OAuth Authentication

This page contains third-party references. We strive for our content to always be up-to-date, however, the content referring to external vendors may change independently of Omada. If you spot any inconsistency, please report it to our Helpdesk.
Omada Identity supports OAuth authentication through the use of bearer tokens for access to the Omada Identity website. The OAuth implementation supports various grant types, including username and password grants and client secret grants. The client's application that connects to ES must request a bearer token with a third-party Identity Provider (IdP) and provide the token as a bearer token in the HTTPS Authorization header.
Access tokens issued in response to a client credentials token requests are used for machine-to-machine communication where it is required not to store or embed usernames and passwords. By default, tokens based on client secret are not linked to Omada Identity's users; in consequence, users must be created with usernames that are the sub-claims of the access token. The service user must be granted a minimal authorization level needed.
By convention, the main Application registration in the IdP (the one used in the OpenID Connect configuration) cannot be used with client secret grants, i.e., one new application registration must be created per client application that connects to ES.
OAuth for OData API
The OData API in Omada Identity Cloud can be utilized with a Client Credentials flow, with OAuth authentication in customer’s own Azure tenant.
Prerequisites
To set up and configure such an authentication flow it is required to:
-
In Omada Identity, applicable Data Object Type(s) must be enabled for OData:
-
In Omada Identity Cloud Management Portal, authentication must be configured to use OpenID and Microsoft Entra ID:
-
Azure App for interactive authentication (hereafter Azure App OpenID) must be configured to use OpenID for authentication.
-
A tool for manually sending calls to Azure and Omada APIs will be needed.
We recommend downloading Postman. You can download it for free here.
Creating Azure App for OAuth authentication flow
A second or additional Azure App OAuth must be created, in the same tenant where Azure App OpenID is present.
-
In Microsoft Entra ID, click Register new application.
-
Go to Manifest and set the
accessTokenAcceptedVersionto 2.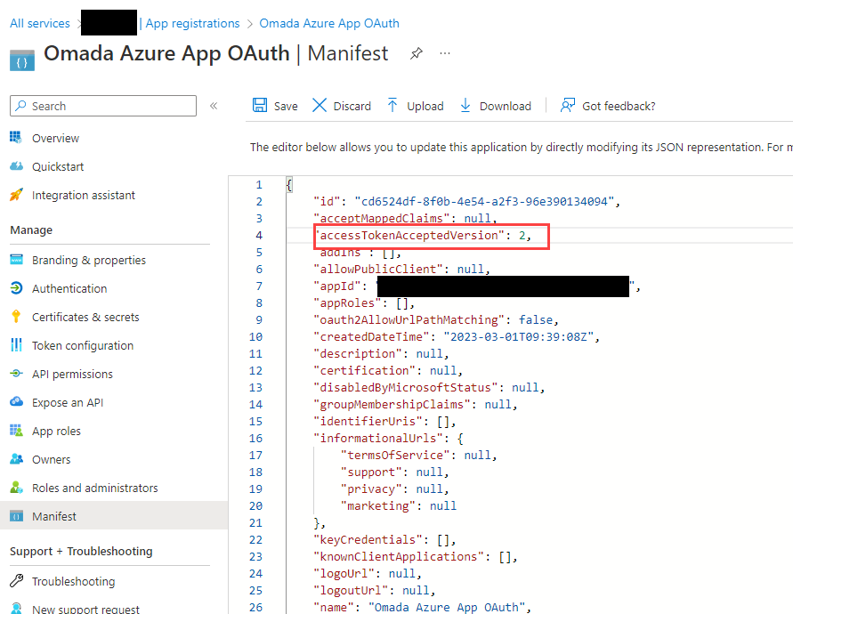
-
Go to Certificates & secrets and create a New client secret.
