Access request
The Access request process allows you to define the scope of your access requests. You can easily select who should have access to specific resources or systems using this process. With the Access request process you can:
- Request access for multiple beneficiaries simultaneously.
- Request access more simply and intuitively.
- Check your access requests on a new page.
Experience the request access process with Omada Identity Cloud interactive walkthrough. Learn how to perform a manager approval of access requested by one of your subordinates.
Follow these steps to request access:
-
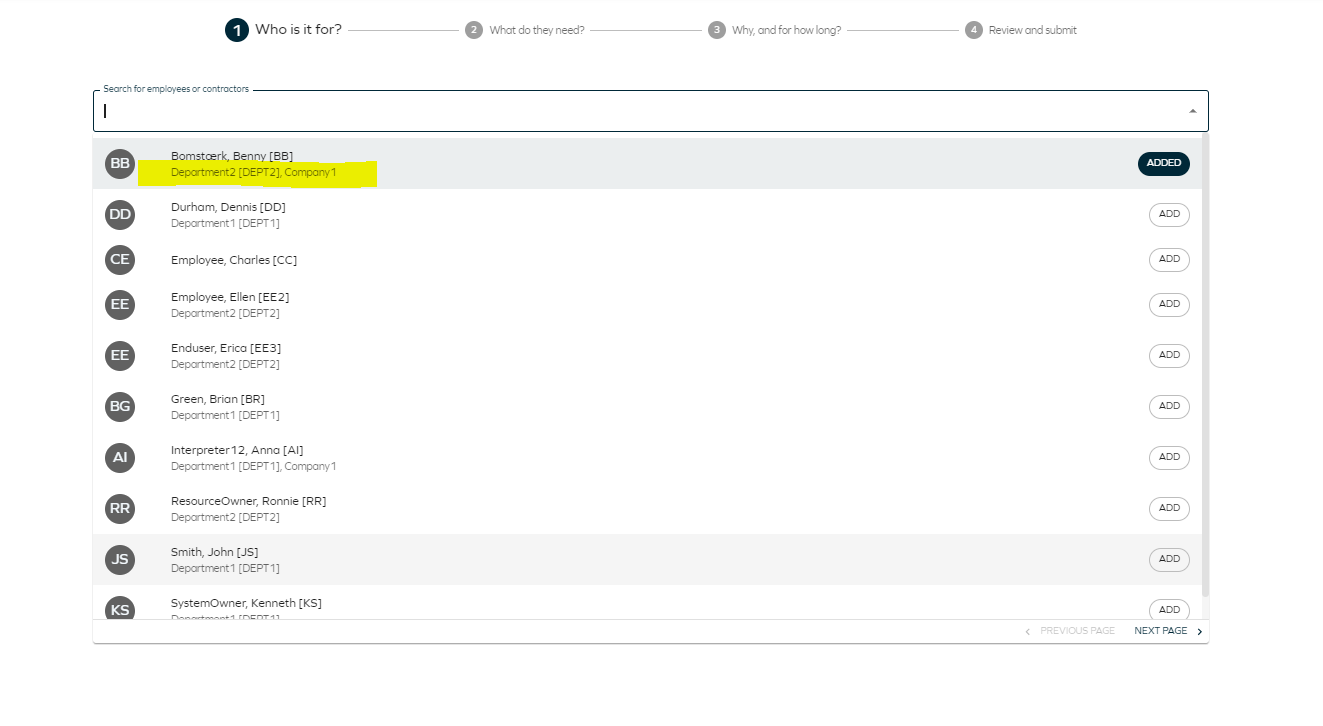
Click Request access tab in the Home page. The page will open, and you will see four steps.
