Release highlights
We've just released Omada Identity update! What's new?
Launch of AI chat assistant
We're thrilled to announce the launch of our new AI-powered Documentation Chatbot, now available on the main page of Omada Identity Documentation.
The new AI-powered chat assistant significantly enhances productivity by allowing you to quickly access the information you need without navigating through multiple pages, making it easier than ever to find the details you’re looking for. It offers an improved user experience with its intuitive and user-friendly interface, making interactions seamless and efficient.
Key features:
-
Specialized assistance - our chatbot leverages a large language model using our comprehensive Omada documentation corpus. It focuses solely on delivering precise and relevant information from our extensive documentation.
-
Intelligent search - ask the chatbot any question related to Omada Identity Cloud, and it will provide:
-
Summarized answers: Clear and concise summaries of problems or instructions.
-
Follow-up capability: The chatbot retains the history of your queries, allowing you to ask more specific questions based on previous answers.
-
Documentation links: Direct links to the relevant sections of the documentation for more in-depth reading.
-
Read more links: Additional resources to help you gather more input on the topic.
-
Code examples: Practical code snippets when applicable.
-
Embedded images: Visual aids within answers to enhance understanding.
-
Copy functionality: Easily copy the provided answers by clicking the copy icon.
-
Feedback system: Provide feedback with a thumbs up or down. You can also leave comments or suggestions in the chat to help us improve the chatbot’s performance.
-
-
Multilingual support - the chatbot can translate responses into your native language or any other language you prefer, ensuring accessibility for a global audience.
We encourage you to explore our new AI-powered Documentation Chatbot and experience the ease and efficiency it brings to navigating Omada Identity Cloud documentation. Your feedback is invaluable as we strive to provide the best possible support and resources. The continuous improvement of the chatbot, driven by the feedback, ensures that we are consistently refining and enhancing its capabilities to better serve your needs.
New functionalities and version updates
Omada Identity Governance improvements
With this release, Omada Identity now enables the renaming of accounts, streamlining governance processes and providing increased flexibility in managing user accounts.
New Omada Identity Graph API
We've introduced new versions in Graph API that include:
-
New query calculatedAssignments designed to retrieve all calculated assignments data associated with a specific system, based on the provided systemID. Additionally, we've enhanced the accessRequests/childAssignments. Now, it exposes additional properties from the RoPE calculated assignments. Previously, the only exposed fields were the identity, resource, and parent resource.
-
We introduce a new query called accessRequestPolicyChecks, which provides users with a simulated policy check for assignments within the Access Request process. This query facilitates the execution of policy checks for the assignments requested for specified identities. To utilize this feature, it is essential to provide the ID of the identity along with the IDs of the resources requested for that identity.
Refer to Omada Identity Graph API documentation to know more.
New built-in user group for Omada Identity service account
We have introduced a new built-in user group: Provisioning users. This group is designed for managing users and user groups within the Data Object Security Model. By default, it has no authorization roles and a Medium authentication level.
For more information, refer to the Users and user group section in the Security documentation.
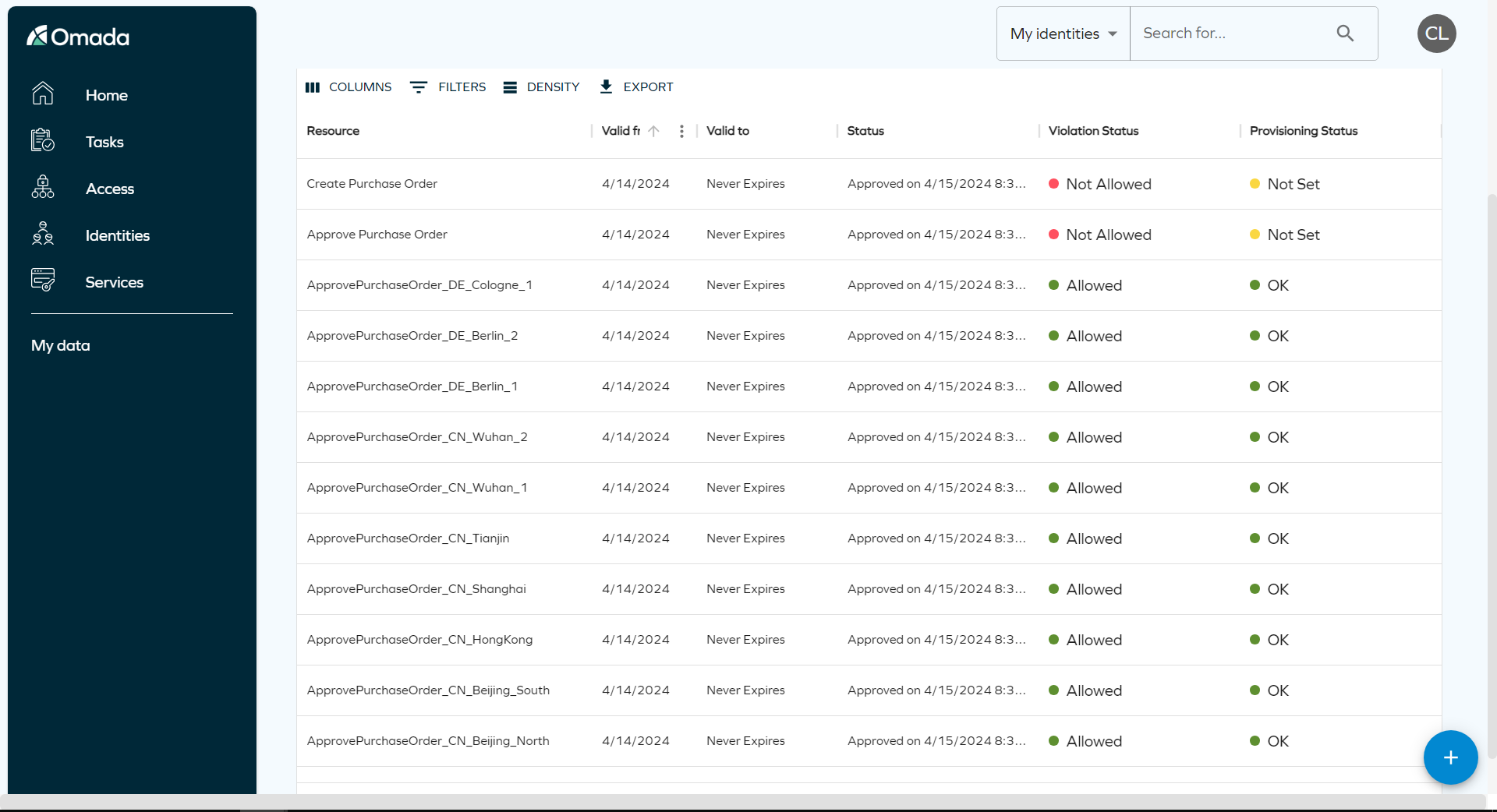
Access Request new columns: Provisioning and Violation status
We have enhanced the Access Request feature. Now, there are two new columns named Provisioning status and Violation status columns. Provisioning status shows the status of your request: Queued, Failed or Completed. The Violation status column shows if any violation have been found in your request.
