Resolved Issues and Bug Fixes
Read more about resolved issues and bug fixes in this release.
UI and UX
Read-only access to identity views on assignment policy
We have fixed an issue with the read-only state of the Identity view field in the Assignment policy data object form.
INC-290453
Missing translations of widget titles
We have enabled the translations of widget titles on dashboards where those translations were missing.
INC-286603
Performance issues
To reduce loading time and avoid session crashes, we have:
- improved performance when running Policy and risk checks in the new UI access approval flow,
- simplified the counting query to improve performance when updating the count of items in the menu.
INC-286918
Approving or rejecting requests with valid to set in the past
Due to an issue, it was impossible to approve or reject an access request that had the valid to in the past. We have now made it possible.
INC-289917
Export option not working under access approvals
The export option has been removed from the Approvals page, as exporting is available for the List views only.
INC-290584
Error message when using the assignment explorer
We have fixed an issue where the assignment explorer in the old UI would not open if references attribute values had identical names.
INC-290125, INC-289040, INC-290153
Menu structure not selectable to delete
Previously, clicking a checkbox in the menu structure also opened the corresponding item, making it impossible to select it without opening. This issue has been fixed: checkboxes can now be selected independently, allowing you to choose multiple items and use the Edit or other action buttons as intended.
INC-289445
Access request validity date - wrong date format according to user settings
Date formats now display correctly for users in English-speaking regions that don’t use the US format, such as the UK, Australia, and India. This update ensures dates are shown consistently according to local formatting standards.
INC-285865
Access Request
Request cancellation notification
We have fixed an issue with request cancellation notifications by adding a new template with actual values and removing the empty ones.
Role and Policy Engine
Permission compliance status set wrongly to Explicitly approved with Parent review
There was a bug related to the ReviewOK reason: the child resources were inheriting the ReviewOK reason from the parent, which was causing the compliance status to be set to Explicitly approved instead of Implicitly approved. Now, this wrong behavior has been fixed, and children do not inherit the ReviewOK reason from parents anymore.
INC-285597
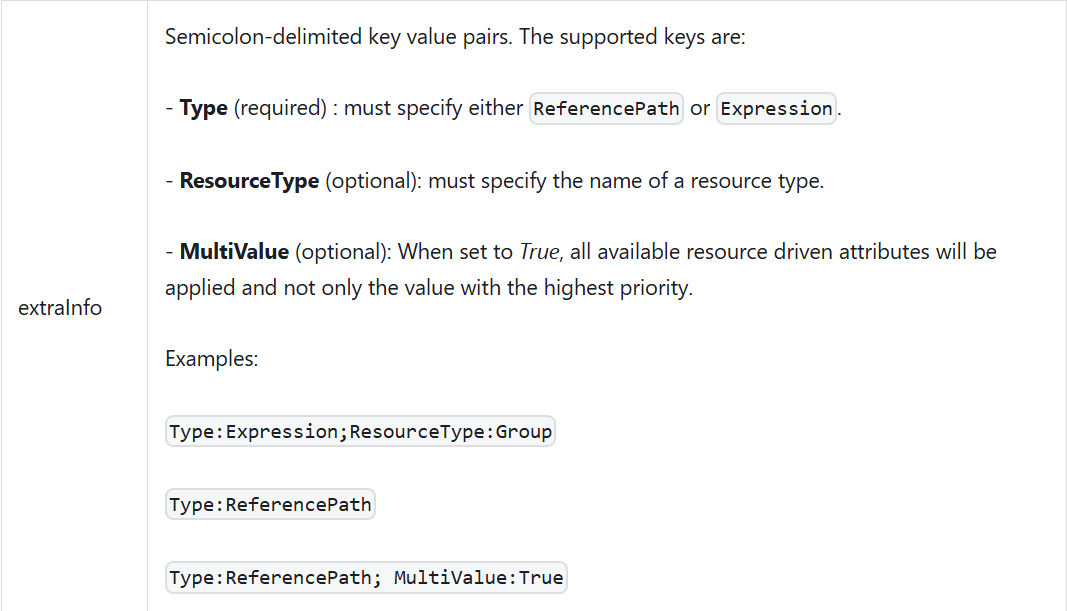
MultiValue resource-driven attribute failing
There was an issue where the RoPE AttributeValueResolver extension ignored the MultiValue attribute if there were spaces between the values in the extraInfo. We now support the syntax with a space after the semicolon: Type:ReferencePath; MultiValue:True.