-
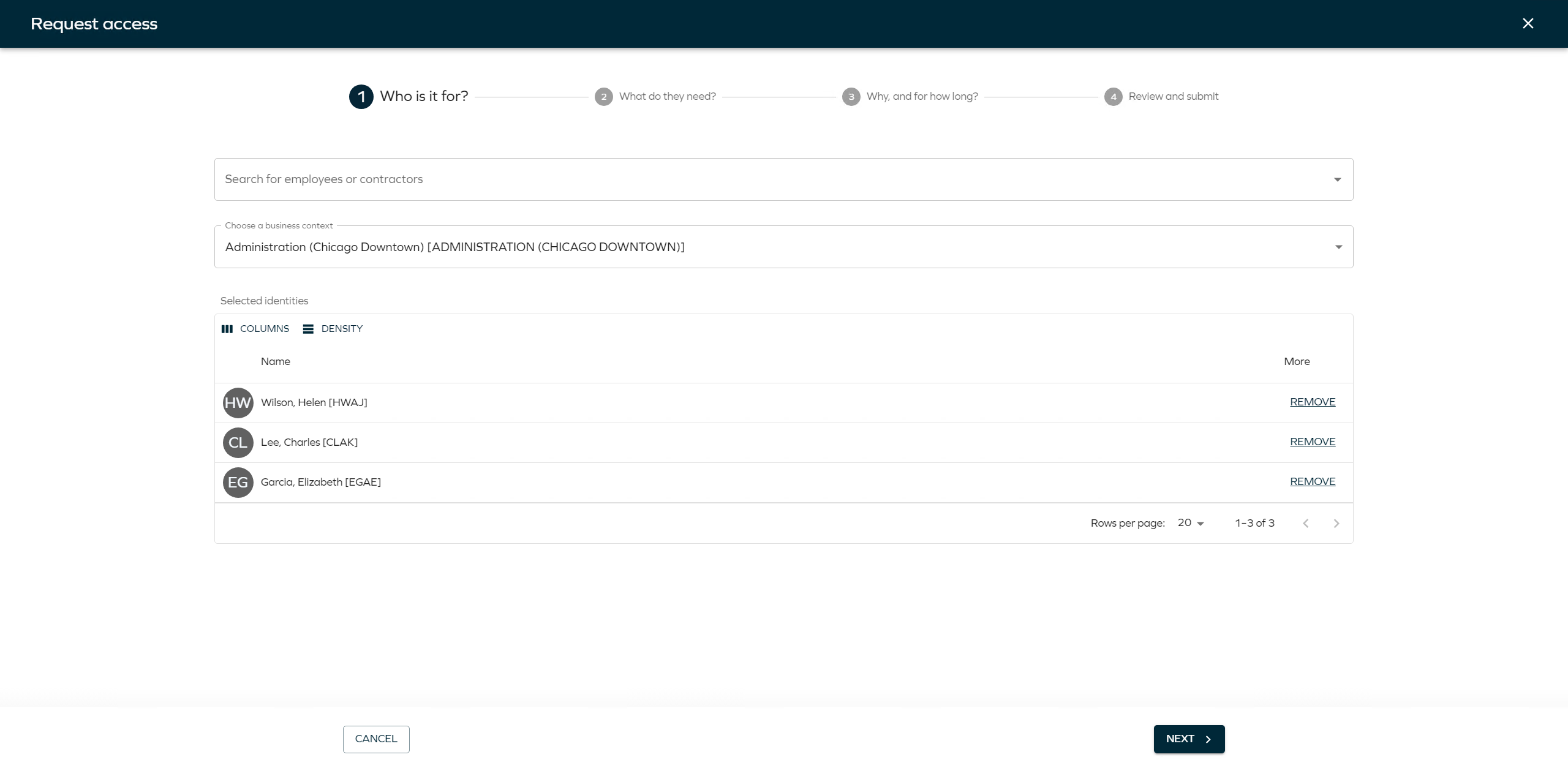
Select the beneficiaries for whom you want to request access. Click Add to add as many beneficiaries as needed.
 tip
tipIf you intend to request access for more than one beneficiary simultaneously, they must share the same business context.