Edit forms
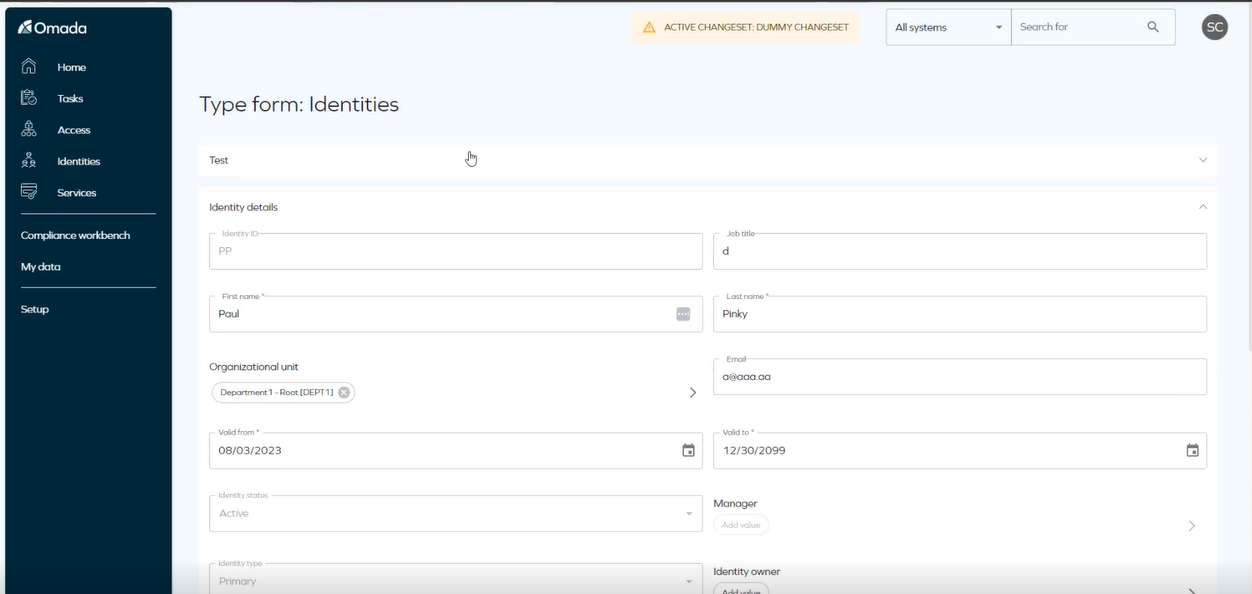
Omada Identity provides now the possibility to design forms. To do this go to Setup > Forms > Design forms. This will enable to create, edit, and delete forms related to different business processes.
If you want to know how to configure them go to Edit forms section.
Forms based on React components are designed to replace existing ones in the legacy UI. Navigate to Setup > Master Data,where you'll find a list of views (Identities, Resource Assignments, Resources, Account Types, etc.) and a detailed form for each item in the list. New React forms display an enhanced responsive form with modern controls based on the Graph API, simplifying the view (History and 3-dotted Actions menu are removed) for an improved user experience.
Script files are JavaScript snippets added to the form to extend its functionality. To prioritize security, scripting is deprecated in React Forms. This change is implemented to mitigate potential security risks associated with the scripting language. For users who have previously utilized scripting within forms, it is recommended to review and update forms to accommodate this change.
OpenID Connect Authorization Code Flow
We have added support for OpenID Connect Authorization Code Flow within Omada Identity. This enhancement empowers administrators to set up secure authentication, allowing users to utilize third-party logins like Entra ID and Okta to authenticate with Omada Identity.
With the Authorization Code Flow, Proof Key for Code Exchange (PKCE) is automatically enabled, ensuring robust security measures against potential attacks.
Detailed guidance on the OpenID authentication configuration is available in the Authentication and Single Sign-on configuration section.
Omada Identity Ansible package
We have introduced a new installation tool - Omada Identity Ansible package. This new tool is designed to help our partners and customers automate the installation of the on-premises version of Omada Identity.
With Omada Identity Ansible package, you can easily manage and configure your Omada Identity installation using Ansible's powerful automation capabilities.
For detailed instructions and further information, refer to the Omada Identity Ansible package documentation.
This feature is currently in Technical Preview. The goal of this preview phase is to gather initial customer feedback and ensure the feature reaches necessary parity with the Omada Identity Installation Tool.
Azure SQL support for Omada Identity
Omada Identity now supports running on Azure SQL. This enhancement allows you to leverage external databases from Azure SQL for your on-premises installation. For more information, refer to the Azure SQL databases section in the Installation guide.
Connectors
New Entra ID connectivity package
We have introduced a new supercharged connectivity package for Microsoft Entra ID that amplifies the management capabilities and elevates security. The package offers a wide range of out-of-the-box functionalities, allowing you to import information about users, groups, group memberships, and used licenses. You can also automate the provisioning and deprovisioning of Entra ID users, groups (Security, Teams, and SharePoint), and memberships. The connectivity package includes support for the delta import of users and groups, significantly reducing the time required for the import process.
This update introduces the following features:
Simplified provisioning
- Automated manager provisioning. You can provision managers directly into Entra ID, eliminating manual configuration.
- Resource owner management. You can map resource owners in Omada to group owners in Entra ID and assign users in both environments. This feature simplifies user assignments across both platforms, streamlining access control workflows for approvals and reviews.
Optimized group management
- Intelligent group mapping. The connectivity package intelligently excludes groups already synchronized from the on-premises Active Directory. It prevents duplicate entries and streamlines Entra ID groups.
- Enhanced group visibility. Create separate resource types for cloud-only groups within Entra ID. This provides a clear distinction between various group types (distribution groups, security groups, etc.) and allows you to easily exclude irrelevant groups from self-service access requests.
