is set to True, the extension performs the Risk Score calculation for CRAs.
The extension updates the Risk Score and Risk Level of the Identity and Resource data objects regardless of whether Identity calculation results are discarded or not.
The extension has a setting named AsyncRiskScoreUpdates. If it is set to True, the extension performs updates of Risk Score and Risk Levels on Identities and Resources asynchronously. That is, the updates may still be in progress after a cycle run has completed, allowing RoPE to have a higher throughput.
Calculating risk scores and levels may have an impact on the RoPE performance.
SAP GRC policy check
This extension is used for the external SAP GRC SoD check within the Policy & Risk check feature.
The extension extracts all the relevant SAP resources and calls the SAP GRC web service (using the OPS gateway service to handle the request). If a policy violation is discovered in the response, a new
CalculatedPolicyCheck is added to each assignment. The result is also saved for the CRA in the tblCalculatedPolicyCheck table (this does not take place in the simulation mode).
For more information on how to enable simulation, see the Configuration of RoPE for SoD simulation section of Role and Policy Engine - policy check documentation.
Self-management
The Self-management extension is part of the Omada Identity Self-management feature in the Packaged Solution.
You can use the self-management feature for managing access to itself. It contains a process from which the end-users can request Omada Identity roles.
It is possible to disable the self-management extension, if you don't want to have ownerships calculated. In that case, you need to comment out the self-management extension in the RoPE configuration file, and you can then manage ownerships manually through the Effective owner/manager fields. It is possible to combine the self-management with manually maintaining owners, and in that case you need to use the Manual owners concept.
There are a number of roles that you can manage in Omada Identity:
- Resource ownership
- Resource folder ownership
- Org. unit management
- Identity management
- System ownership
- Cost center ownership
- Company ownership
- User group membership
- Service Desk agent role
- Classification tag ownership
- Employment ownership
You can extend the Self-management feature to apply to other data object types. There are both an effective manager/owner field and an explicit owner field on the object types.
The value in the explicit owner field is, by default, maintained by the ODW component. It is used by the RoPE extension to calculate a self-management resource assignment and, in turn, the population of the effective manager/owner.
The RoPE Self-management extension also allows for two self-management resources to control the membership of the same user group. For example, the Org. Unit Manager resource and the Identity Manager resource can both manage the Managers user group. The group membership is granted with the first assignment to one of the resources. The group membership is revoked when the last assignment to the resources is revoked.
The Self-management concept with the use of assignments to self-management resources is based on the OUID, SYSTEMID, and other ID string values. As a result, if, for example, an ID string value is
updated on an Org. unit or a System, the existing self-management resource assignment with reference to its string attribute value will point to a non-existing object. It has the following consequences:
-
The object owner is not updated, and the existing one remains until a new is appointed.
-
Should a new object be created having the previous ID, the current owner will also become an owner of the new object.
Such a situation has to be remedied manually with the following workaround:
Identify the resource assignment data objects to self-management resources where the managed object identifier, such as the OUID or SYSTEMID, has become obsolete. Expire those invalid resource assignments and request and approve the equivalent assignments for the correct combinations of identity, resource, and managed object id.
Configuration and example
This extension supports the following configuration settings:
-
CalculateExplicitOwners- specify whether the explicit owners stated on a managed object should be included in the computation of the effective owners of the managed object.- The explicit owners are always stored in the ExplicitOwner property.
- The Effective owners are either stored in the Ownerref or Manager property.
-
IndividualAssignments- this option enables fine-grained access reviews of assignments for the "Omada Identity management" resources in the Omada Identity portal.- Consider an identity that has made multiple access requests, for example, for the Omada Identity management "Group Member" resource to become the member of different user groups in Omada Identity. Using this option, RoPE computes a CRA for the "Group Member" resource for each time it has been requested. Each of the CRAs can be presented in an access review and thus the option allows for approving some group memberships while rejecting others.
-
Recompute- specify whether owners should be updated for data objects in each calculation.- If set to true, RoPE will update ownerships even if no change in resource assignments have been made. Setting this to True may impact performance.
- Default value: false
-
UpdateDataObjectsInNewThread- specify whether data object updates should be executed in a separate thread.- This is to increase throughput of RoPE. This means that the updates may still be in progress after the cycle run has completed.
- Default value: true
-
LoadDataInParallel- allows the batch preparation to be done in parallel.- If set to true, the batch preparation is done in parallel, improving the performance (especially when the batch size is high or there are numerous objects involved). If set to false, the batch preparation is done in a synchronous way. The parallel load has some overhead, so it is not always the best option.
- Default value: false
- You can measure the effect of the configuration by comparing the execution time in RoPE calculation logs. Check the following line:
Omada.RoPE.Controller.OISX.Extensions.SelfManagementExtension.Engine_BatchPrepared" executed in X msecs
-
UpdateDataObjectsBatchSize- allows to specify the batch size for updating data objects.- This setting determines the number of data objects (for example, resources or resource folders) that are updated in a single batch during self-management operations. Splitting updates into batches helps optimize performance and resource usage by balancing the workload between the application and the database.
- Default value: 5000
- You can increase or decrease this value to optimize performance based on the system's capacity and workload requirements.