-
Select the business context and click Next.
-
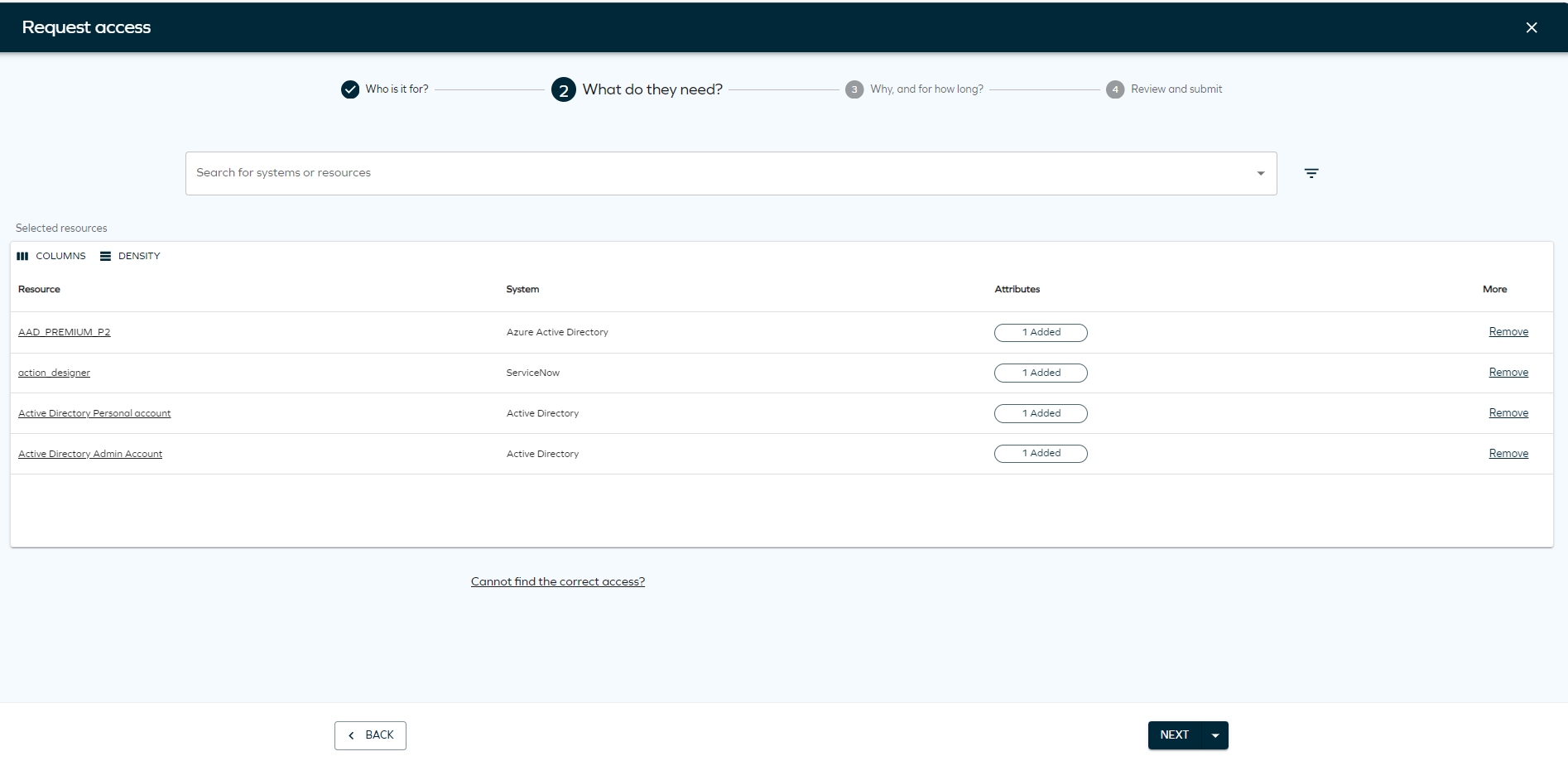
Search for the systems or resources to which you want to provide access. Click Add to include as many resources or systems as you want. You can also select Show assigned resources or Show popular resources first to display resources assigned to that beneficiary, if applicable.