Teams and SharePoint support
- Centralized Teams governance. Manage your Teams directly within the Entra ID connectivity package (managing existing teams/access requests, requesting new teams).
- Simplified SharePoint management. Gain granular control over SharePoint site-level governance. Manage access and permissions without delving deeper into the SharePoint hierarchy.
Enhanced authentication and security
- Increased security with certificate authentication. Introduce an additional layer of security with certificate authentication for Entra ID, providing a more robust authentication method.
- Simplified cross-domain management. Manage multiple domains within Entra ID with ease thanks to our new default configuration support. Now, users in one domain can be members of groups in another domain, streamlining cross-domain collaboration.
We have also introduced an improved sign-in activity monitoring, allowing you to gain valuable insights into user activity with our new sign-in activity import feature (you can identify stale accounts and optimize your Entra ID environment accordingly).
SSH
We have introduced a new generic SSH connectivity package, allowing you to connect to a number of systems. See Secure Shell (SSH) in the Connectors section for details.
SAP Concur
We have added a new connector for SAP Concur that supports managing users and role assignments.
Functionality updates
New UI and paging options for the Generic REST, OData, and SCIM systems
Generic REST, OData, and SCIM systems have new, redesigned Queries and mappings form. In the new UI, available options are grouped into tabs:
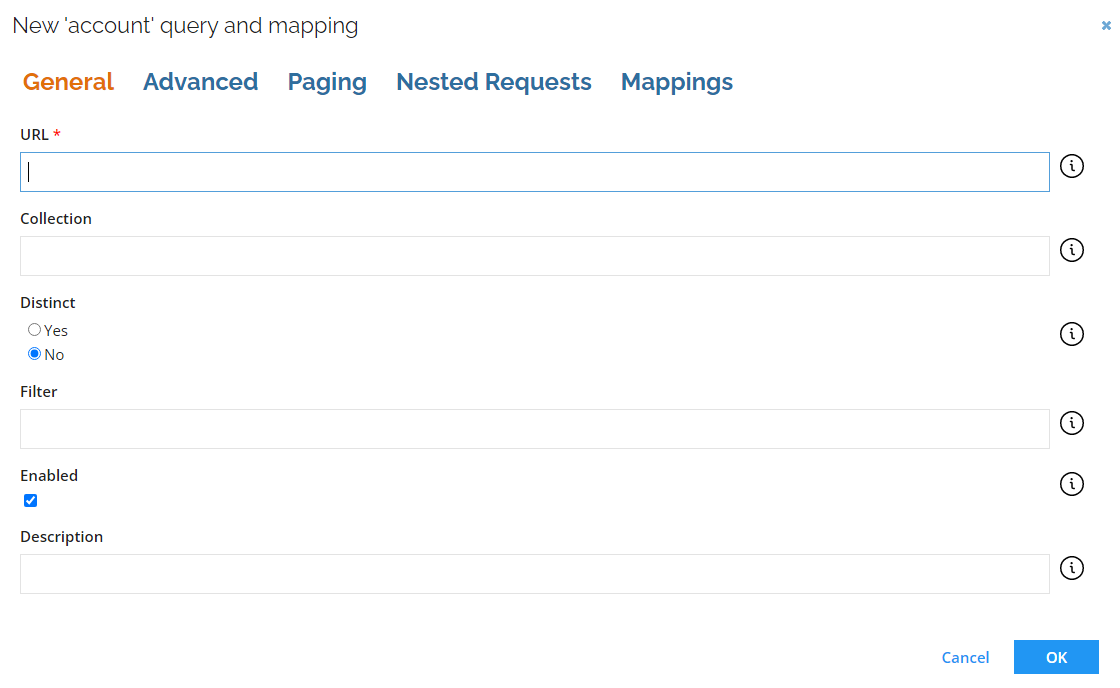
All collectors using generic REST, OData, and SCIM, which do not have customized JS files, are also affected.
We have also introduced the following new features:
-
Adding headers to the query request
-
You can now specify headers at the query level, ensuring they are attached solely to requests for that specific query. This feature can be found in the Advanced tab:
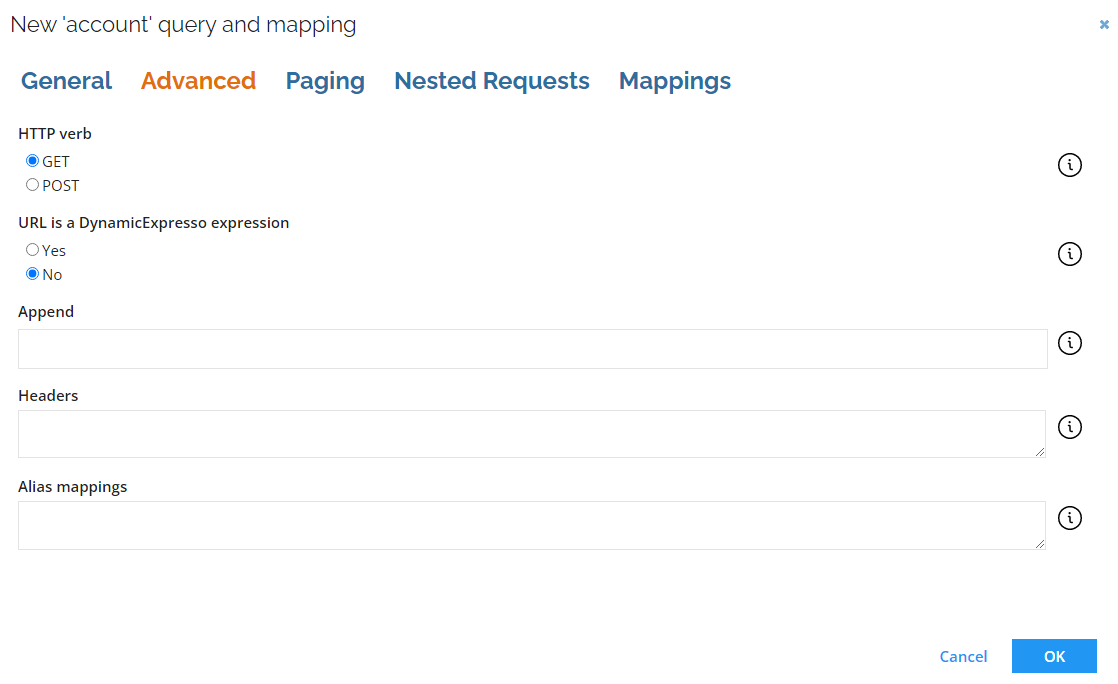 info
infoPreviously, custom headers could only be added in the Connection Details section, leading to them being included in all requests. Although still an option, you can continue to specify headers for all requests in the Connection Details section.
