Security
The security in Omada Identity is enforced in several different places which are listed below:
| Enforcement Point | Description |
|---|---|
| Views | A view can be configured with a number of user groups who are allowed to see the view in the menu structure. |
| Menu Items | A menu item can be configured with a number of auth roles who are allowed to see the menu item in the menu structure. |
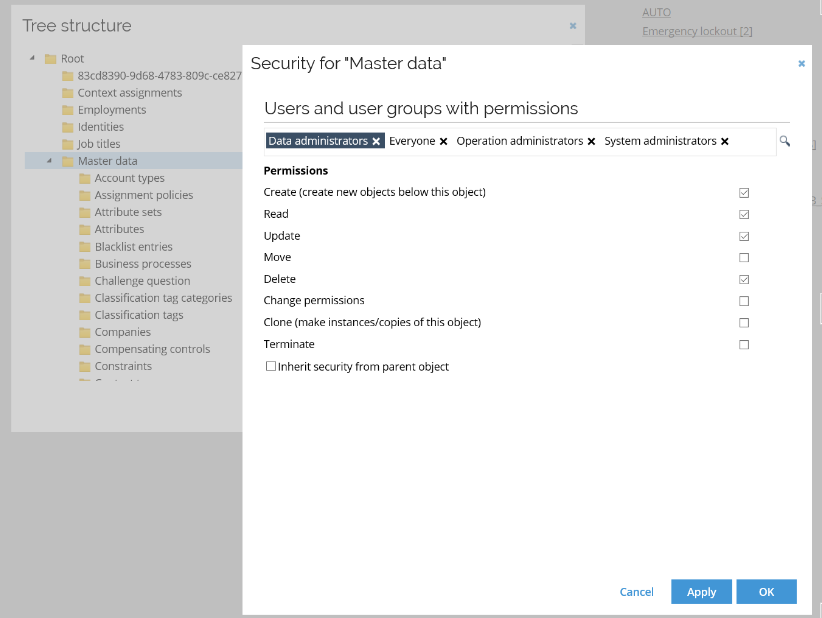
| Data Objects | A data object can be configured with a number of user groups and/or users having CRUD access to the data object and sibling data objects in case it is a folder. |
| Hard Coded Rules | Some security rules are hard coded in OIS. Examples: Auditors always have read access to surveys. System admins always have full access in a number of access modifiers. |
| Access Modifiers | Some access modifiers take parameters that specify that certain user groups have full access. The parameters are configured on the data object type or view where the access modifier is applied. |
| Dashboards | A dashboard can be configured with a number of user groups who are allowed to see the dashboard. |
| Surveys | A survey can be configured with a number of users and user groups who are survey admins. A survey admin is, for example, able to reassign questions. |
Data object security model
Data objects have a security model which resembles that of a file structure. A data object inherits security from its parent unless it specifically breaks the inheritance. If a data object has children, it is considered a folder data object.