 tip
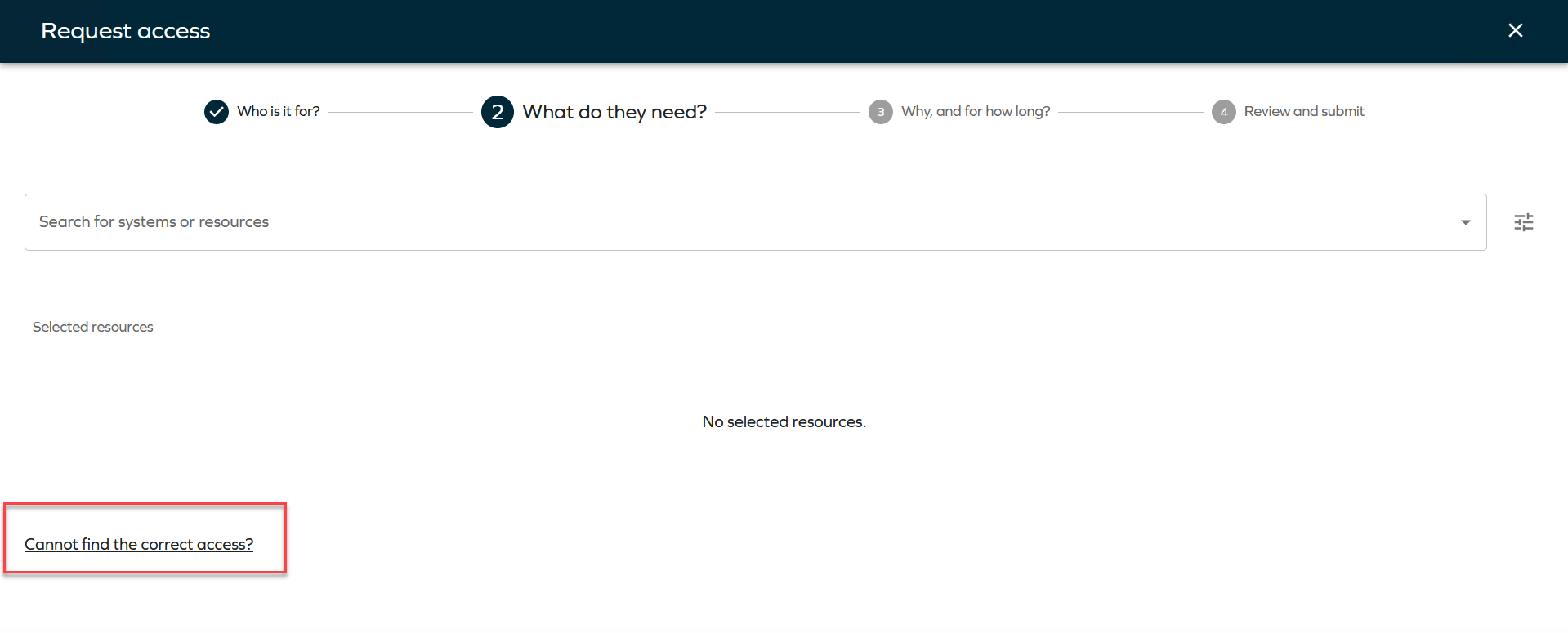
tipIf you don't find the resource you are looking for, you can click on Cannot find the correct access? to type the access request manually.
 info
info-
You can edit the resources and choose the desired account type for each resource.
-
The new Access request process will also take into account Auto-account type configuration. A warning will indicate if a resource cannot be added to the request due to a lack of a valid matching account type.
