Running policy & risk checks
Running policy & risk checks in Access Request
When you have enabled the policy check simulation feature, the simulation becomes an integral part of the access request process, either through an optional button that you can click before submitting the request or as a mandatory workflow in the process.
The organization can choose to configure the visibility settings for each policy & risk check in the Access-Request Approval. You may therefore see that some of the screenshots shown in this document vary from your Omada Identity implementation.
Running optional policy check simulation
If the organization has decided to make the policy check simulation optional, you can click Run Policy & risk checks before you submit an access request.
In such cases, you can use the policy & risk checks to preview if your access request violates the established protocol in the organization.
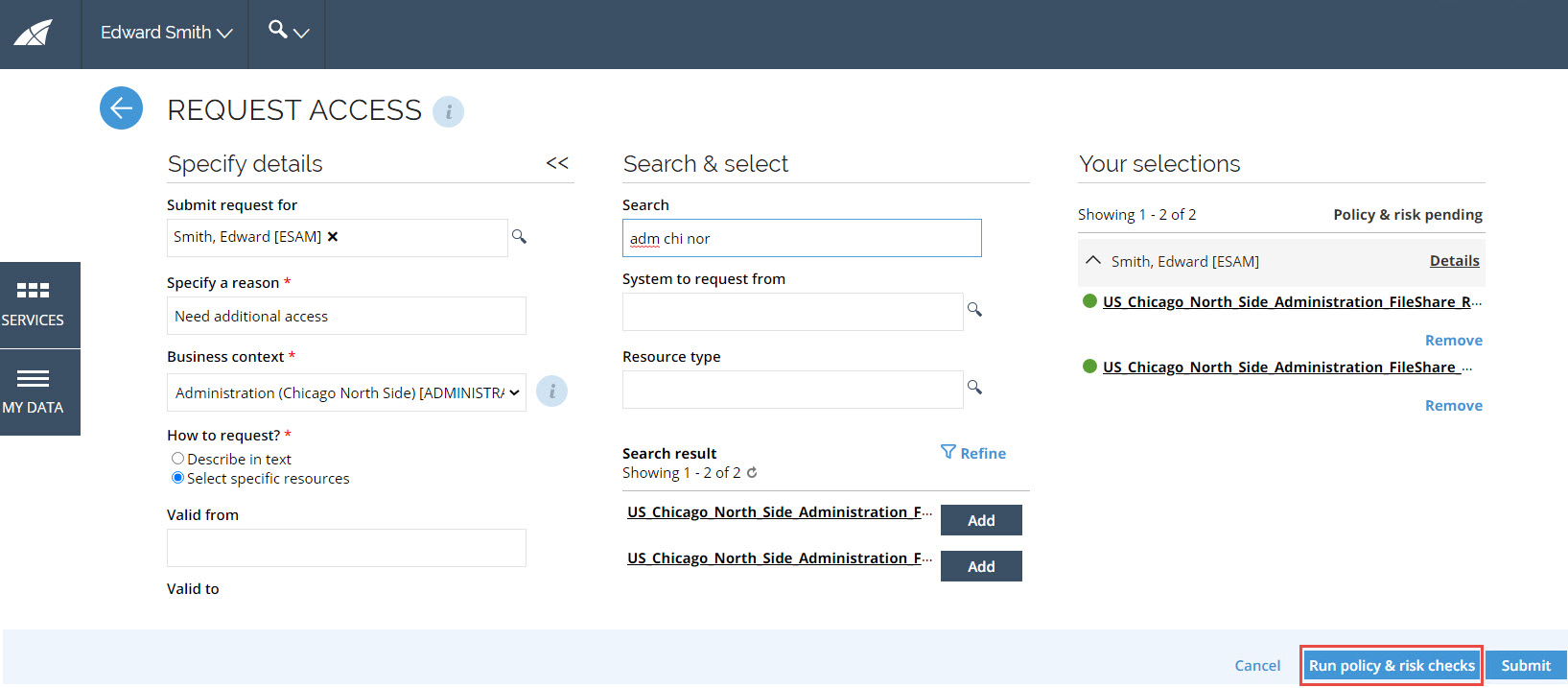
When you click Run policy & risk checks, the Summary of Policy & risk checks window opens. Depending on the number of resources that you have requested access for, this process may take a few minutes to complete.