-
-
Paging per query
-
You can now set, change, or disable paging at the query level. This option is available in the Paging tab:
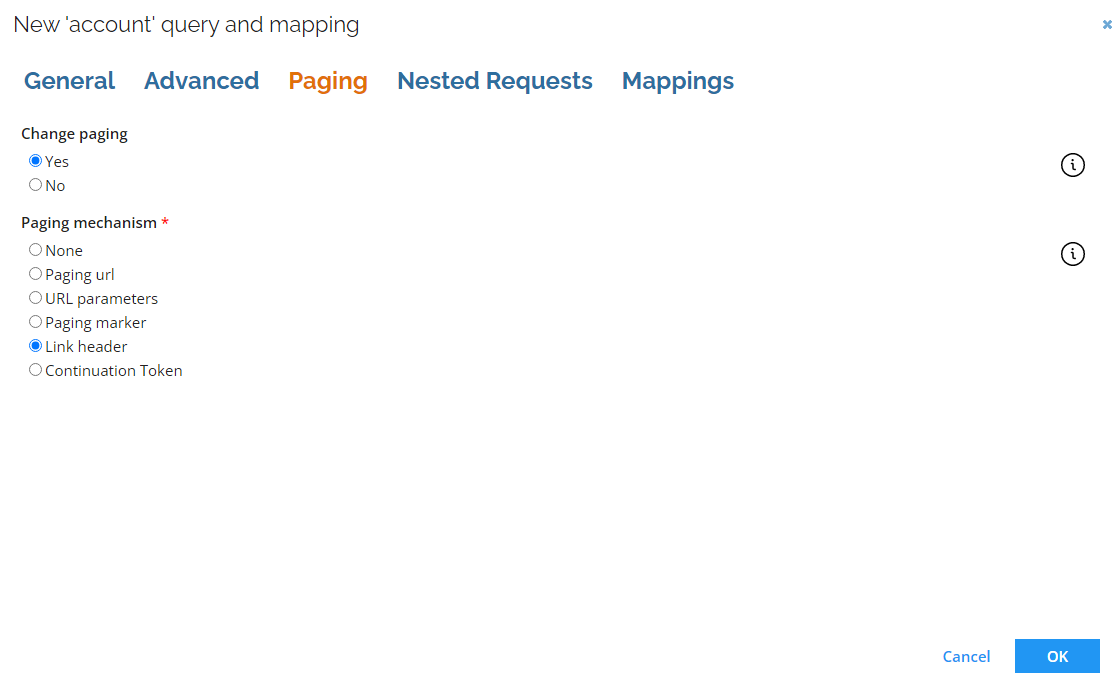 info
infoThis option offers the same paging options and types found in the Advanced form You still can specify paging for all requests in the Advanced form.
-
-
Paging for nested requests
-
You can now change or disable paging type for nested requests:
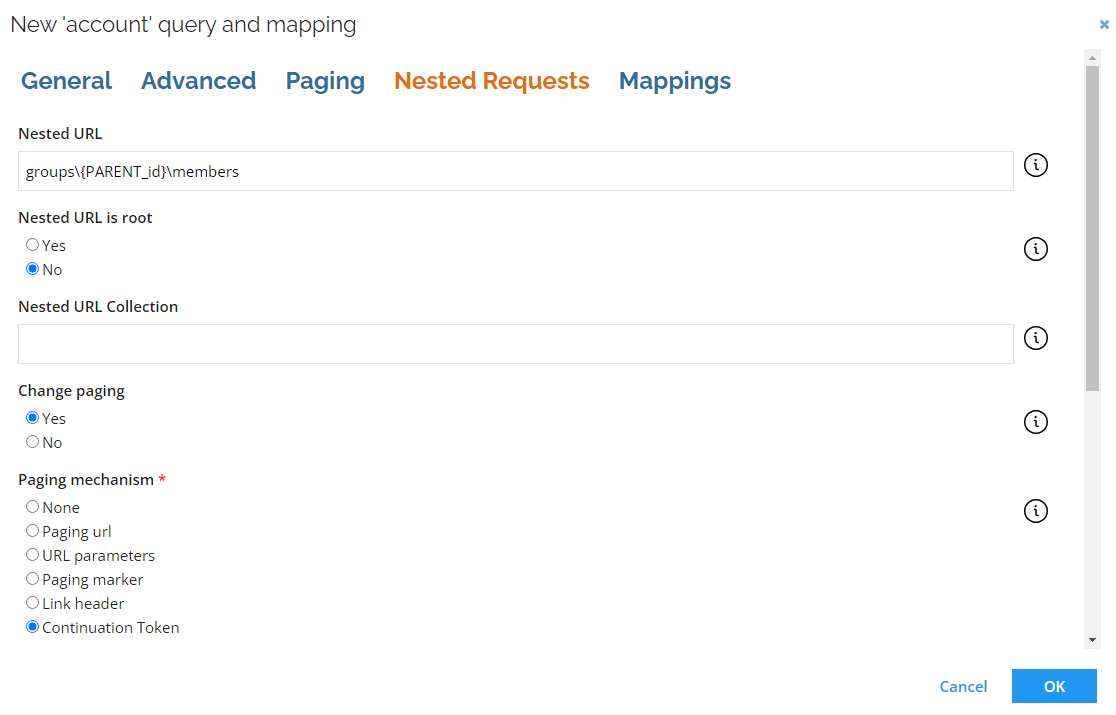
-
OPS REST Connectors upgrade: JSON paths & request templates
We have enhanced the OPS REST and REST-based connectors with the following options:
-
Introducing support for JSON paths property names, denoted by $. (dollar and dot), such as $.name, for example:
<properties>
<property name="$.added[0].loginId" />
<property name="$.added[0].roles" multiValued="true" />
<property name="$.added[0].sampleArray" multiValued="true" />
</properties>-
JSON path properties now support updating field values in the request. This includes both plain text and nested JSON structures. When a JSON value is provided, the connector constructs the entire structure in the specified location.
noteYou can combine existing properties with JSON path properties to enhance flexibility. JSON path properties are applied at the end, atop the prepared request. JSON path properties can only be used if the JSON already contains the field identified through the path. They cannot be used to create new fields, making this feature particularly valuable for reconciliation scenarios or when utilizing request templates object details.