-
-
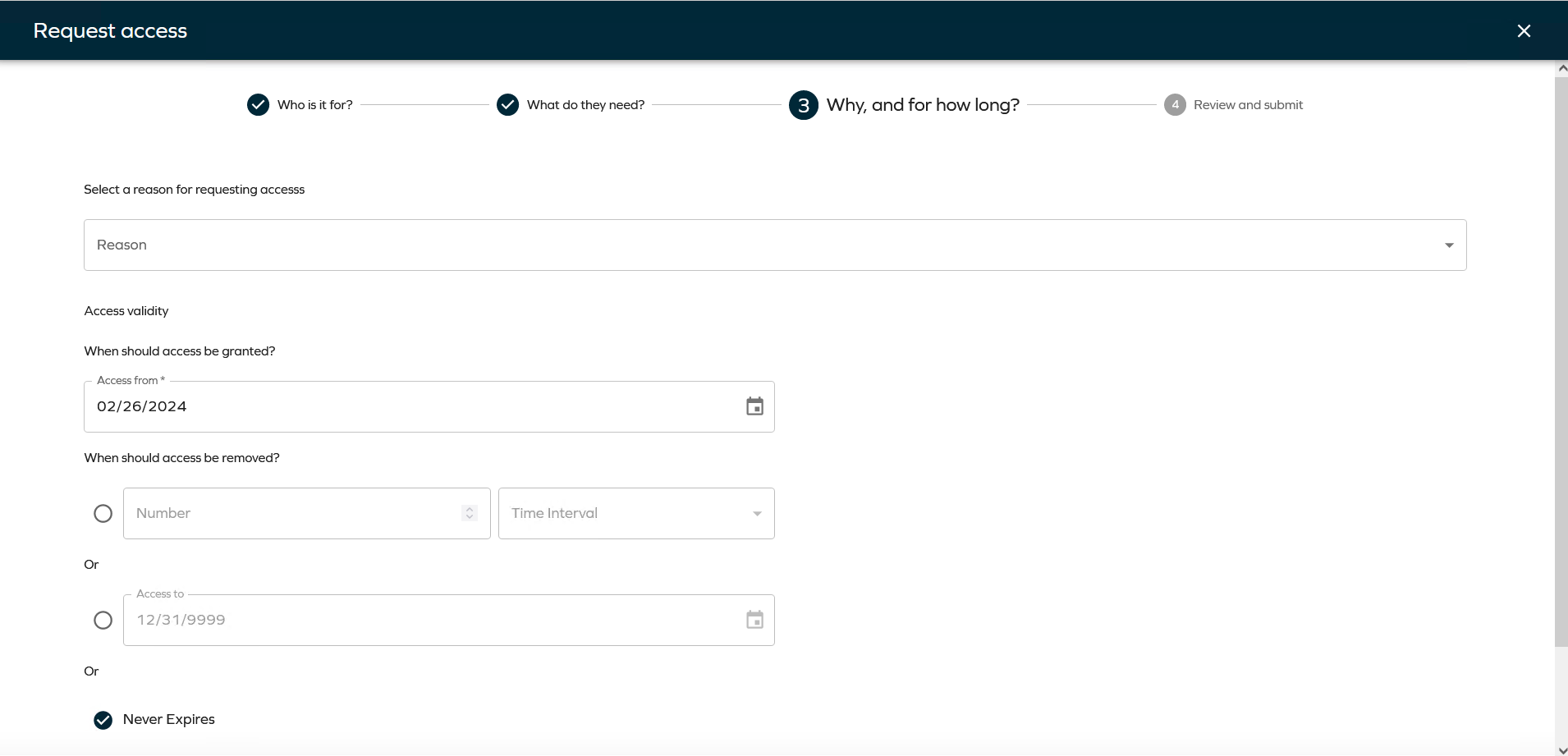
Select a reason (if it is enabled) for requesting access and choose a valid date to grant access to the beneficiary from the selected day.
noteSet the Reason field to be optional or hidden entirely. Set the Requires value to False to make the field optional or to True to hide it.