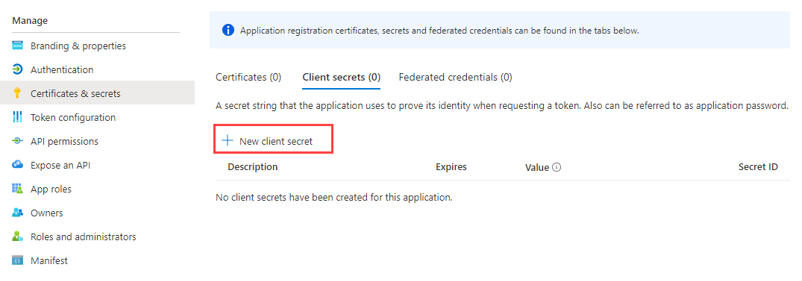
-
Make sure to copy and make a note of the Client secret value.
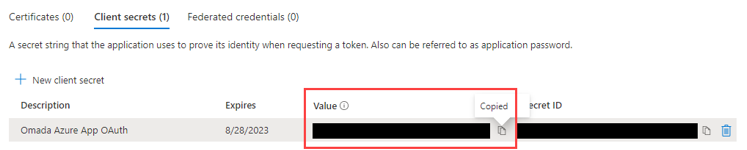
-
Go to Overview and copy and make a note the Application (Client ID).
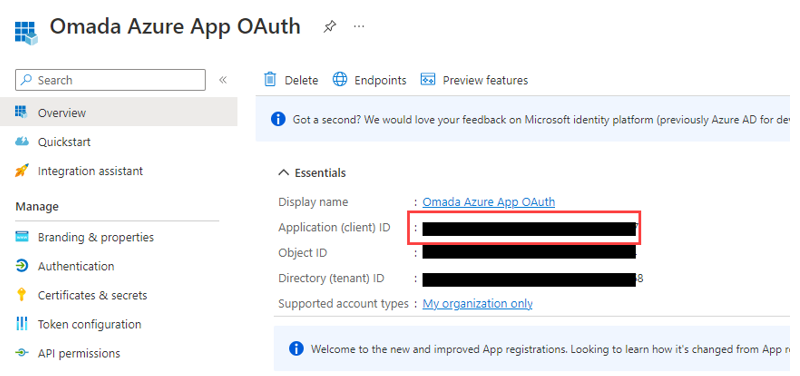
-
In the Overview, click Endpoints and copy and make a note of the OAuth 2.0 Authorization Endpoint v2 and OAuth 2.0 Token Endpoint v2.
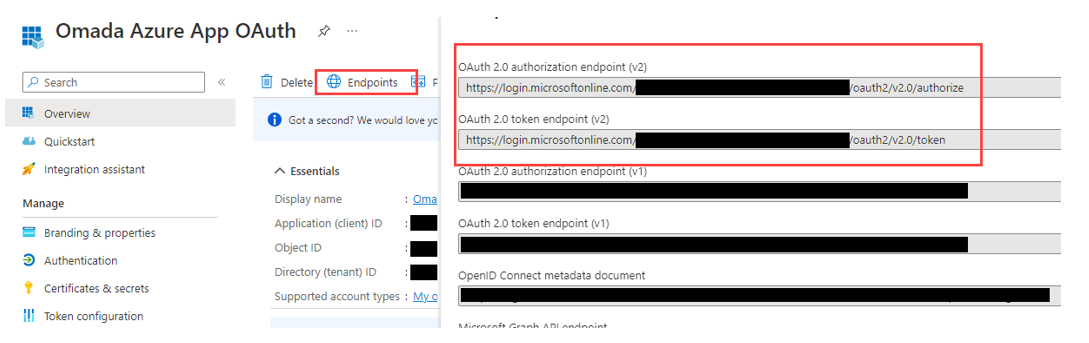
Configure Application ID URI in the OpenID application
Now, add an application ID URI in the application used for OpenID authentication (the one configured for authentication in the Omada Identity Cloud Management Platform).
-
In your Microsoft Entra ID tenant, go to the OpenID application (Azure App OpenID).
