Compliance Workbench
Compliance Workbench is a type of user's dashboard that allows System Owners and Auditors to ensure that a system or application is compliant. It presents an overview of the compliance statuses of all the resource assignments for each system or application.
To display the Compliance Workbench, go to My data > Manage > Compliance Workbench.
Compliance Workbench fulfills the following main tasks:
- It shows resource assignments grouped per system and their compliance status,
- It provides a fast overview of the compliance state of all systems included.
Moreover, this interactive dashboard allows the users to:
- Get detailed information about the resource assignments,
- Start recertification, for example, access or account ownership survey.
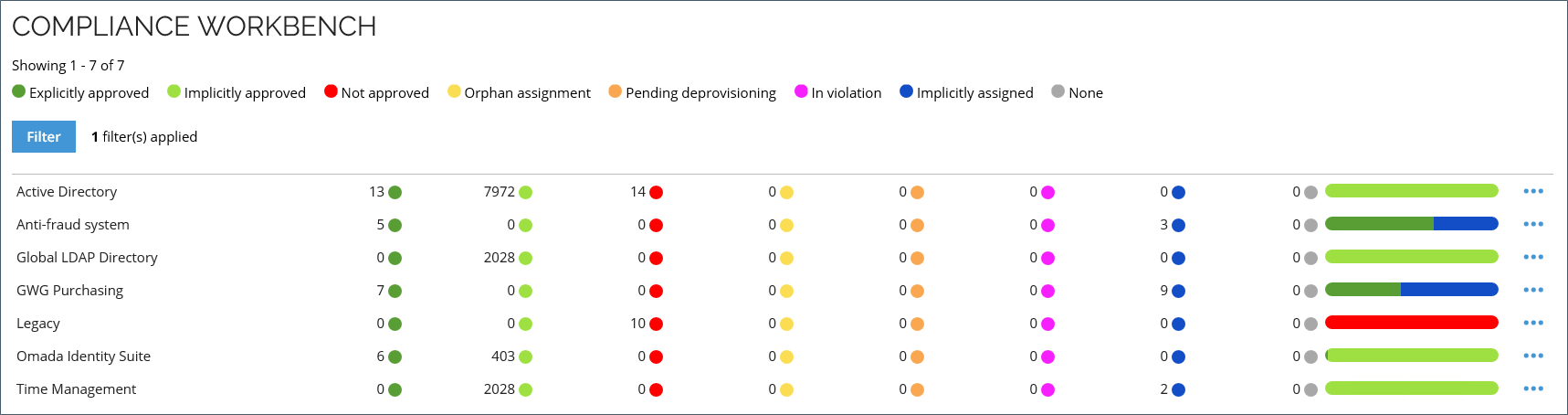
Compliance statuses
Compliance Workbench provides graphical information on the status of the calculated resource assignments. Each status is defined by a different color in a separate column.
Explicitly approved (Green)
The calculated resource assignment is the outcome of a direct assignment, or it has been approved in a survey.
Implicitly approved (Light Green)
The calculated resource assignment is the outcome of a policy or a child of an assigned enterprise or application role.
Not approved (Red)
The calculated resource assignment only exists in the connected system - there is no desired state for it.
Orphan assignment (Yellow)
The calculated resource assignment belongs to an unresolved identity, or the Data Warehouse is uncertain of its ownership.
Pending deprovisioning (Orange)
The calculated resource assignment awaits to be deprovisioned.
In violation (Violet)
The calculated resource assignment violates a constraint that has not caused it to be disabled because a pending evaluation procedure exists for the violation.
Implicitly assigned (Blue)
An enterprise or application role, which is not in violation, is implicitly assigned.
Implicit assignments are created for enterprise and application roles if the Role and Policy Engine detects that identity is assigned to all the contents of the role - but not the role itself.
This is done to allow Separation of Duties constraints to be defined on the enterprise or application role level.