-
On the final step, review and edit beneficiaries and resources. Click Next to complete the access request.
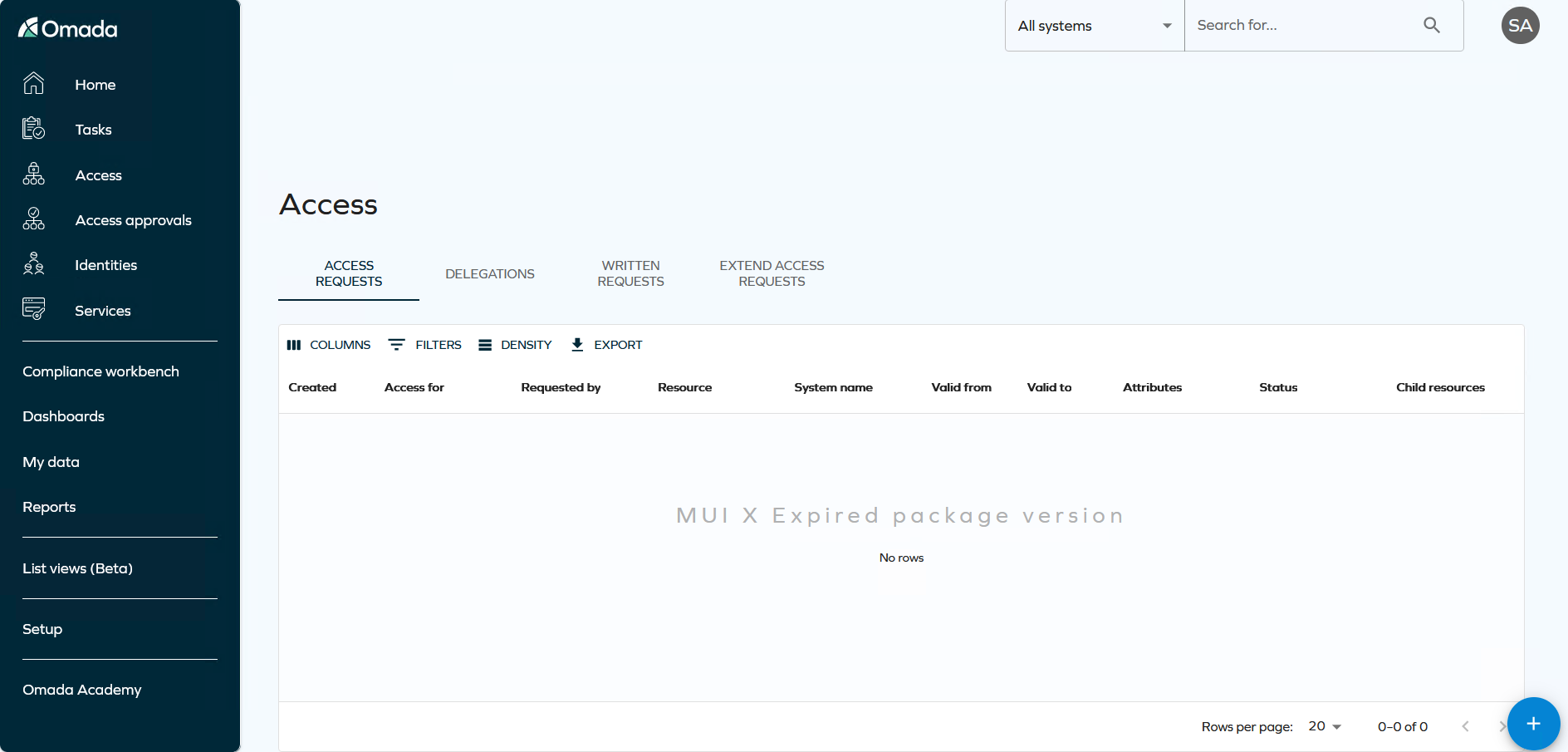
To view your active access requests, navigate to the Access tab in the navigation pane. Here, you will find a list of all your active access requests. The Access request tab allows you to receive paged results from the server.
