Identity Risk Subscription with Microsoft Entra ID Identity Protection
With the Identity Risk Subscriptions feature, you can integrate external identity risk detections, for example from Microsoft Entra ID.
Using Microsoft Graph - Microsoft Entra ID Graph Identity Protection API, we can trigger an event based on risk events detected in Microsoft Entra ID Identity Protection. The risk events can, for example, include log-ins using an anonymous browser, impossible travel, leaked passwords, and such.
The triggered event enables users in Omada Identity to react to security events in one system that may affect the whole identity. It's an opportunity for managers in Omada Identity to inspect the risk detection and decide whether some additional actions are needed, such as an emergency lockout of the identity during the investigation, for example.
The solution consists of the following, two main elements:
-
The ability to subscribe to risk detection events in Microsoft Entra ID Identity Protection Integration.
-
The ability to react to those events by configuring event definitions with related filters and actions.
Install Subscription integration feature package
Verify whether the Subscription integration feature package is already installed:
-
Go to Setup > Administration > Configuration management > Installed packages tab.
-
Perform one of the following actions:
- If the Subscription integration package is on the list and the checkbox is greyed out, the package is already installed. Continue to the next section.
- If the Subscription integration checkbox is selectable, click the Install button.
Create a new subscription
Prerequisites
To create a new subscription, first, you must do the following:
-
Ensure you have a P1 or P2 license in Microsoft Entra ID.
-
Ensure that the Microsoft Entra ID application have the necessary API permissions to create a subscription to the SecurityEvents.ReadWrite.All resource.
-
Ensure that the server available for notifications is accessible from the Microsoft Entra ID or MS Graph via the address in the
WebSiteURLcustomer setting. It must beHTTPS.- For more information on Microsoft Entra ID subscription requirements, refer to the Microsoft Azure AD documentation.
-
Create an App Registration in Microsoft Entra ID. The variables such as
Tenant ID,Client Secret, andClient IDwill later be used in the Onboarding Values configuration parameters.
Configuration
Follow these steps to create a new subscription data connection:
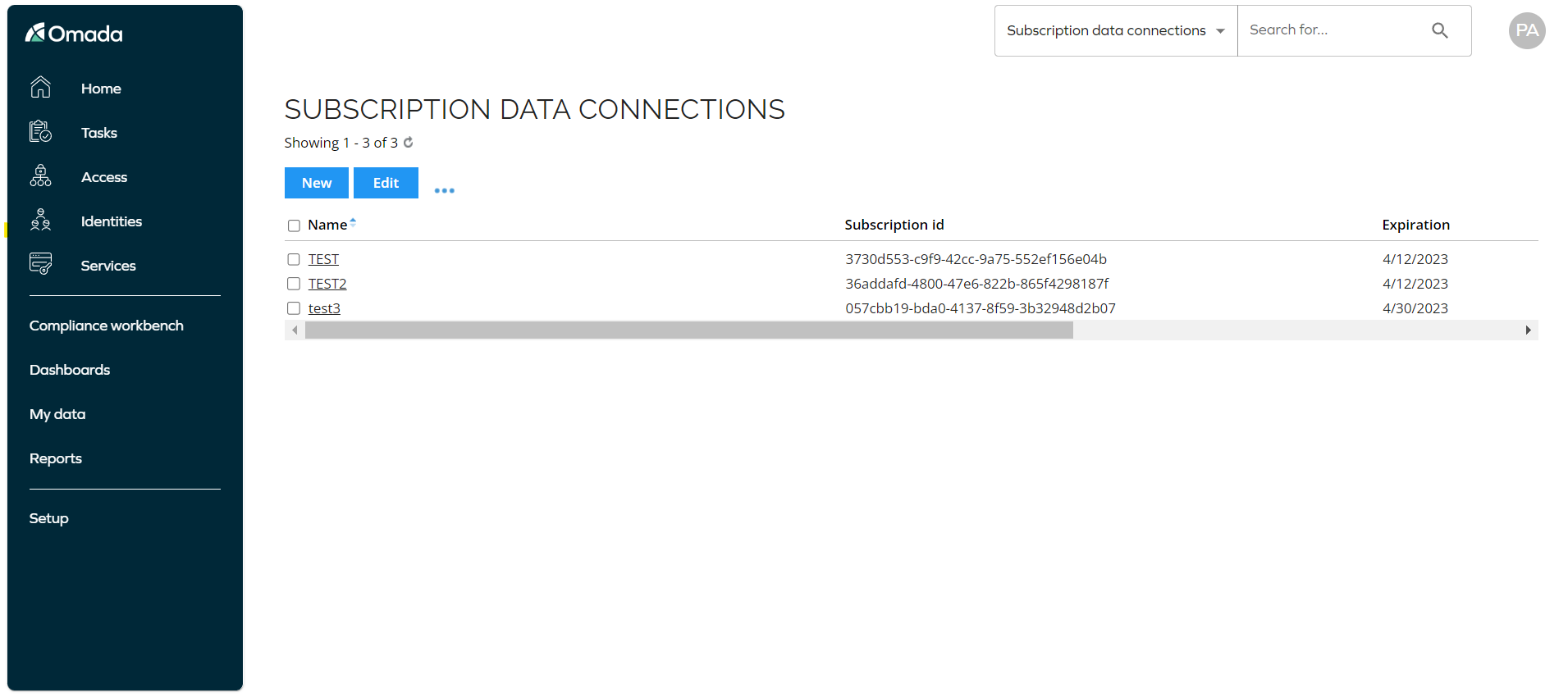
-
Go to Setup > Administration > Connectivity Configuration.