None (Grey)
Not possible to express a meaningful compliance status for the assignment. For example, a calculated resource assignment that is disabled and has no actual state reasons has status None because it is irrelevant from a compliance perspective.
Details of Compliance
Compliance Workbench allows you to drill down to the details of each of the calculated resource assignments of each of the onboarded systems and examine involved resources, identities, reasons, or attributes.
The following diagram presents the graphical overview of the details provided by the Compliance Workbench.
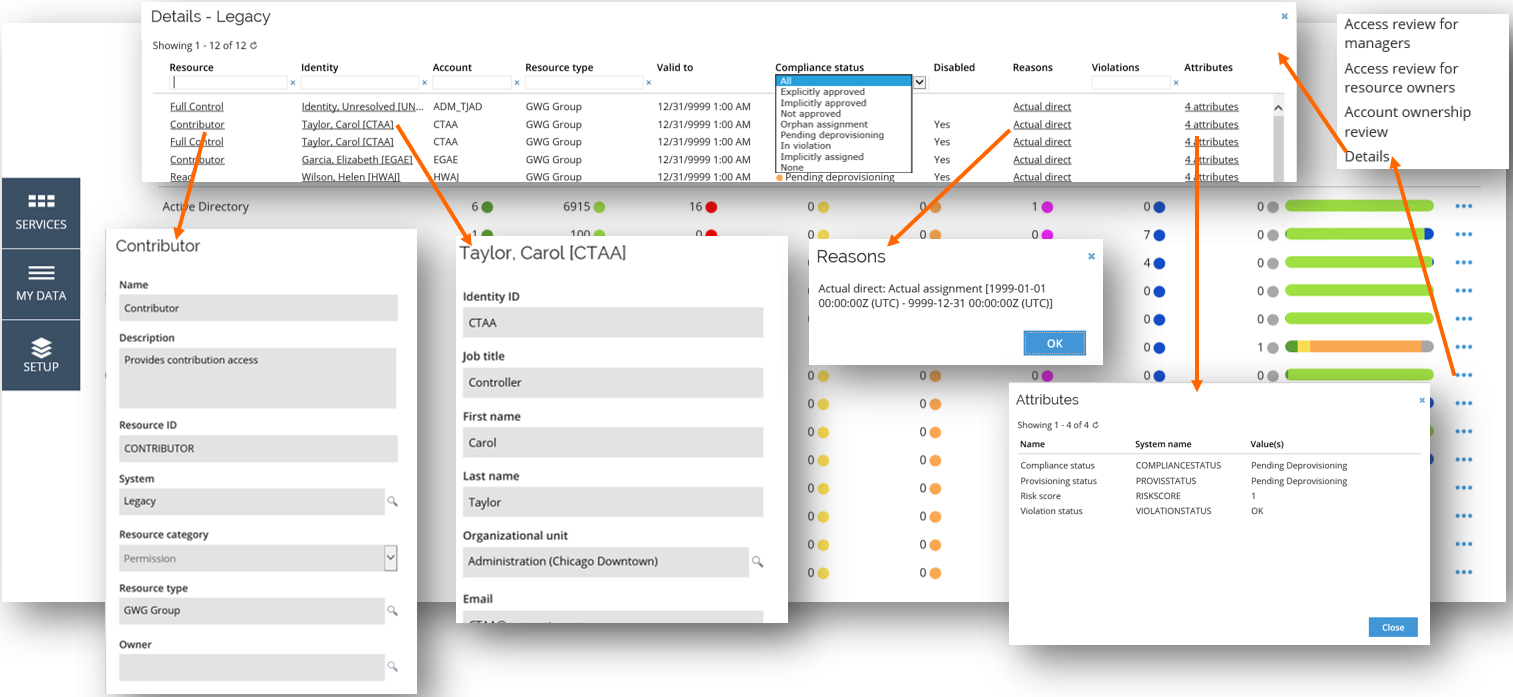
To open the details of the desired system, click the ellipsis menu on the right-hand side of the Compliance Workbench.
