Default settings
Manage personal users
By default, Omada Identity manages users for all employees and contractors. If there is a need for an identity with a different identity category, the user can be requested in an access request through the Omada Identity Account resource or any of the Omada Identity User Group resources, as the system is configured to auto create accounts.
Accounts
When creating a new account, if the properties culture, langId, or timeZoneId are not specified in the task mappings, their values will default to the corresponding settings in the customer configuration: DefaultCulture, DefaultLanguage, and DefaultTimeZone. For more details, refer to the Defaults section in the customer settings documentation.
To configure custom mappings, update the Omada Identity OData User task mappings within the Omada Identity system.
To assign fixed values to these properties, you can use expressions such as the following:
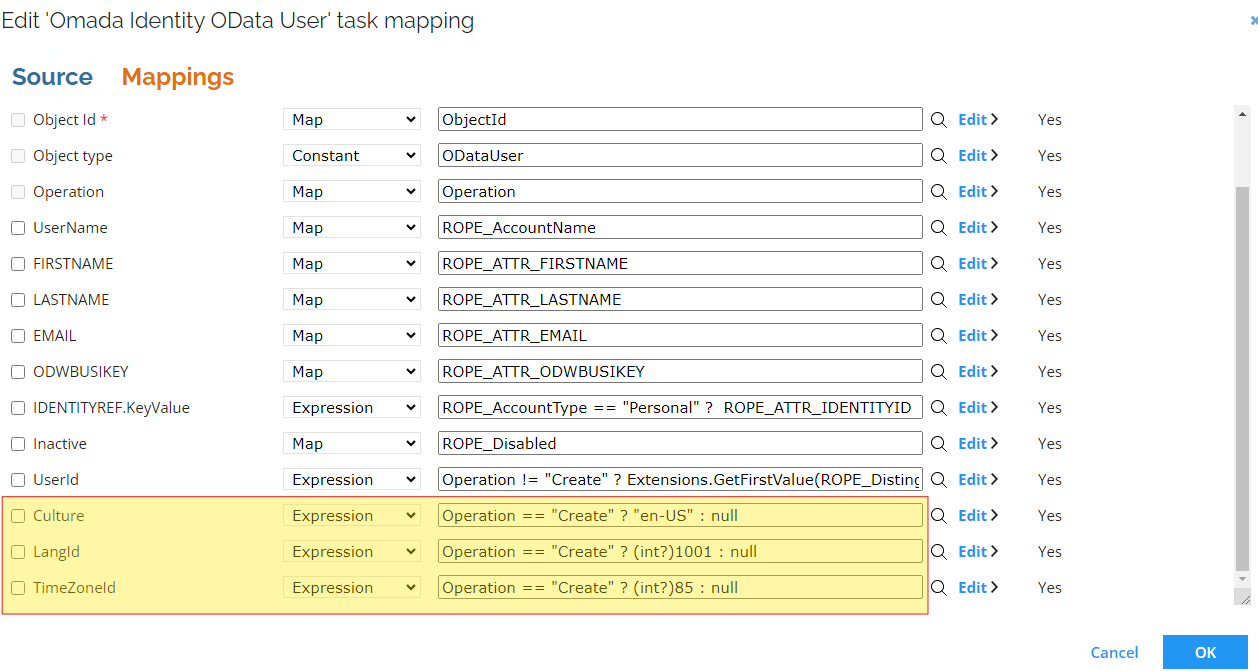
For information on how to populate the values for these properties, refer to the Data object types section in the OData API documentation.
System Category
The feature utilizes the built-in Omada Identity system category, dedicated for the Omada Identity system.
System
The feature is based on the built-in system Omada Identity. Even though it’s an internal system, the authentication of the service user is configured on the system for the collector and the connector to be able to communicate with the Enterprise server.
The new user provisioning and reading user and user group data that you've previously created is also used for the collector and connector configuration. Ensure that you select this user while configuring the settings.
