Cisco Umbrella

This connectivity package provides support for managing users in Cisco Umbrella. This is a cloud-only service.
Supported objects and operations
| Cisco Umbrella | Omada Identity Data Model | Operations |
|---|---|---|
| Users | Accounts | Create, read, delete |
| User(roleId) | Resource assignments | Read |
Minimum required permissions
Read/write of user admin permissions must be granted when creating the API key. API Documentation: Umbrella Users and Roles API - Cisco DevNet.
Implementation notes
Users are the central object in Cisco Umbrella. A user can only have one role which must be defined upon creation of a user object with an integer representing the roleID of the role. Due to the limitation of the API (only allowing for POST, GET and DELETE operations), a user is created with a roleID. They must be deleted and recreated to change the roleId.
Network requirements
N/A
Prerequisites
-
Log in to
https://dashboard.umbrella.com/and navigate to Admin --> API Keys. -
Click API Keys and then, in the top right corner, click the + Add symbol.
-
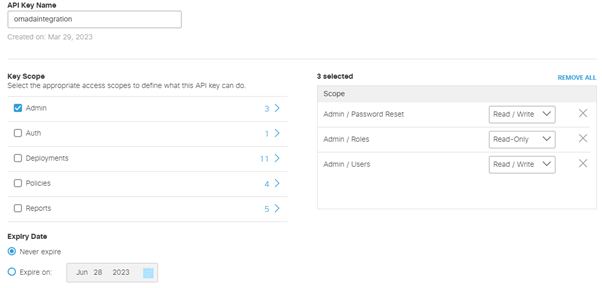
Provide an API key name and select read/write for the Admin Key Scope.
-
Click generate key. Add the key and secret to your vault of choice before clicking next (you won't be able to display them again).
Resource-driven attributes
Role assignments are managed via an attribute on the User object, and therefore the resource-driven attributes concept is used. After importing the Role objects to the Enterprise Server, use the following steps to set up resource-driven attributes:
-
Open each Cisco Umbrella resource
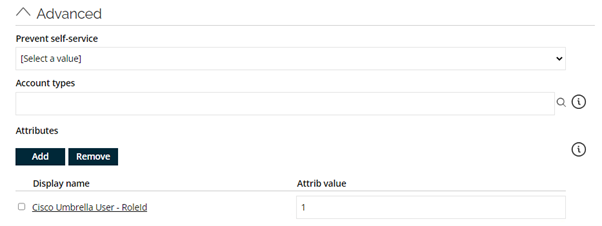
Resource Type = Cisco Umbrella Rolesand go to the Advanced section. -
Add the attribute Cisco Umbrella User - RoleId and fill out the attribute value with the value present in the Resource ID property:
-
Open the RoPE configuration file:
- On-prem:
\Omada Identity Suite\Role and Policy Engine\Service\ConfigFiles - Cloud: In the Cloud Management Portal, navigate to Environments. In the environment row, from the drop-down menu, select Configure. Choose the RoPE configuration tab.
- On-prem:
-
Add the following lines under the Attribute Value Resolver extension (change the key value in case you already have that specific key defined). Adopt the name of the account if you have not named the system Cisco Umbrella.
<add key="CiscoUmbrellaRole"
name="Cisco Umbrella Account:C_CISCOUMBRELLA_ROLE"
extraInfo="Type:ReferencePath"
value="/#ASSIGNMENTS_PER_RESOURCETYPE/Cisco Umbrella Roles:[C_CISCOUMBRELLA_ROLE]"/>
Request or assign access
The identity must be assigned both the Cisco Umbrella account and one Cisco Umbrella role. The above configuration of resource-driven attributes will copy the ID of the role onto the account when provisioned, which is required as the role is just an attribute on the user object in Cisco Umbrella.
Reconciliation
By having the role as a separate object and creating a resource assignment for it, you can import the actual state of both the account and the assigned role.