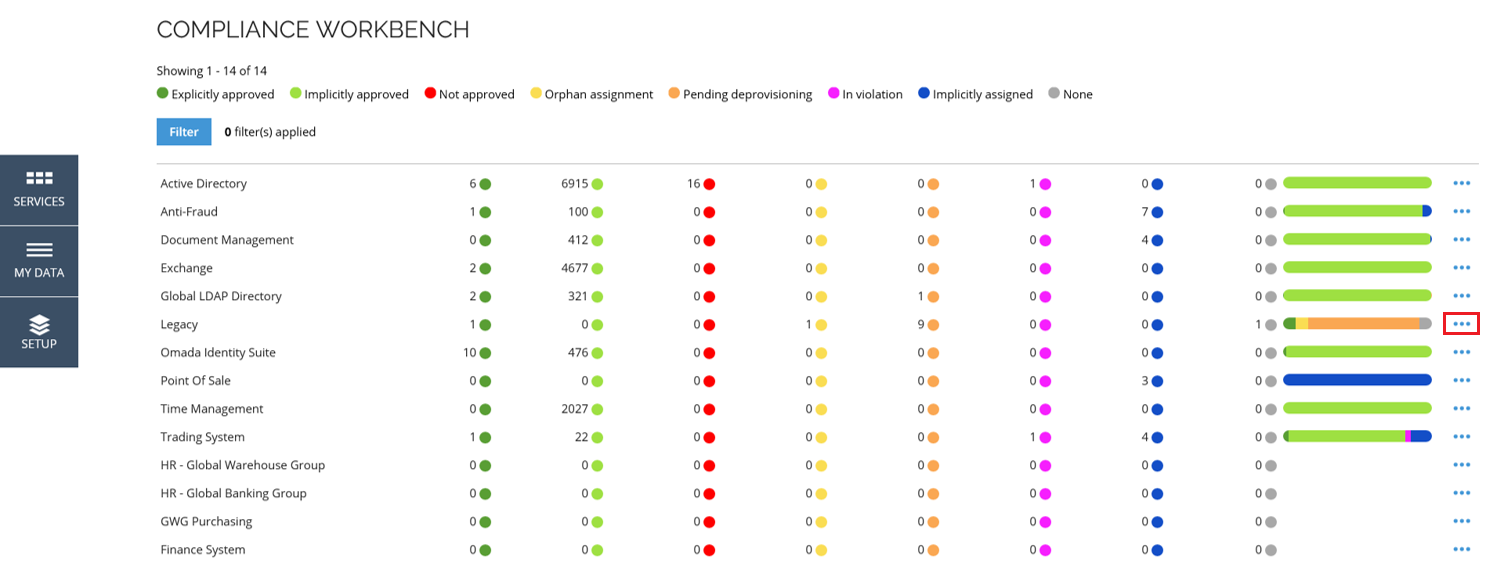
From the menu, select the Details option. This will open a new window with the details of the selected system.