-
Open the Subscription data connections view and click the New button to create a new subscription data connection.
-
Provide the name of the data connection and click the Apply button.
-
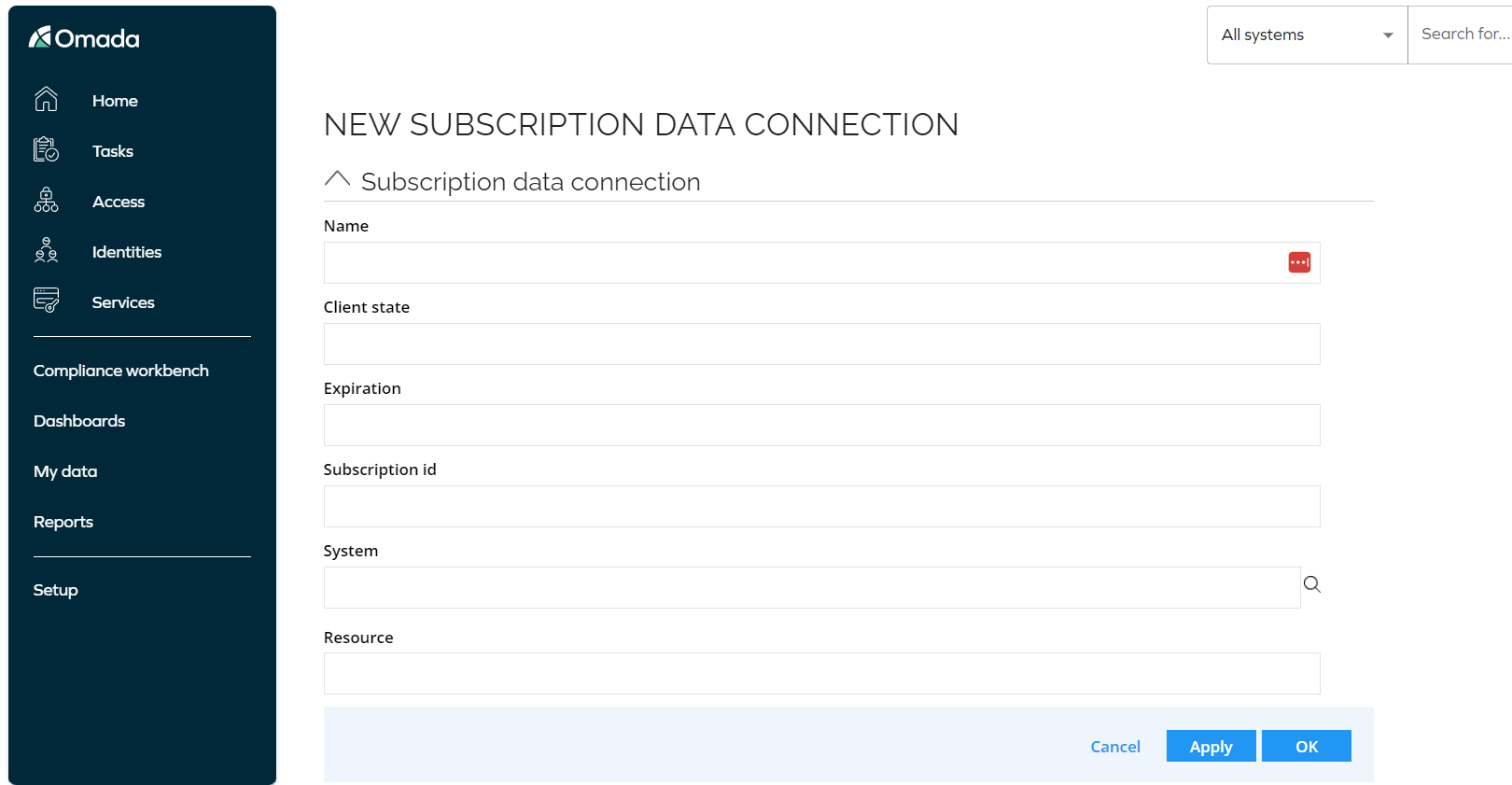
Fill in the following fields:
- Onboarding values field with the following configuration parameters:
<ConfigurationParameters xmlns="http://schemas.omada.net/ois/2016/SystemConfigurationValuesML">
<configurationParameter Name="Type">
<values>
<value>MsGraph</value>
</values>
</configurationParameter>
<configurationParameter Name="AuthMethod">
<values>
<value>AzureAD</value>
</values>
</configurationParameter>
<configurationParameter Name="ClientId">
<values>
<value>3d4c55b2-121d-4488-af3a-a43aff3f42dc</value>
</values>
</configurationParameter>
<configurationParameter Name="TenantId">
<values>
<value>2272d63f-dcbd-4ac2-82d2-faa89d26b761</value>
</values>
</configurationParameter>
<configurationParameter Name="ClientSecret">
<values>
<value>SECRET</value>