-
It is not possible to request access for technical identities using this new Access request process. If you want to request access for a technical identity please refer to Omada Identity - Legacy Access Request User Guide.
-
If a resource doesn't require attributes but has an assigned account type, the resource will be associated with that account type.
-
Beneficiaries can only be assigned a resource if both the identity and the resource share matching account types.
-
Access can be requested for multiple beneficiaries only if they share the same business context.
If you are still using the legacy access request, please refer to the Omada Identity - Legacy Access Request User Guide to find more information about it.
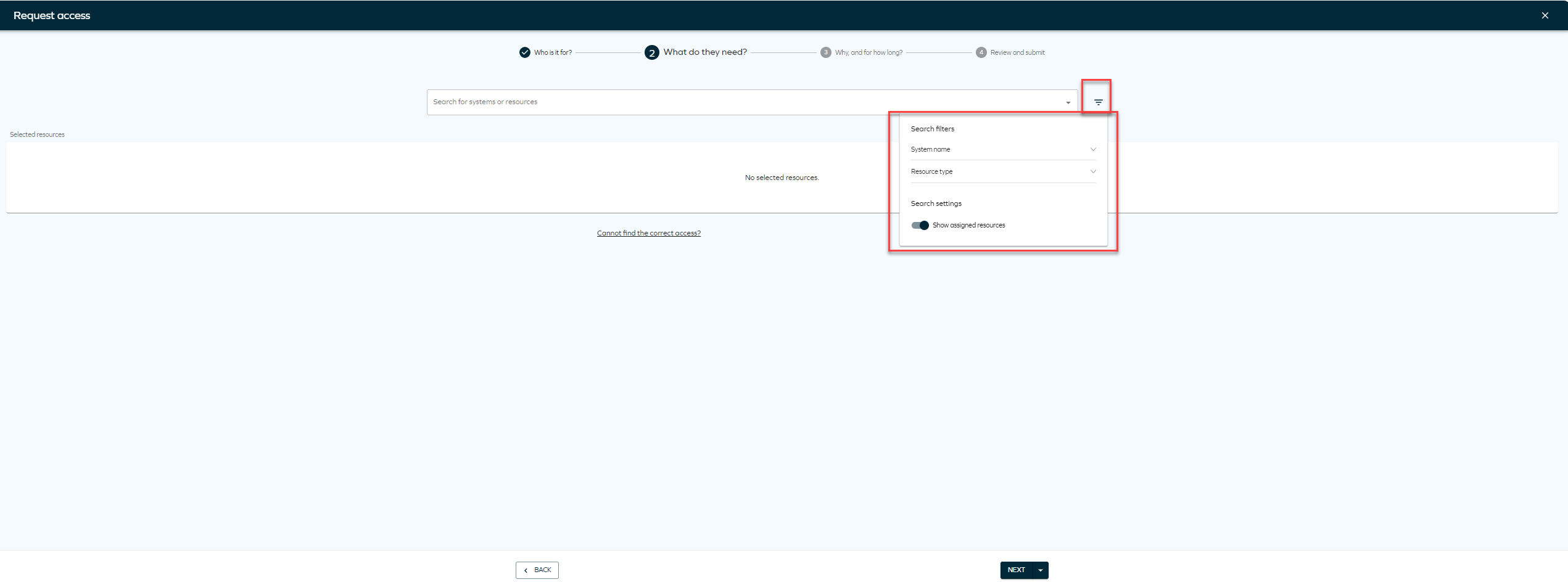
Assigned resources toggle
On the new Access Request page, we have moved the Show assigned resources toggle to a new settings menu. In this menu, you will find a new toggle called Show popular resources first. To sort resources by popularity, you need to enable context on the Access request form, and make sure the customer setting Access request - popularity enabled is set to True. You can access the settings menu by clicking the icon next to the Resources dropdown.