-
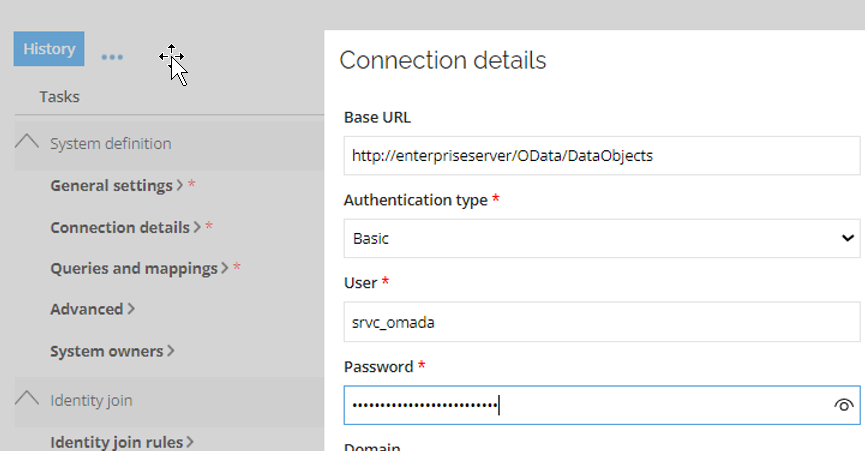
For the collector, go to System definition > Connection details and provide the Base URL pointing to the OData/DataObjects folder of the application, including credentials.
-
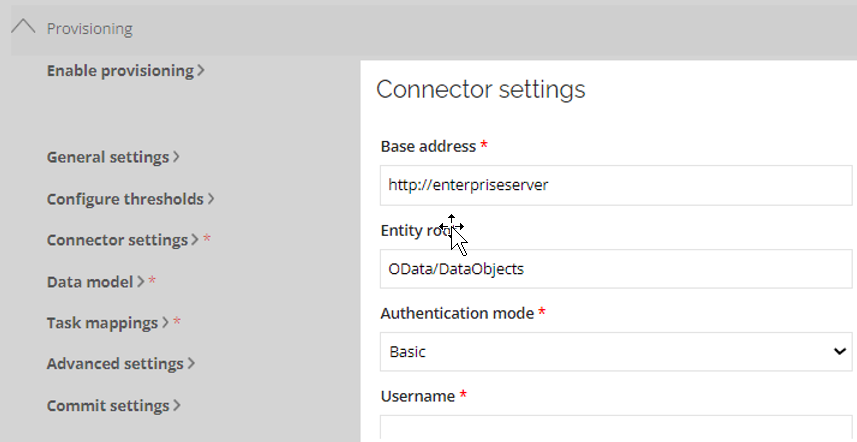
For the connector, go to Provisioning > Connector settings and provide the Base URL to the application, including credentials.
The feature comes with preconfigured collector and connector based on the OData connectivity.
Resource types
There are task mappings for the following two resource types:
- Omada Identity Account - mapped to the user (ODataUser)
- Omada Identity User Group mapped to user group membership (ODataUserGroupMember)
Other resource types used in the Omada Identity system, like the self-management resources are not used by the OPS provisioning and thus not mapped.
Once all accounts and permissions are in an approved state, you can enable the Exclusively managed setting on both Omada Identity Account and Omada Identity User Group resource types, allowing the compliance to be maintained automatically.
Resources
Each user group has a corresponding resource for managing user group membership. Creating a user group triggers creation of corresponding resource. You can find reference to the user group in the Advanced tab of the resource form.