You can cancel the policy checks that are currently running and return to the request by clicking Cancel.
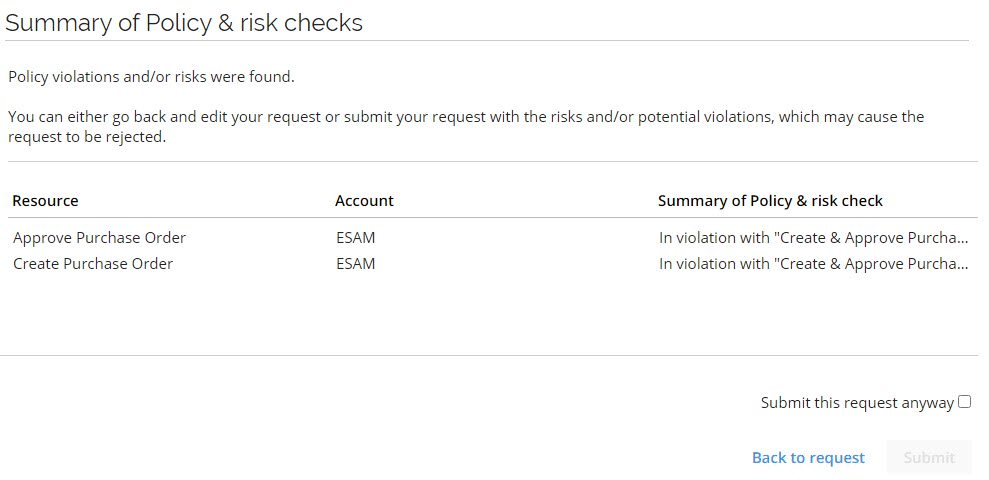
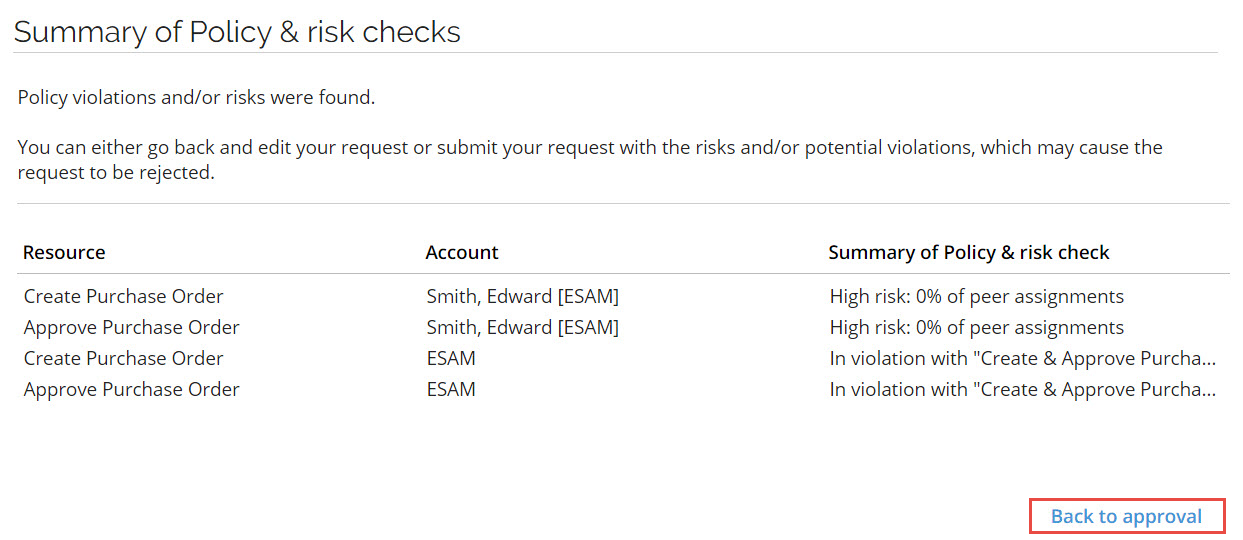
If any violations are found during policy checks, the user can decide too either:
- Continue submitting the access request with the knowledge that the requested resources violate the organization's policies.
