Evaluation of the results of policy check
If there are no violations found during the policy check, you receive a confirmation message. You can choose to approve or reject requests. The policy and risk checks should be used as a guide to the user.

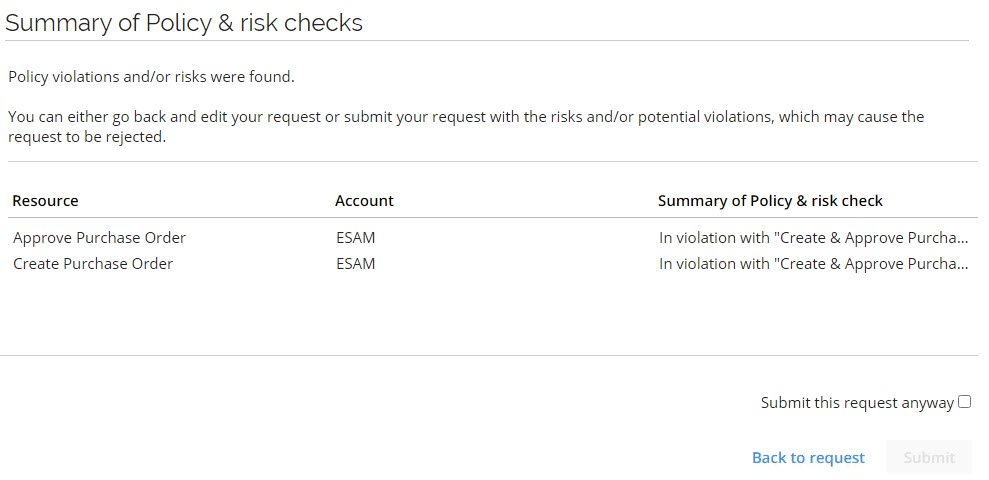
In contrast, if violations are found, you receive an overview of the violations that were found. The violations are listed one by one and detail the policies that have been violated.
Then you can close the window and review the details by clicking the link in the Policy check column.
To bring up the summary view again, you can click context menu and select Policy & risk summary.
As mentioned above, the Result of the policy check window strictly serves as information to you. The violations that have been found never block you from approving a request.
Color rules
The following color rules apply in the Main window of the access request and Approval in this priority (where the first wins):
- If one or more checks have an error, then a black icon is displayed.
- If one or more checks have a warning, a yellow warning icon is displayed.
- If all checks have been run successfully and there are no warnings or errors, then the result will be green.
- If a policy check has not been run yet, then the icon is grey. The icon can also be grey if peer access is the only check enabled, and the identity has no peers.
In the Details view, the different checks have icons that show the status of the resources that have been checked.
If a resource has been defined as not relevant for a check, then its status will be OK (green) for the SoD policy check and Risk analysis in SAP GRC. For Peer Access Analysis, the icon stays grey if Peer Access Analysis has not been run for a given resource.
In such cases, the message displayed in the Details window for the SoD policy check and Risk analysis in SAP GRC will show no risks found. For Peer Access Analysis, there will be no corresponding message.
Result of policy check overview
Resource - lists the resources that violate a constraint.
Account - lists the identity whose access request has caused a violation.
Summary of policy & risk check - shows the active constraint that the request violates, as well as information on the reference number of the errors, if any appear.
Submit this request anyway - enable this setting to submit the access request for approval, even though it violates a constraint.
Back to request - go back to the request form and change the resources that you include in the access request, for example, delete one or more of the resources that cause the violation, or add a reason for wanting the toxic combination in the text field.
Submit - send the access request to your manager for approval.
Cancel policy checks - when the policy and risk checks are still being performed, you can click this button to cancel them.