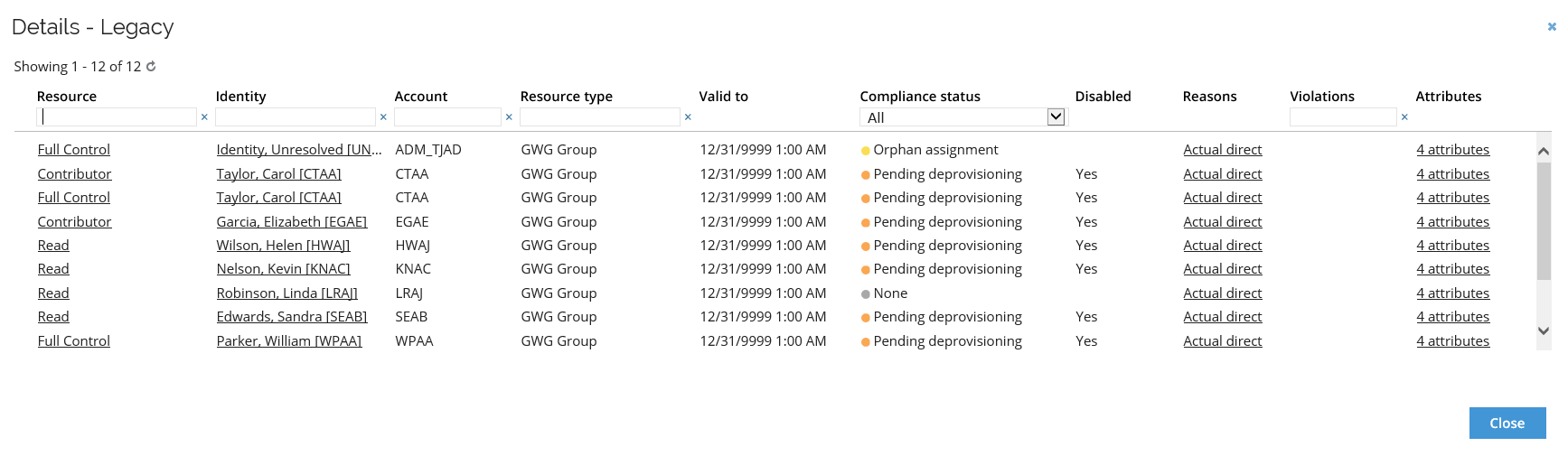
Each column of the Details window allows you to sort and filter the calculated resource assignments. You can also filter out only one compliance status using the Compliance status drop-down menu.
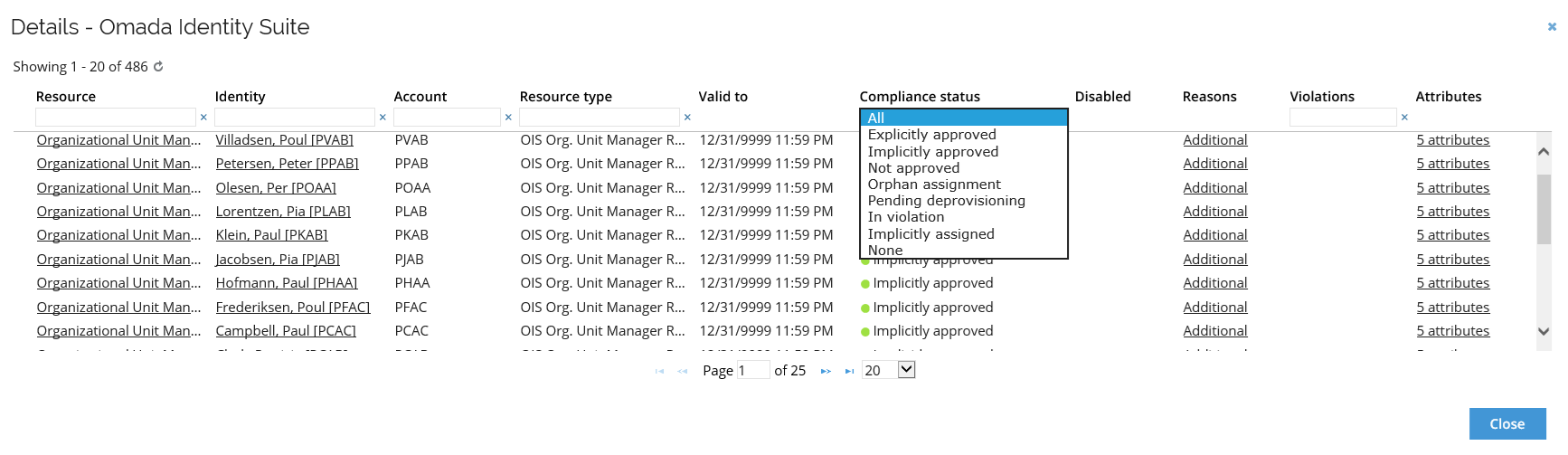
The Details screen of the system also allows you to view the specifics of the Resources, Identities, Accounts, Attributes, and Reasons relevant to a particular compliance status of the caluclated resource assignment.