For details, see the following table in RoPE standard extensions:
INC-291382
Failing RoPE calculations
There were issues with failing RoPE calculations. They have now been resolved: deleting old Calculation Queue, Cycle Run, and Object Event items is now done in batches of 1000 to avoid timeouts and prevent excessive locking of the tables.
INC-290898
Enterprise Server
Error executing webservice – System Owners
We have fixed an error with executing the web service which occurred in the System Overview when selecting the System Owners.
INC-290074
Empty date in copy rules blocking access to all copy rules
We have fixed the displaying of copy rules with empty copy values and added validation before saving the data in the copy rule fields.
INC-287321
Event definitions failing to trigger object creation
There were issues with event definitions on object creation that sometimes was not triggered correctly. We have now fixed it.
INC-291739, INC-291282
ES Timer Service running but not updating Archive
We have applied improvements to the performance of the Audit Trail.
INC-284318
Security
Escaping customer settings
Customer settings are now properly escaped when read. This means that special characters (such as quotes, backslashes, or symbols) are correctly interpreted as part of the text value, preventing errors during configuration loading or processing.
INC-294059
Access modifiers and property security
We have enhanced the security measures in the access modifiers listed below, preventing the Property security configuration from being overwritten. This way, we avoid the disclosure of property values for properties that are protected by the Property security (which could only happen if the user had read access to the object under the business rules of the access modifier).
In the default configuration, the following Data Object Types have an access modifier set on the type definition:
- Access requests
- Activities
- Application onboardings
- Context assignment requests
- Context assignments
- Data update requests
- Delegations
- Evaluate identity violations
- Identities
- Onboarding contractors
- Onboarding employees
- Password reset enrollments
- Processes
- Provisioning tasks
- Resource assignments
- Resource folders
- Resources
- Survey templates
- Surveys
- Systems
The following access modifiers have been updated:
ActivityAccessModifierFullReadAccessModifierProcessAccessModifierProcessTargetAccessModifierCalculatedRolesAccessModifierContextAssignmentsAccessModifierContextIdentitiesAccessModifierContextObjectsAccessModifierDuplicateRoleAssignmentsAccessModifierIdentitiesAccessModifierIdentityContextsAccessModifierIdentityRequestableRolesAccessModifierIrrelevantRoleAssignmentsAccessModifierManagedIdentitiesAccessModifierManagedOrOwnedObjectsAccessModifierMyContextsAccessModifierMyDelegationsAccessModifierMySurveysAccessModifierObjectsWithIdentityPropertyMatchOrgUnitsAccessModifierOwnedContextsAccessModifierOwnedRolesAccessModifierOwnedSystemsAccessModifierPasswordResetAccessModifierResourceFoldersAccessModifierResourcesAccessModifierRoleAssignmentsAccessModifierSecondaryIdentitiesAccessModifierSystemRolesAccessModifierSystemRoleSelectionAccessModifier
Omada Provisioning Service
Purging mechanism for provisioning jobs fails
The purging mechanism for provisioning jobs could fail or time out when processing a large number of jobs. It has now been optimized to handle higher volumes efficiently and avoid failures due to timeouts.
INC-289117
Connectors
JWT sends empty fields resulting in invalid requests for some APIs
The REST OPS connector sent all standard headers and claims in the JWT token, even if they were empty. It was changed to contain non-empty headers and claims only.
OAuth2 Client Credentials certificate not recognized by ADP system
The Include certificate option in the REST connectivity was not respected for the authentication requests (when OAuth2 authentication was used). This has been fixed.
INC-290669