-
-
Possibility to use request templates
-
Now, JSON request templates can be defined per operation within object details. The convention for detail names is
{Operation}Request, for example,CreateRequest. These templates are stored in large data fields, enhancing customization and organization for each operation, for example:<object name="SampleUser">
<objectDetails>
<objectDetail name="CreateRequest" >
<largeDataField>
{
"added":[
{
"organization":{
"name":"my company",
"type":"Company"
},
"roles":[
{
"name":"Role 1"
},
{
"name":"Role 2"
}
],
"sampleArray":[],
"loginId":"myLogin"
}
]
}
</largeDataField>
</objectDetail>
-
Microsoft Exchange Online and Hybrid - support for distribution/mail-enabled groups
We have introduced distribution/mail-enabled security groups management in Microsoft Exchange Online and Hybrid connectivity packages.
Support for the CreateIfNotExist operation
We have also added the support for the CreateIfNotExist operation in a range of connectors. The operation checks if the object already exists before attempting to create it.
UI updates and improvements
New Form and List actions
We have improved the Form and List actions for the following features: Access Request, Request Password, and Add Classification Tags in both form and list actions. These new Form and List actions will allow you to trigger either a new Access Request flow or the existing Reset Password flow with the selected identity already chosen.
This update includes actions such as Edit, Delete, and Recalculate in the new UI layouts. These actions can be displayed in a menu, toolbar, or row menu. You can find the Form and List actions in List Views, which are located in the left main menu, under the List Views (Beta) menu item.
The functionality of Form and List actions has been standardized and is based on system configurations. So creating JavaScript events or using displayEvaluator has been deprecated from the form.
New UI in the Compliance Workbench dashboard
We have introduced a new User Interface (UI) in the Compliance Workbench. This includes system overview that shows the overal compliance state for all applications in the solution, as well as a System list with all the information for the systems.
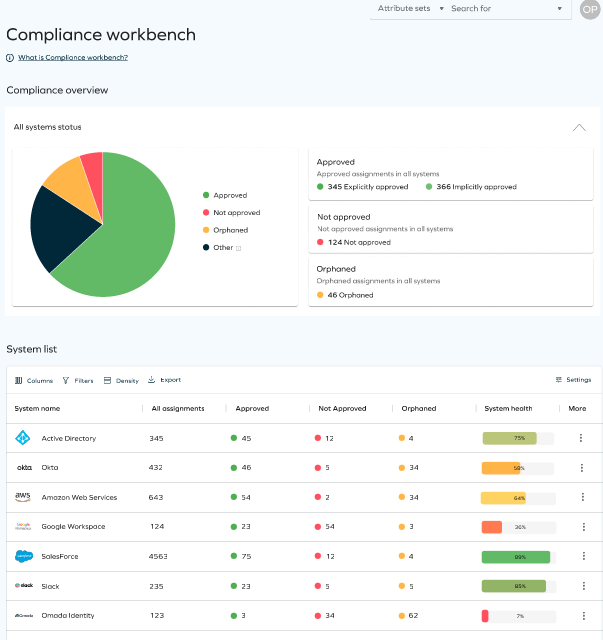
In this new Compliance Workbench, you will see the following columns:
- System name: This column shows the name of the system.
- All assignments: This column displays the total sum of all calculated resource assignments for each system.
- Explicitly approved: The calculated resource assignments that are approved.
- Implicitly approved
- Not approved: The calculated resource assignment only exists in the connected system - there is no desired state for it.
- Orphaned: he calculated resource assignment belongs to an unresolved identity, or the Data Warehouse is uncertain of its ownership.
- System health: This column reflects the current health status of the system, indicating the level of risk associated with its operation. The health status is categorized into three levels: high, medium, or low risk. These states (compliant and non-compliant) can be configured in the Compliance Workbench configurations.
- More: It allows you to open the configured surveys for the chosen system. When you click on one of the reviews, the initiated survey opens in a new tab.
There are some column statuses that are hidden by default:
- In violation
- Pending deprovisioning
- Implicit assigned
- None
We have implemented numerous new features designed to enhance your experience within the updated Compliance Workbench flow. For further details on these enhancements, consult the Compliance Workbench article.
You can find the legacy Compliance Workbench under My Data menu.
:::
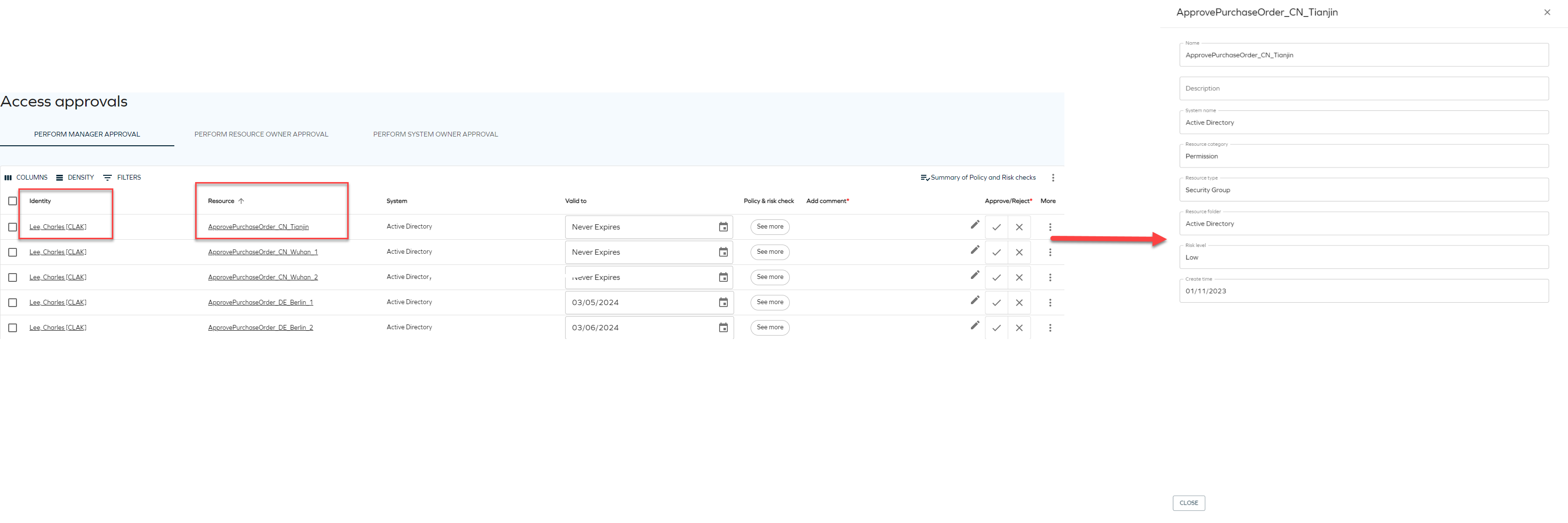
Access approval new pane
We have introduced a new panel in Access Approval. Now, you can click on underlined text representing a resource or identity, and a sidebar will display additional information about that identity or resource.
