ServiceNow ITSM Relay
The ServiceNow ITSM Relay connector (Service Catalog) is based on the generic REST connector. See the REST section for the full description of tabs, fields, and configuration options. However, the connector only relays provisioning tasks to the external provisioning system. The ServiceNow ITSM Relay Connector (Service Catalog) allows to provision service catalog items from ServiceNow.
- Provisioning tasks consistently attain their final states (completed/failed) when the provisioning job is marked as completed or failed.
- For situations where all provisioning tasks should be created in a single request on the ServiceNow (SNOW) side (REQ), the connector always orders them using a cart, even if the job contains only one task. This ensures that result values remain consistent across all provisioning tasks.
Supported objects and operations
The following resources and operations are supported. The ServiceNow Relay Connectivity allows you to create and relay request and request item objects to ServiceNow, and indirectly manage access rights.
| Resource | Possible operations |
|---|---|
| Request | Create |
| Request item | Create |
| Service catalog item | Read |
Minimum required permissions
You need to have access to ServiceNow REST API. Depending on the client's configuration, you may also need access to an existing ServiceNow account with the user_admin role to manually manage sent requests.
Implementation notes
For information on how to build a developer ServiceNow instance, refer to the ServiceNow documentation.
Network requirements
The collector requires the port to the ServiceNow API endpoint to be open. The default port number for HTTPS is 443.
Prerequisites
Target system configuration
For the ServiceNow Relay Connector to work correctly, you need to configure ServiceNow portal to authorize Omada Identity user to log in using OAuth credentials. ServiceNow supports several ways of enabling OAuth authentication against their web services. Follow the steps below to set up the OAuth Password Credential authentication in ServiceNow and enable Omada Identity to access ServiceNow API endpoint.