-
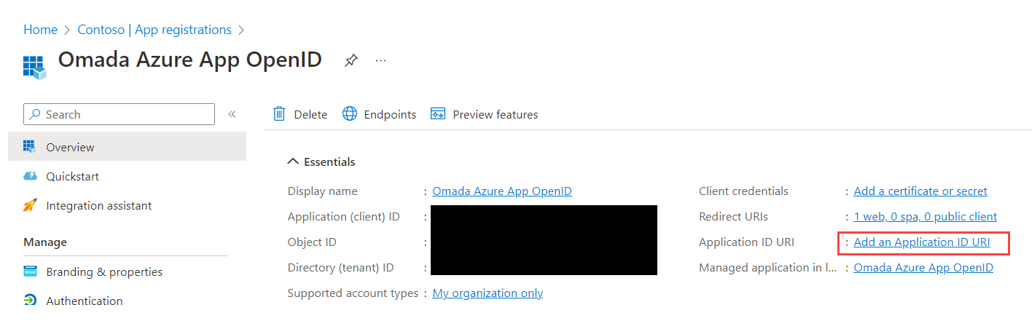
Click Add an Application ID URI.
-
Click Set and enter the API URL, as follows:
API://[id of the OData AppRegistration]
Generating a bearer token
-
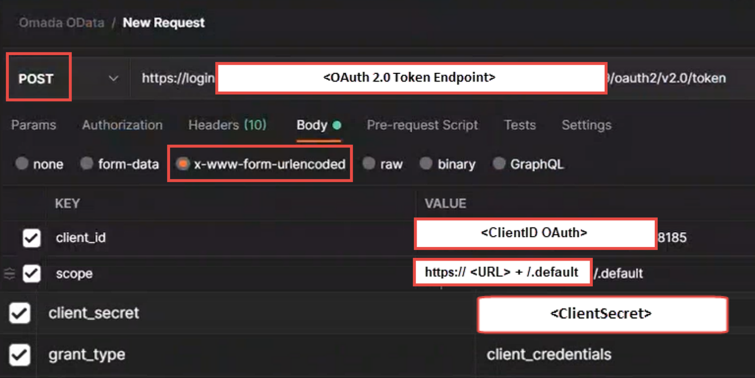
In Postman, create a new POST request, with four added Headers, using values from step 3:
-
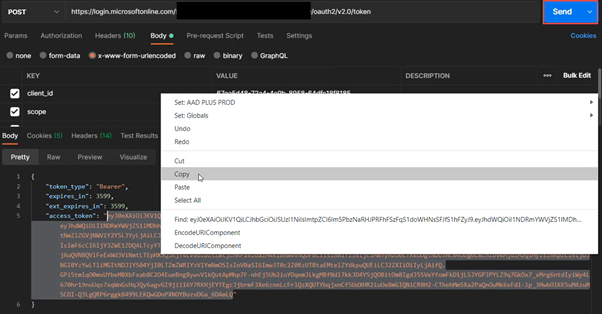
Send Request, then copy the BearerToken returned:
-
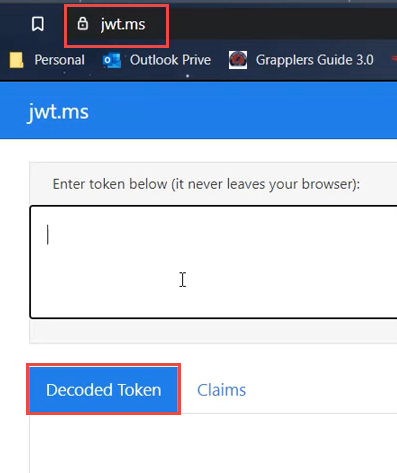
Using a web browser, navigate to URL: jwt.ms..
-
Paste the BearerToken, and click on the Decode Token button.