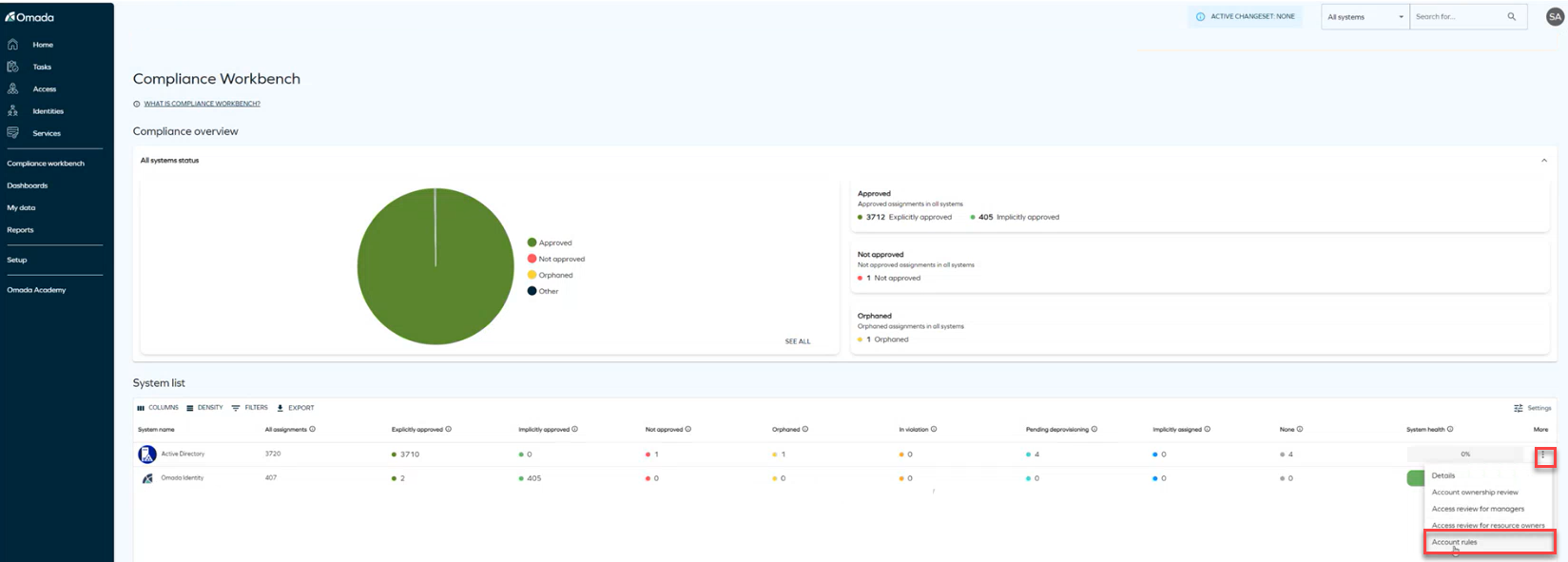
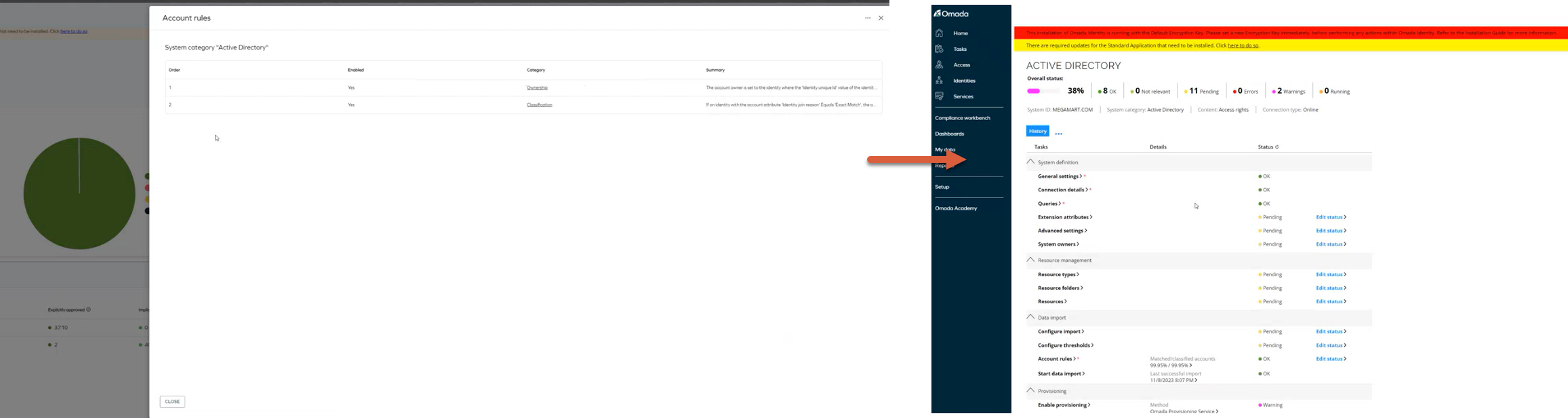
Account rules in the Compliance Workbench
We have enhanced the Compliance Workbench by adding a new option to view Account Rules in a read-only mode for each system row. Clicking on the Account Rules will open the Account Rule window, allowing you to view them.