<add type="Omada.RoPE.Controller.OISX.Extensions.SelfManagementExtension, Omada.RoPE.Controller.OISX" >
<settings>
<add key="CalculateExplicitOwners" value="true"/>
<add key="IndividualAssignments" value="true"/>
<add key="Recompute" value="false"/>
<add key="UpdateDataObjectsInNewThread" value="true"/>
<add key="LoadDataInParallel" value="false"/>
<add key="UpdateDataObjectsBatchSize" value="5000"/>
</settings>
</add>
If you add a custom self-management configuration, it is important that the attribute containing the reference to the managed object has the field Reference value format set to contain only the idProperty from the Self-management XML configuration:
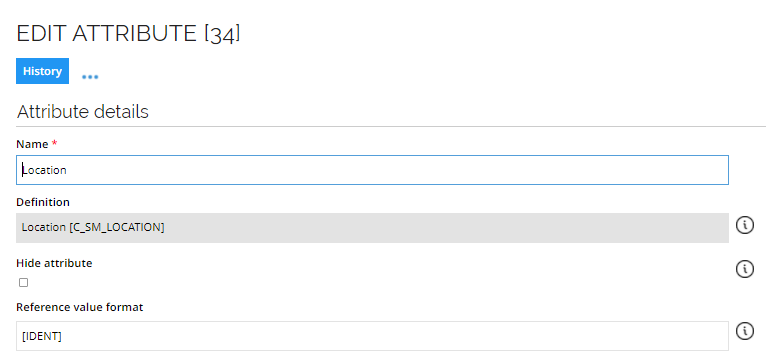
Shadow object event executor
Evaluates event definitions that are defined in the Omada Identity portal for resource types.
A calculated assignment shadow object is created in the Role & Policy Engine by this extension. The system automatically generates a data object type for each configured resource type. The attribute set of the resource type defines the available properties on the shadow object type along with a set of built-in properties.
Configuration and example
The extension does not support any configuration settings.
<add type="Omada.RoPE.Controller.OISX.Extensions.ShadowObjectEventExecutorExtension, Omada.RoPE.Controller.OISX" />
Unresolved identity account attribute remover
The extension removes certain attributes from accounts for the UNRESOLVED identity.
This is to prevent the accounts from being updated, for example, with wrong first- and last-name values in the target systems.
Configuration and example
This extension supports the following configuration setting:
AttributesToRemove - delimited list of attribute names to be removed from account assignments belonging to the UNRESOLVED identity.
<add type="Omada.RoPE.Controller.OISX.Extensions.UnresolvedIdentityAccountAttributeRemover, Omada.RoPE.Controller.OISX" >
<settings>
<add key="AttributesToRemove" value="FIRSTNAME,LASTNAME"/>
</settings>
</add>
Validity period attributes assigner
This extension assigns values to the VALIDFROM and VALIDTO attributes on all CRAs if these attributes are allowed on the resource type.
It assigns the computed ValidFrom and ValidTo values of a CRA to the corresponding VALIDFROM and VALIDTO attributes.
The extension should be used when manual or OPS provisioning is required for SAP or other systems that support a validity period on permission assignments. It ensures that manual and OPS provisioning tasks are triggered when the validity period of a CRA changes, which otherwise (deliberately) does not occur because most systems (except, for example, SAP) do not support validity periods on permission assignments.
Configuration and example
<add type="Omada.RoPE.Controller.OISX.Extensions.ValidityPeriodAttributesAssigner, Omada.RoPE.Controller.OISX" />
To use the extension, ensure the following configuration steps are completed:
- The VALIDFROM and VALIDTO attributes must be added to the attribute set of the relevant resource types.
- These two attributes must be included in the provisioning relevant attributes on the resource type.
- The Reconcile on attribute level customer setting must be set to true.
It is not necessary to add VALIDFROM and VALIDTO to the Reconciliation attributes map.
Validity resolver
The extension resolves the validity of an object that participates in a calculation of an assignment for an identity. The validity is resolved for objects of these types:
- Identity
- Resource
- Resource Assignment
- Context
- Assignment Policy
- Identity Context
- Actual Assignment
- Calculated Assignment
If the object has a validity period, it is considered. These objects have a validity period:
- Identity
- Resource
- Resource Assignment
- Assignment Policy
- Identity Context
- Calculated Assignment
If the object has a disabled state, it is also considered. These objects have a disabled state:
- Identity
- Resource
- Actual Assignment
- Calculated Assignment
Configuration and example
The extension does not support any configuration settings.
<add type="Omada.RoPE.Controller.OISX.Extensions.ValidityResolver, Omada.RoPE.Controller.OISX" />
Violation status calculator
The purpose of the Violation Status Calculator extension is to calculate the violation status for each CRA. The violation status is assigned to the ViolationStatus attribute.
The violation status of a CRA can have the following values:
-
OK - there are no violations for the CRA.
-
Evaluation pending – usage prevented – The CRA has a violation, is prevented from becoming active, and has an Evaluate violation process pending. Because usage is prevented, the assignment will not be provisioned while awaiting a decision, but it will be deprovisioned if it has already been provisioned.
infoThis status can occur if the CRA did not exist before the violation or if it existed but was Disabled.
-
Evaluation pending – usage allowed – The CRA has a violation, is active, and has an Evaluate violation process pending. Because usage is allowed, the assignment will not be deprovisioned while awaiting a decision.
infoThis status can occur if the CRA existed before the violation and was not Disabled.
-
Overridden - the CRA has a violation, but it has been overridden in an Evaluate violation process.
-
Blocked - the CRA has a violation, and it has been blocked in an Evaluate violation process.
Configuration and example
The extension does not support any configuration settings.
<add type="Omada.RoPE.Controller.OISX.Extensions.ViolationStatusCalculator, Omada.RoPE.Controller.OISX" />