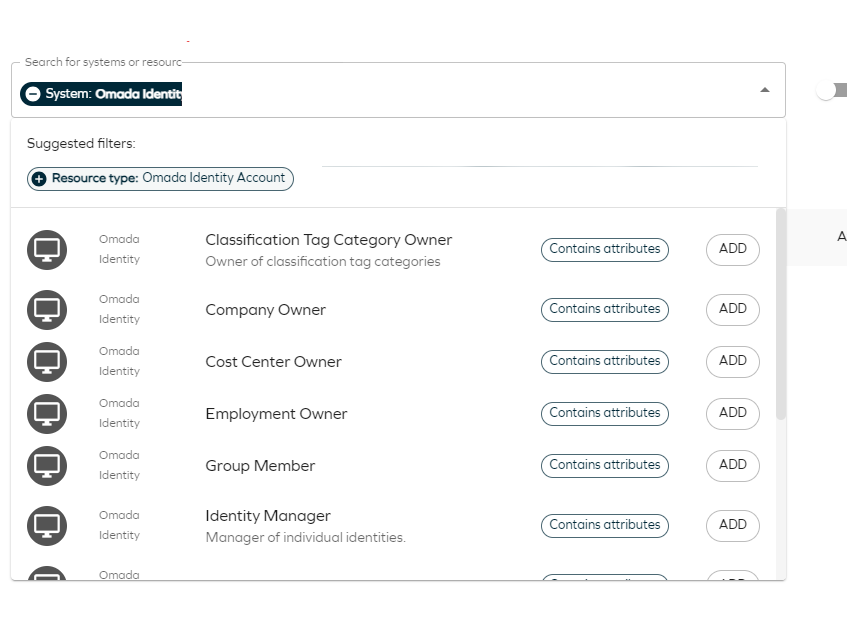
Search filtering
You can use the Enable Search Filtering that lets you choose how you want to view your list of resources in the Resource step when requesting access. Now when adding resources you will see a Suggested filters section to the search box. These filters are quick tags that help you narrow down your resource search. The section contains chips with possible filters to use. The chips come in two types: System and Resources and each filter chip shows the type and name, for example: System: Omada Identity.
When you start typing in the search field:
-
Filters related to your search appear in the Suggested filters section.
-
You can click on a filter chip to apply it, and the resource list updates based on that filter.
-
You can apply multiple filters of different types, but only filter the same type at a time.
-
You can select two different system filters or two different resource type filters simultaneously.
We limit the number of filter chips to better usability. If you select a filter of a certain type, other filters of the same type hide. They become visible again if you remove that filter from your search.
Edit contexts in Access Request
You can choose which identity details are shown when you request access. To do that go to Set up > Properties and find the system name AR_CONTEXT, click Edit lookup view and set up the filters you want to appear in the Access Request process.

Now, when request access, the identity details displayed will match what you configured in the Lookup view.
Experience the approve access request process with Omada Identity Cloud interactive walkthrough. Learn how to perform a manager approval of access requested by one of your subordinates.
Request access on behalf
You can request access on behalf of another person depending on the authorization role you have. Here, you can see which roles may require access on behalf of another person:
- Administrators: can request access for themselves.
- Auditor: can request access for themselves.
- CIAM end user: can request access for themselves.
- CIAM service user: can request access for themselves.
- Contractor: can request access for themselves.
- Data administrator: can request acccess for all identities.
- Employee: can request access for themselves.
- Manager: can request access for themselves and the identities they manage.
- Operation administrator: can request access for themselves.
- Password filter: can request access for themselves.
- Platform admin: can request access for themselves.
- Resource owner: can request access for themselves.
- Service desk: can request access for themselves.
- System owner: can request access for themselves.
- User: can request access for themselves.