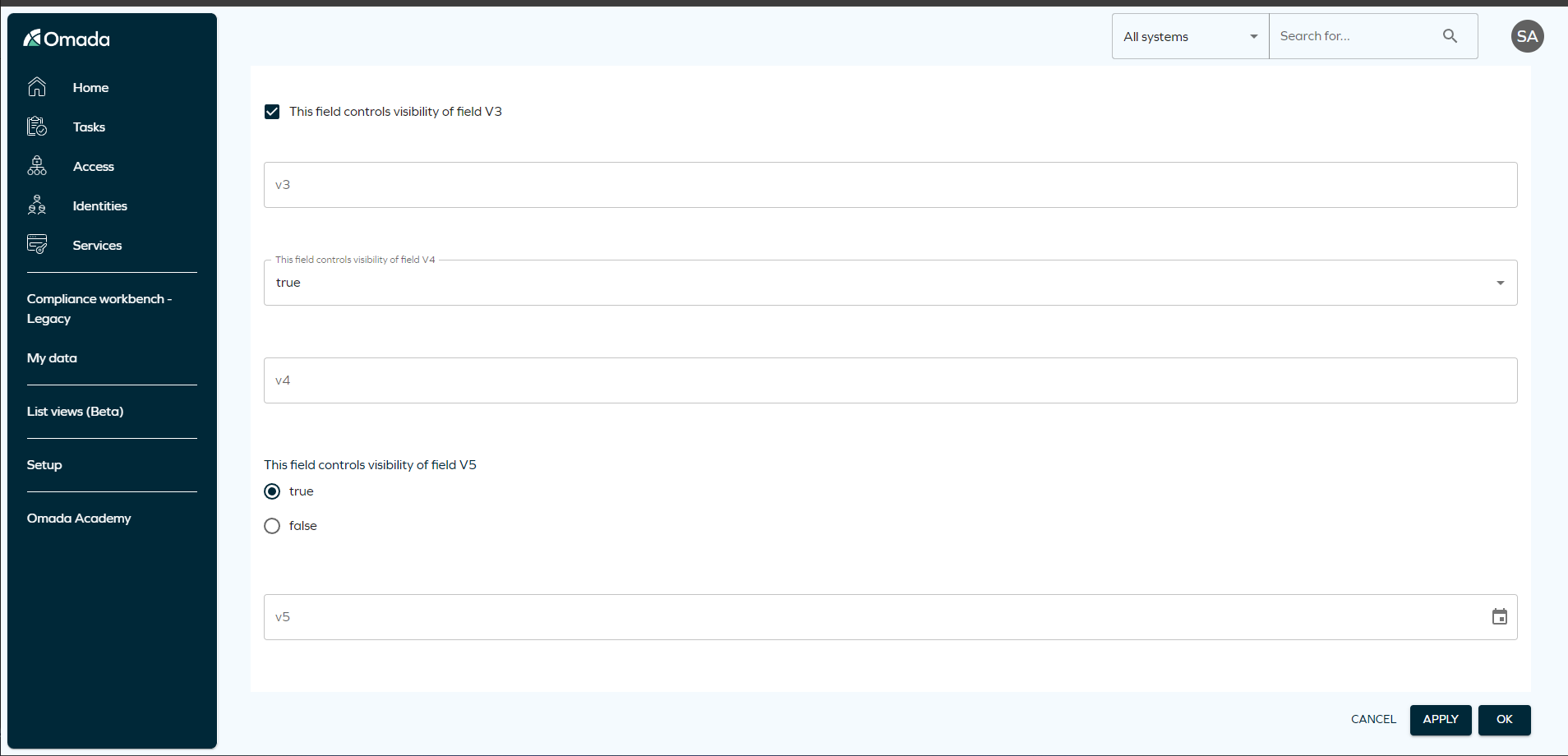
Visibility depends form in new UI
We have introduced the Visibility depends on field in new UI forms. Now, you will be able to define the visibility conditions for each configured form section or field in the new UI.
Brand colors
We have updated our product to allow customization of colors. Now, you can personalize accent colors for buttons, backgrounds, and highlights. The focus on brand colors assists in adhering to WCAG 2.2 Level AA accessibility requirements, ensuring inclusivity and accessibility for all users.
Collapsible menu
We have made some enhancements to the main menu.
You can now collapse the main menu while using Omada Identity, giving you a more streamlined and customizable interface.
New icons:
- Compliance Workbench
- My data
- List views
- Setup
- Omada Academy
We've introduced a default icon for any links that admins add to their menus. Other icons can be selected from the collection we supplied in the Omada Identity New UI menu icons
Cloud Management Portal Icon Update
Coming soon customer admins could upload a new, square icon in the Cloud Management Portal, within the configuration menu of their cloud environments. We've added a secondary image upload option there. If there is no secondary icon, the menu will fall back to shrinking the existing icon. While it is not critical to upload a new one, it is recommended for the best visual experience.
We hope these updates enhance your productivity and overall experience with Omada Identity.
Beneficiaries renamed to Identities in Access Request and Extend access features
We have updated the term beneficiary to identity in the Access Request and Extend Access flow to maintain consistency throughout our product.
Never expires in Details pane in Access Approval
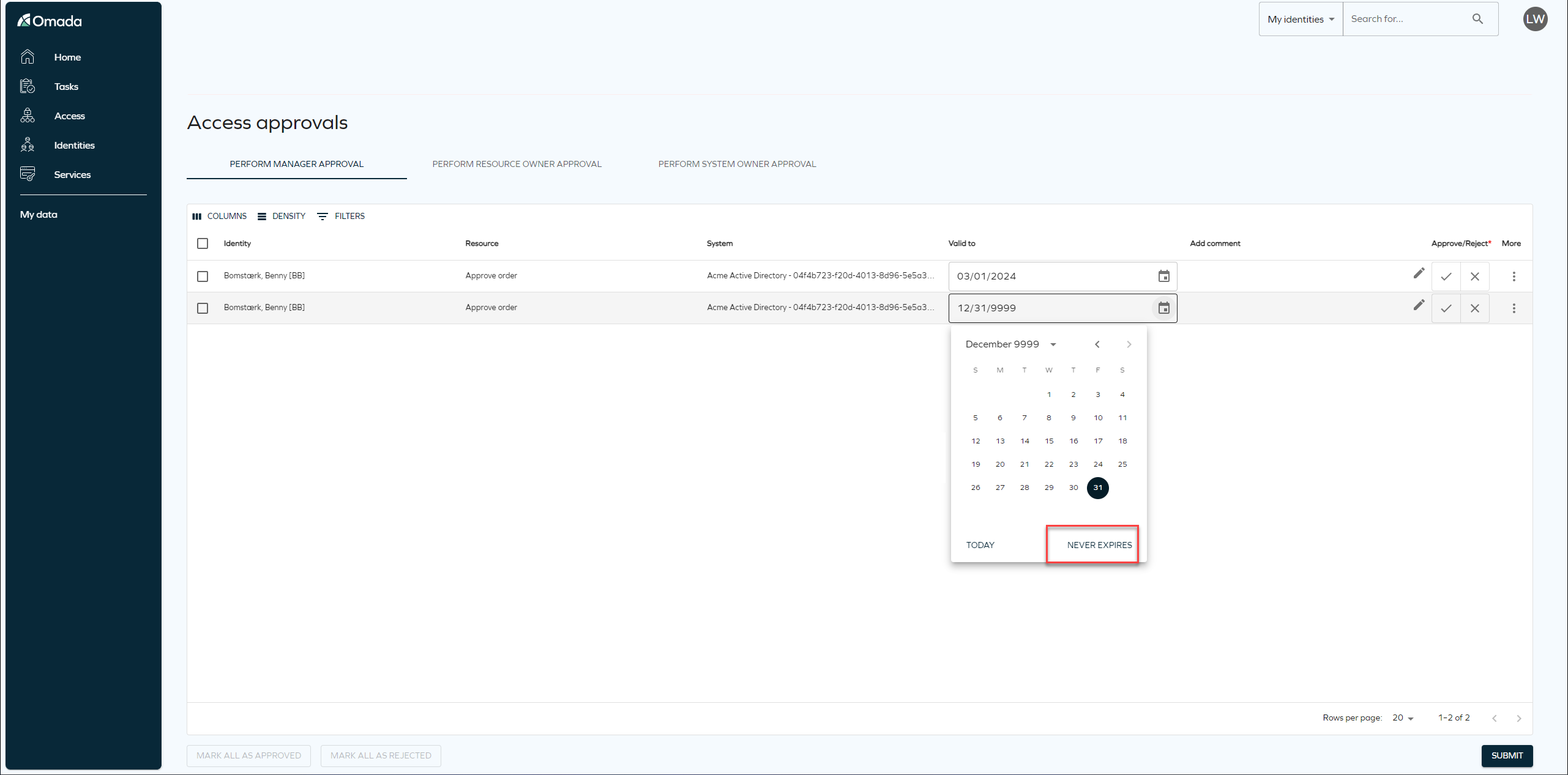
We have updated the Details pane in Access approval to show Never expires instead of 12/31/9999.
Read more about this change in March Release notes.
Account types
We have enhanced the Account type feature for requesting access. Now it is possible to:
- View the account type for each beneficiary.
- Assign the appropriate account type if a beneficiary matches the resource account type.
Enhanced mail delivery handling for connection errors
We've improved our mailing delivery system to prevent unnecessary retries when encountering connection errors to the email server. Instead, emails will remain in the mail queue until a successful connection is established, ensuring efficient and reliable delivery.
For more information on the Mail queue delivery retries setting, refer to the Mail section in the Customer settings documentation.
Enhanced Omada Identity Portal SSO with OpenID Connect Protocol