To view these specific data, click on a given element on the list, and a new window with the appropriate information will be displayed.
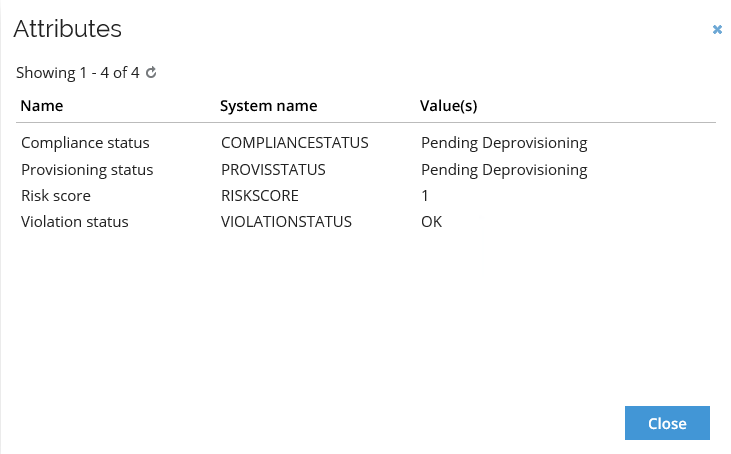
Account Rules and Compliance
Compliance Workbench also gives you access to review the Account rules applied in a onboarded system, as well as, filtering out the system itself.
You can filter out a desired system by clicking the Filter button in the top left-hand side corner of the Compliance Workbench.
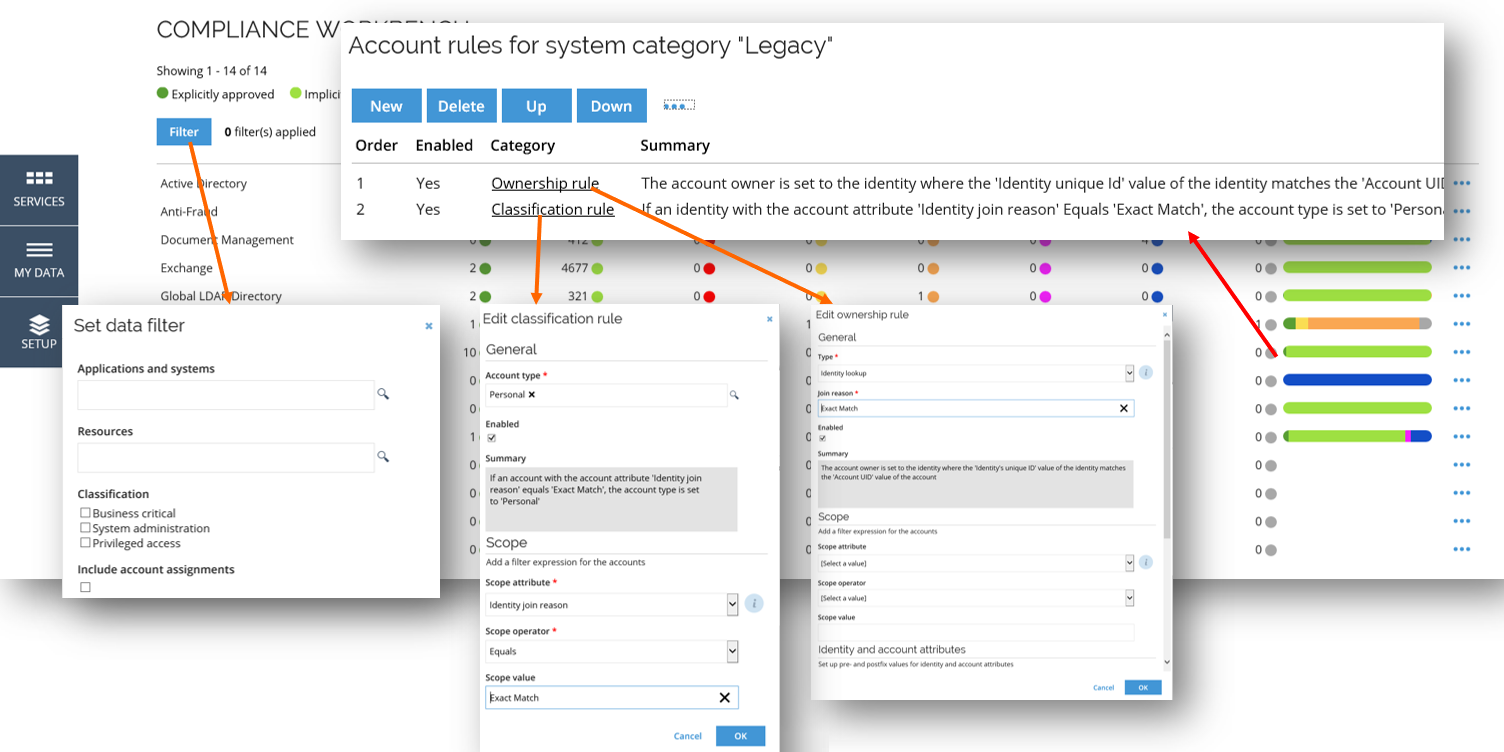
Similar to the Details, the Account rules are available under the ellipsis menu on the right-hand side of the Compliance Workbench.
This allows you to open the Account rules window for the desired system, and view and manage the account rules for the entire system category.