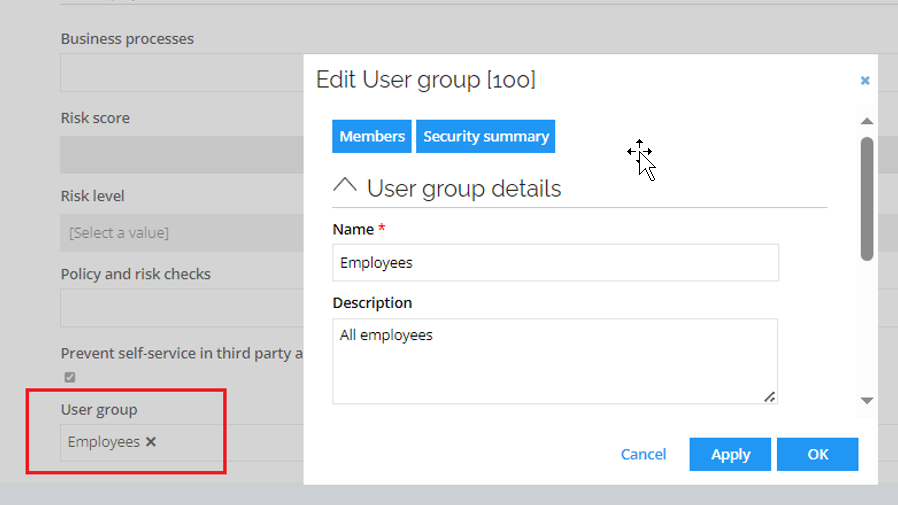
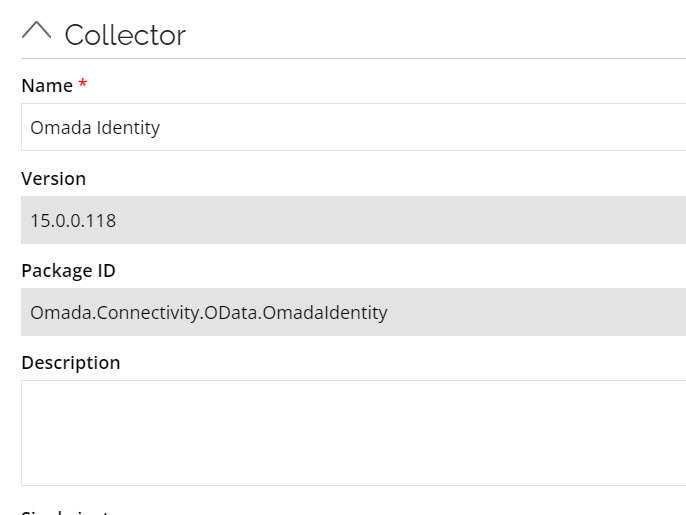
Collector configuration
The feature introduced a new OData based Omada Identity collector.
-
The
accountquery mapping utilizes the OData/User endpoint.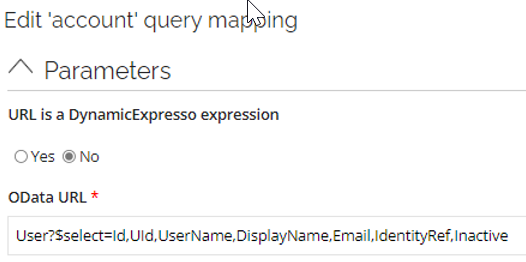
-
The
resourceassignmentquery mapping utilizes OData/UserGroup endpoint.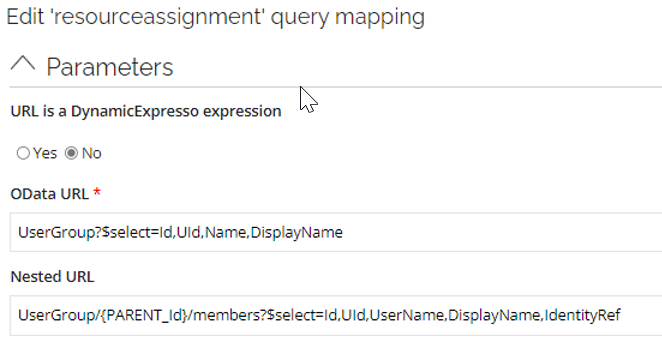
Connector configuration
The feature introduces a new Omada Identity connector.
The connector defines the following paths for updating user objects:
<object name="ODataUser">
<objectDetails>
<objectDetail name="ResourcePathGet" value="User/{UserId}" />
<objectDetail name="ResourcePathUpdate" value="User/{UserID}" />
<objectDetail name="ResourcePathCreate" value="User" />
<objectDetail name="ResourcePathDelete" value="User/{UserID}" />
<objectDetail name="VerbForCreate" value="POST" />
<objectDetail name="VerbForUpdate" value="PUT" />
<objectDetail name="VerbForDelete" value="DELETE" />
<objectDetail name="AnchorProperty" value="Id" />
...