We have updated the internal components utilized for the Omada Identity Portal Single Sign-On (SSO) system, using the OpenID Connect protocol.
For more information on OpenID and OpenID Connect, refer to the Authentication and Single Sign-on configuration documentation.
Policy and Risk checks in Access Request
We have enhanced the Access Request flow by introducing Policy and Risk checks. These enhancements allow administrators to configure the Policy and Risk checks to be mandatory or optional when requesting access, ensuring compliance and security in the workflow. Once configured, these checks automatically execute when advancing to the next step of the Access Request process. If it is set to optional, users can manually trigger these checks.

To configure the Policy and Risk checks in Access Request, see the Access Request section.
Enhanced performance for Access Requests and Approvals
We have boosted performance for surveys. Now, approvals for surveys are completed faster.
Valid to Never expires
We've enhanced the Valid To functionality. Previously, when an identity had unlimited access to a resource, the Valid To field displayed 12/31/9999. We've now update it to read Never expires for clarity and usability.
With this change, when requesting access, you'll notice the new Never expires button option. Selecting this signifies that the identity will have unlimited access to the resource, streamlining the access management process and providing a more intuitive experience for users. This change will roll out for Access Approvals in a future cloud update.
Reassignment logs
We have enhanced the survey logs views and introduced the option to display reassignment logs. Click the Reassignment Logs button to open a dialog that shows all the reassignment logs.
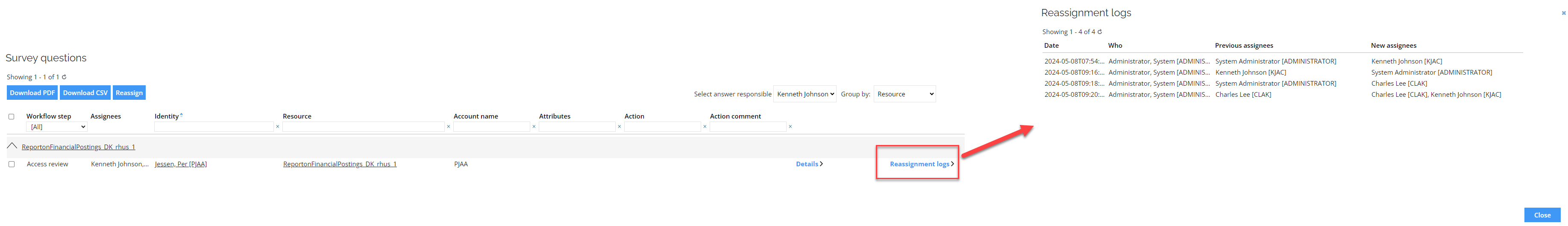
- This feature is available only for administrators.
- Reassignment logs will be visible only if the survey status has not been initiated.
Improved reconciliation of calculated accounts
We have improved the reconciliation of calculated accounts. With the introduction of the Reconcile account name setting within the account resource type, you can now ensure consistency by enforcing the account name during provisioning updates.
For more information, refer to the Resources section in the Import and onboarding guide.
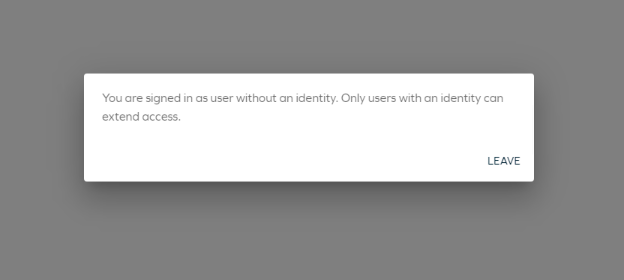
Extend access warning message
We have introduced a new warning message to notify users that extending access is not possible without an identity.
Exporting CSV
We have added significant improvements of the performance of exporting surveys to CSV and PDF. You can now export large files without experiencing any delays.