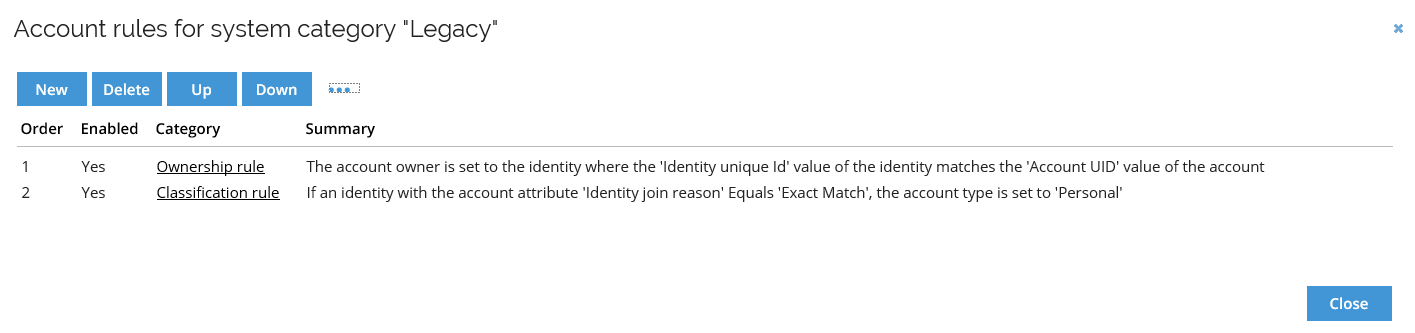
Account rules that you can configure here apply to all systems in a system category.
By default, all accounts in Omada Identity must belong to an identity; either the identity of who uses the account or the identity of the person responsible for it.
The Account rules are used to resolve account ownership and help you manage the accounts in your system by classifying them for different types of usage. When you onboard a system, you can import additional information and create rules based on that information to resolve the owner or resolve the classification of an account.
There are three types of Account rules you can add to an identity, and out-of-the-box there is one ownership and one classification rule already set up for you.