For the user group memberships, the following paths are defined:
<object name="ODataUserGroupMember">
<objectDetails>
<objectDetail name="ResourcePathUpdate" value="UserGroup/{UserGroupID}/Members/{UserId}" />
<objectDetail name="ResourcePathCreate" value="UserGroup/{UserGroupID}/Members/{UserId}" />
<objectDetail name="ResourcePathDelete" value="UserGroup/{UserGroupID}/Members/{UserId}" />
<objectDetail name="VerbForUpdate" value="POST" />
<objectDetail name="VerbForDelete" value="DELETE" />
...
Import profile
The import profile Omada Identity references the Omada Identity system category.
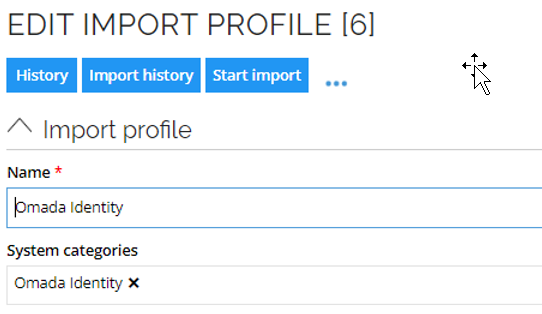
Schedule the daily import in a period with the least number of active users.
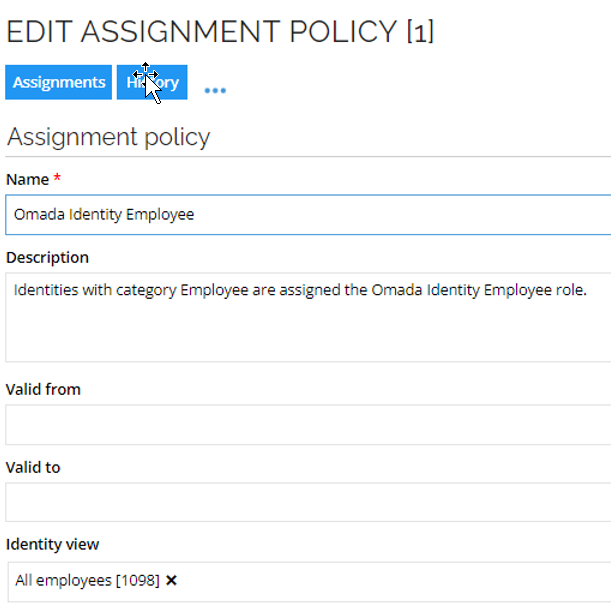
Assignment policies
By default, there are two assignment policies for employees and contractors.
-
Omada Identity Employee
-
Omada Identity Contractor
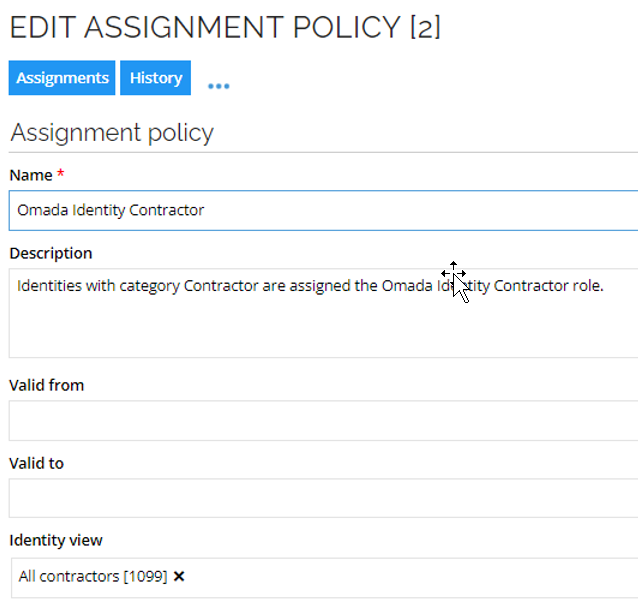
By default, the Omada Identity system is configured with automatic account creation so that all employees and contractors are granted an account and membership of the appropriate user group.
CIAM on-prem: As a CIAM user leveraging governance, you must create an assignment policy to add newly created identities from the Customers category to the CIAM end users user group.