- Go back to the request and click Details to see additional details for the violations and risks detected, and/or:
- Remove the resources that violates the policies, then submit again.
Users can always send their access requests even if there are any violations of company policies. Then, the approver (typically, the manager) must accept or reject the access request in the approval process.
Running mandatory policy checks
If the organization has decided to make one or more policies & risk check mandatory, the mandatory checks always run when users submit an access request.
The mandatory policy check forces you to pay attention to potential violations before you submit access requests.
You can choose to press the Run policy & risk checks button before you submit the request, however, if the policy checks are mandatory, the checks will be always performed on Submit.
Running policy check in Access Request Approval
When the organization has enabled the feature, the simulation becomes an integral part of the access request approval process. When you open the approval survey, the Policy & risk check summary dialog opens. When the results from the policy checks have been received, any violations or risks are shown. The user can close the dialog and continue with the approval.
To open and complete the Perform manager approval task, you must log on as a manager.
If approval has been configured for the requested resources, the resources must be approved in the approval process. The approval can be assigned, for example, to a manager, resource owner, and/or system owner, or other parties depending on the configuration. The approver(s) must respond to the access requests by opening the Perform approval task on the main page of Omada Identity.
If your organization has enabled policy check, it operates the same way as when a user requests access. When the check is enabled in the approval process, it runs as soon as you open the process. You can click Back to approval and the policy check will continue to run in the background.
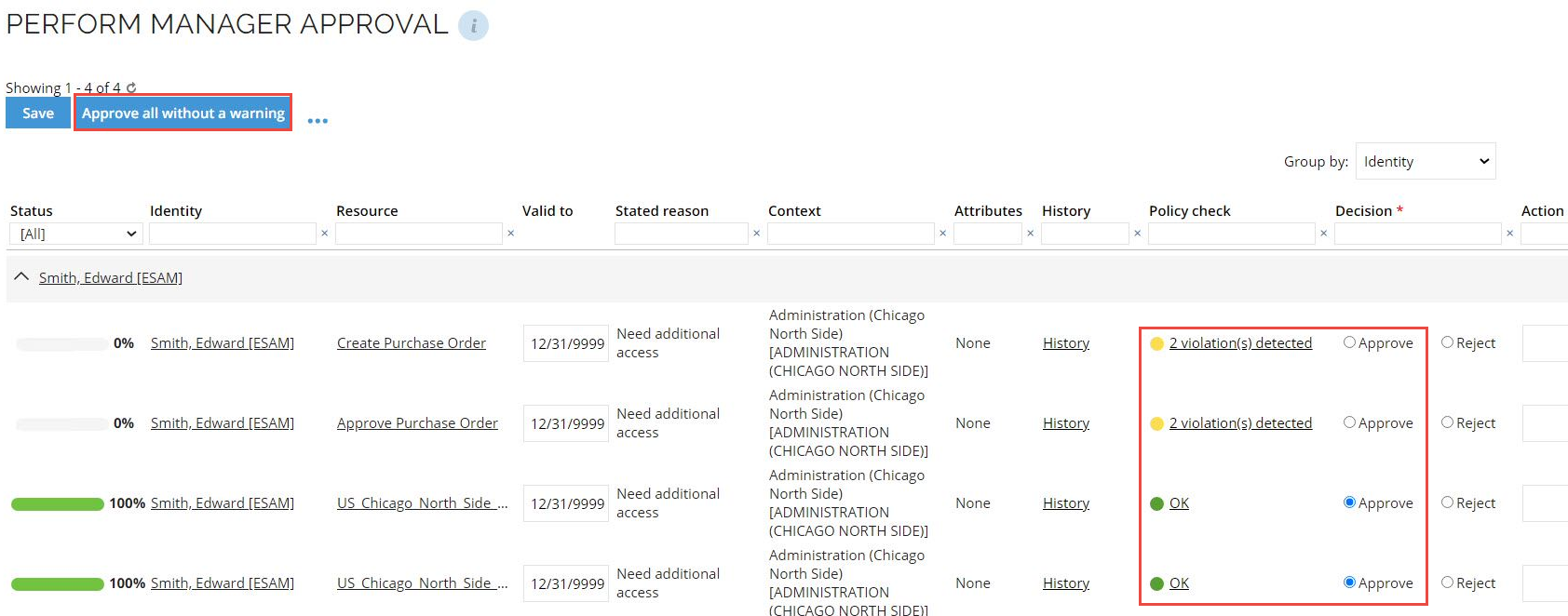
If the policy and risk checks are not set to hide in the access request approval, the results will be shown in the Policy check column. Click the (x) violation(s) detected to see details of the violations in the Result of policy check window.
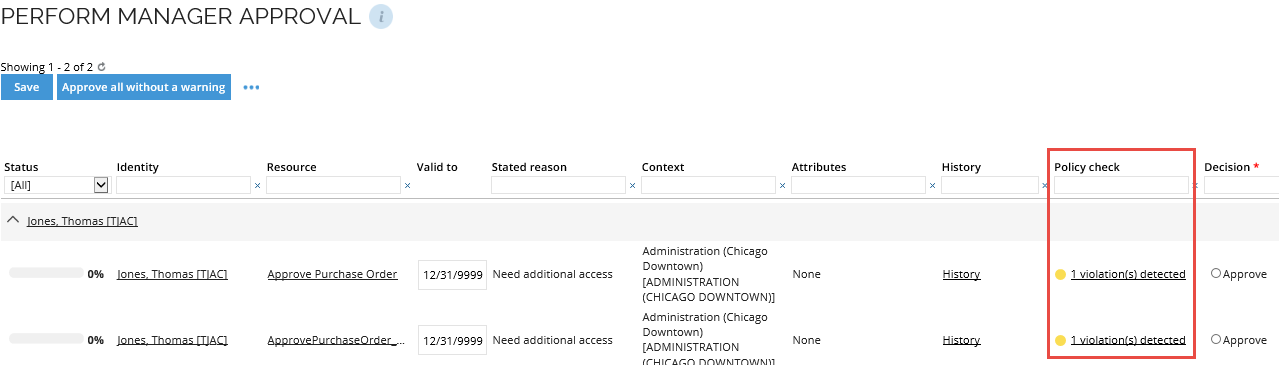
The assigned approver can then approve or reject the individual access requests, similar to the access request processes where policy check simulation is not enabled. If the approver rejects any access requests here, the rejected access requests are considered complete, and the requesting user cannot dispute the rejection. If the user believes that the rejection is incorrect, the user can submit the access request again and provide a comment to argue why the access request is necessary.
If the approver has approved access requests for at least one resource that is in violation to an established constraint, the access request is considered approved and starts the SoD calculation. When the violation of the constraint is detected in the RoPE policy check, RoPE triggers an Evaluate violation task that goes to the manager.
Approve all without a warning
You can approve all assignments that returned no risks and no violations by clicking the Approve all without a warning button. This marks all assignments with the OK status, also those that are not shown in the UI, and saves the survey objects. Click Submit to submit the approval.