-
Verify that values are correct:
“aud” = <ClientID OpenID>
“azp” = <ClientID OAuth>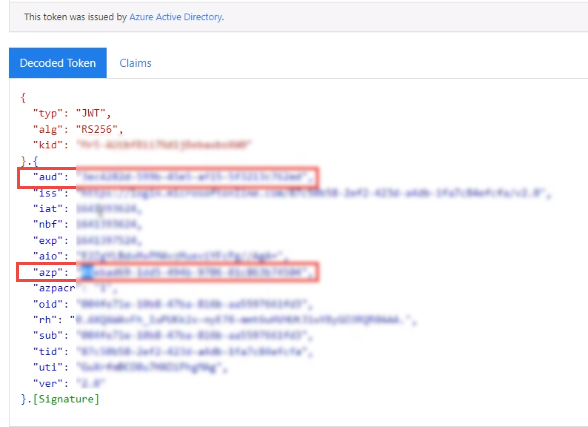
Create a user in Omada Identity for the authentication application
Now, create a user in Omada Identity Cloud for the application that will be able to impersonate users.
-
Log in to Omada as a System administrator.
-
Go to Setup > Administration > Users & Security > Users.
-
Click New.
-
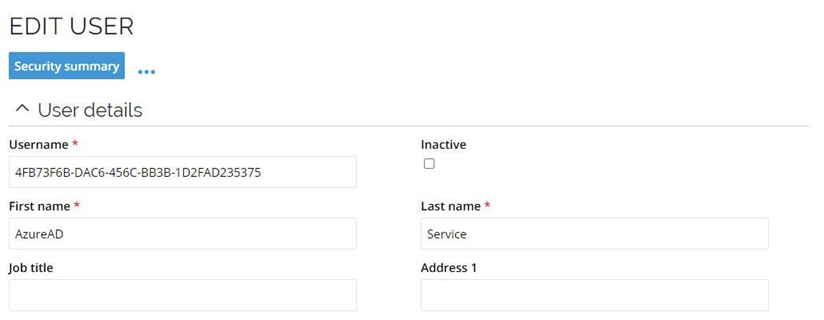
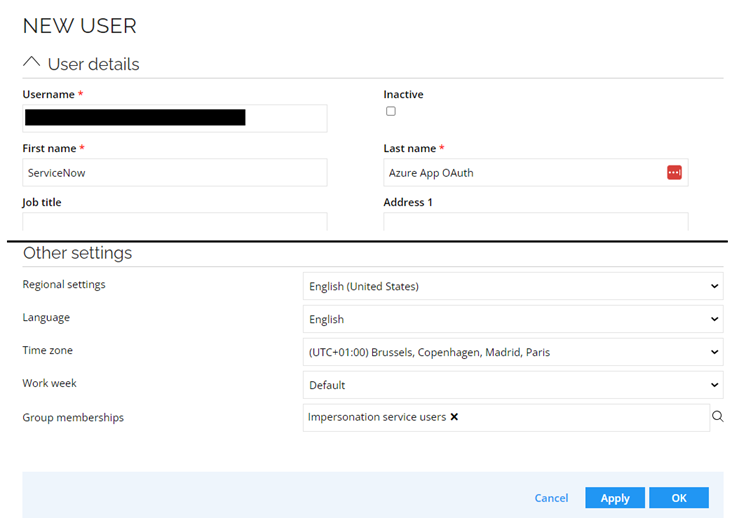
As the Username, add the Application / Client ID copied from Microsoft Entra ID (Omada Azure App OAuth app)
-
Name the user with a suitable name, for example, after the application name registered in Microsoft Entra ID.
-
Assign the user to the Impersonation service users group.
-
-
Click Apply or OK to save the user.
Verifying authentication flow and access
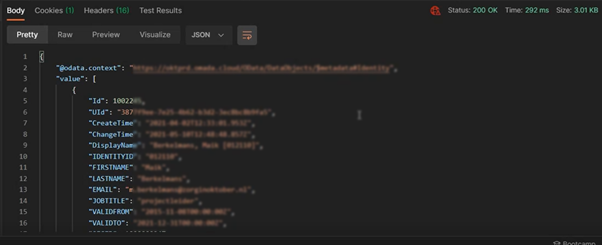
In Postman, create a new GET request, using coded BearerToken for authentication, and applicable URL as seen below:
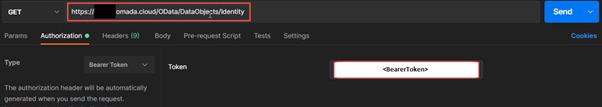
Response: