Policy check
Omada Identity includes a simulation feature for making policy checks from an access request.
Before you turn on the simulation feature, you must ensure that your custom RoPE extensions do not cause side effects when being run as part of a simulation. A side effect is, for example, if an extension sends out an email or modifies a data object.
Below is an example of how you specify in your custom RoPE extension whether the calculation is running in a simulation:
using Omada.RoPE.Interfaces.Engine;
namespace MyAssembly
{
public class MyExtension : IEngineExtension
{
public ExtensionConfiguration Configuration { get; set; }
public void Initialize(IEngine engine)
{
// Check if we're running in a simulation.
// If so, it is important that the extension doesn't make "side effects"
// such as sending out emails or modifying data objects.
if (!engine.SimulationMode)
{
// ...
}
}
}
}
Configuration of RoPE for SoD simulation
The Policy check functionality uses a remote call to Omada Identity RoPE. You can configure the address to the remote call in the customer setting Remote API URL, which is placed in the Customer Settings in Omada Identity.
The default address is http://localhost:8733/RoPERemoteApi/.
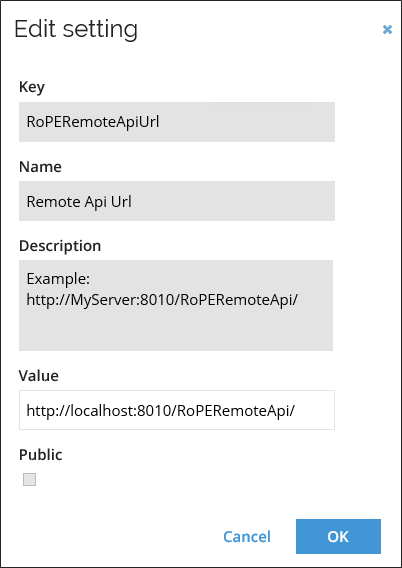
If you are not running Omada Identity RoPE and Omada Identity on the same machine, you must change this address.
Similarly, in the EngineConfiguration.config file on the RoPE service, you must configure the allowedRemoteIPMask attribute to allow the IP address of the Omada Identity to use the service.
Example: If Omada Identity is running on IP 192.168.0.100, it should look as follows:
<executor
…
allowedRemoteIPMask="::1,127.0.0.1,192.168.0.100 ">
<extensions>
SSL support in Segregation of Duties simulation
SSL can be enabled in the RoPE Simulation API used for Segregation of Duties simulation:
- Go to Setup > More... > Customer settings and find the section for the Role and Policy Engine. Click Remote API URL and change the URL prefix to
https://. - Add your trusted SSL certificate on the server where RoPE is installed with the following command, replacing certhash with the thumbprint of your trusted SSL certificate:
netsh http add sslcert ipport=0.0.0.0:8010 certhash=**d28b1add611771f82426e122de3cb6a58d48b6c8** appid={25e0e3f0-a3ba-47bc-825e-d9d21c4d5c83}