- Log in as a system administrator to the ServiceNow administration portal and go to the Application Registry page.
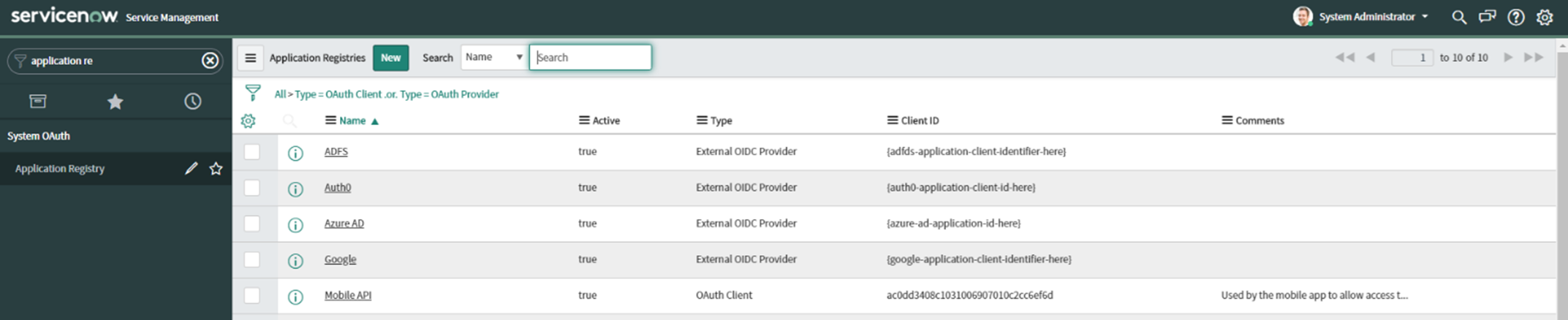
-
Create an OAuth API endpoint for external clients.
- Select the New button and select Create an OAuth API endpoint for external clients.
- Enter a unique name for the profile, e.g.,
OmadaClient. Click Submit. - Open the created object and make a note of the Client ID and Client Secret (The Client Secret can be read by clicking the lock next to the field).
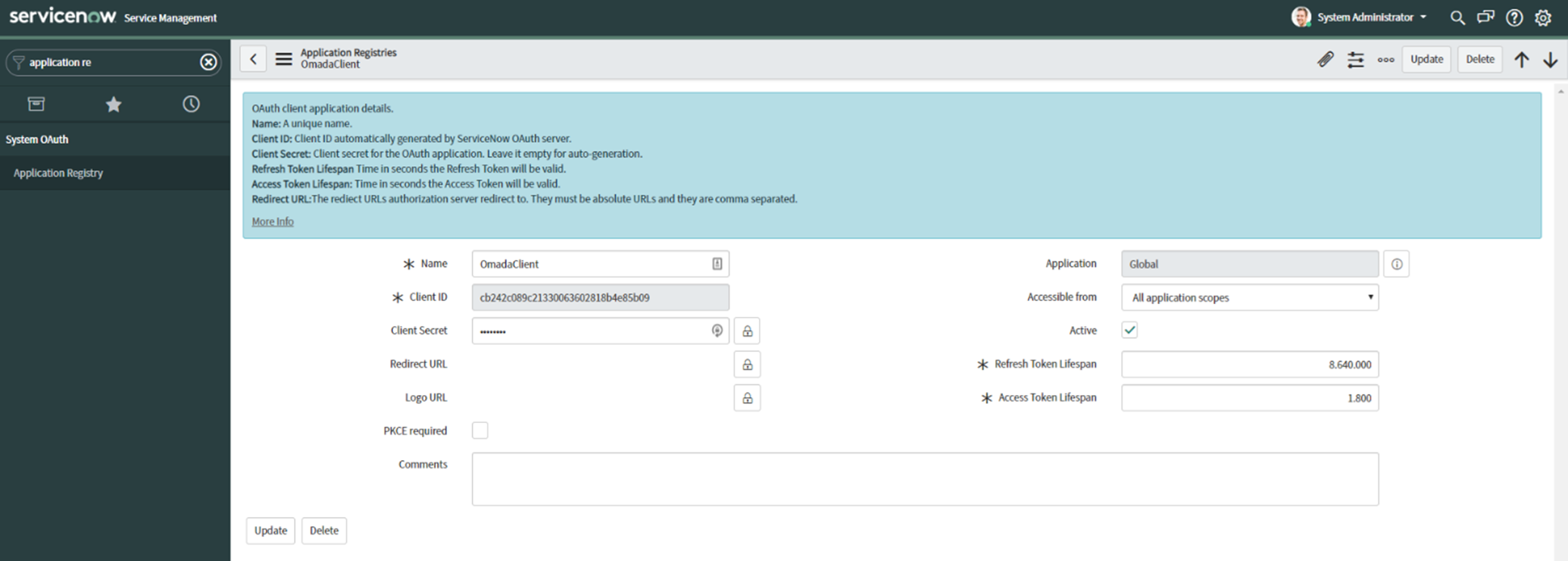
-
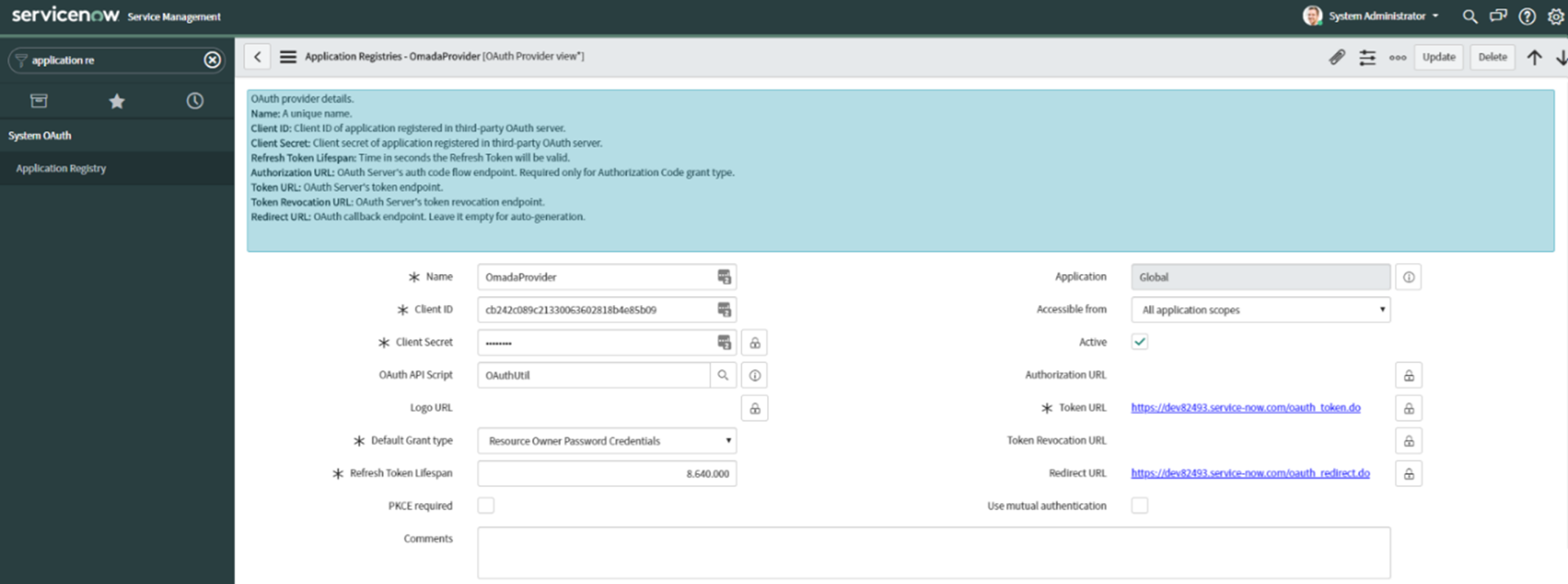
Create a third-party OAuth provider.
- From the list of Application Registries select the New button again and select Connect to a third-party OAuth Provider.
- Enter a unique name for the profile, e.g., OmadaProvider.
- Enter Client ID and Client secret values generated in the previous step.
- Set Grant type to Resource Owner Password Credentials.
- Specify the Token URL like this
https://[instancename].service-now.com/oauth_token.do.
Importing a ServiceNow account
System utilizing the ServiceNow ITSM Relay Connector (Service Catalog) requires importing ServiceNow account. Additionally, the service catalog items can also be imported or added manually in the Omada Identity. To enable importing service catalog items create a new resource type with the SERVICE_NOW_CATALOG_ITEM business key. Service catalog items mostly require additional attributes, which can differentiate from other resources, hence creating new resource type for imported resources with specific attributes is required.
Add a new query in the Queries and Mappings with the following configuration:
-
Object type:
Resource -
URL:
now/table/sc_cat_item?sysparm_fields=sys_id%2Cname%2Cdescription -
Description: Catalog items
-
Following mappings:
Destination Operator Source Business key map sys_id Security resource business key map sys_id Name map name Category constant ServiceNow Catalog Item Type constant SERVICE_NOW_CATALOG_ITEM
Add the requested_for attribute to each service catalog provisioned by the Omada Identity. The doesn't impersonate users, it uses technical account to create requests on the behalf of the beneficiaries.
-2ea44f)