</values>
</configurationParameter>
<configurationParameter Name="Scopes">
<values>
<value>https://graph.microsoft.com/.default</value>
</values>
</configurationParameter>
</ConfigurationParameters>noteRemember to swap the
Tenant ID,Client Secret, andClient IDplaceholders with your values obtained during the App Registration in the Microsoft Entra ID.
-
In the Expiration field, provide the subscription expiration date
- The maximum length of subscription per resource type is under 30 days. That is, the expiration date cannot exceed 30 days set in the future.
-
In the System field, select the Microsoft Entra ID, that is, the target system for which the notifications are subscribed.
-
In the Resource field, provide the MS Graph security alert resource, for example,
security/alerts/?$filter=severity eq 'medium'.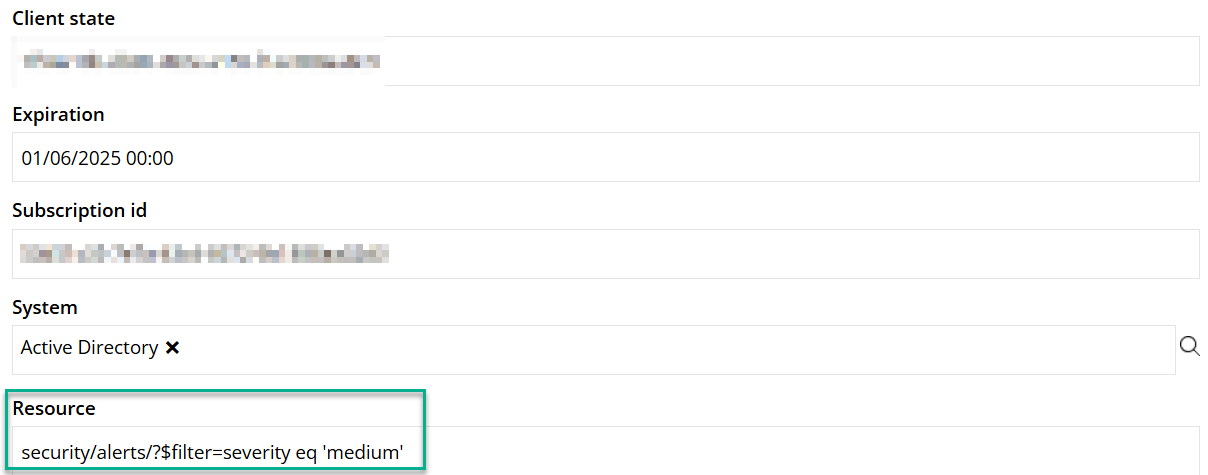
You can only subscribe to MS Graph notifications for changes to filtered alerts, that is, /security/alerts/?\$filter={parameters}.
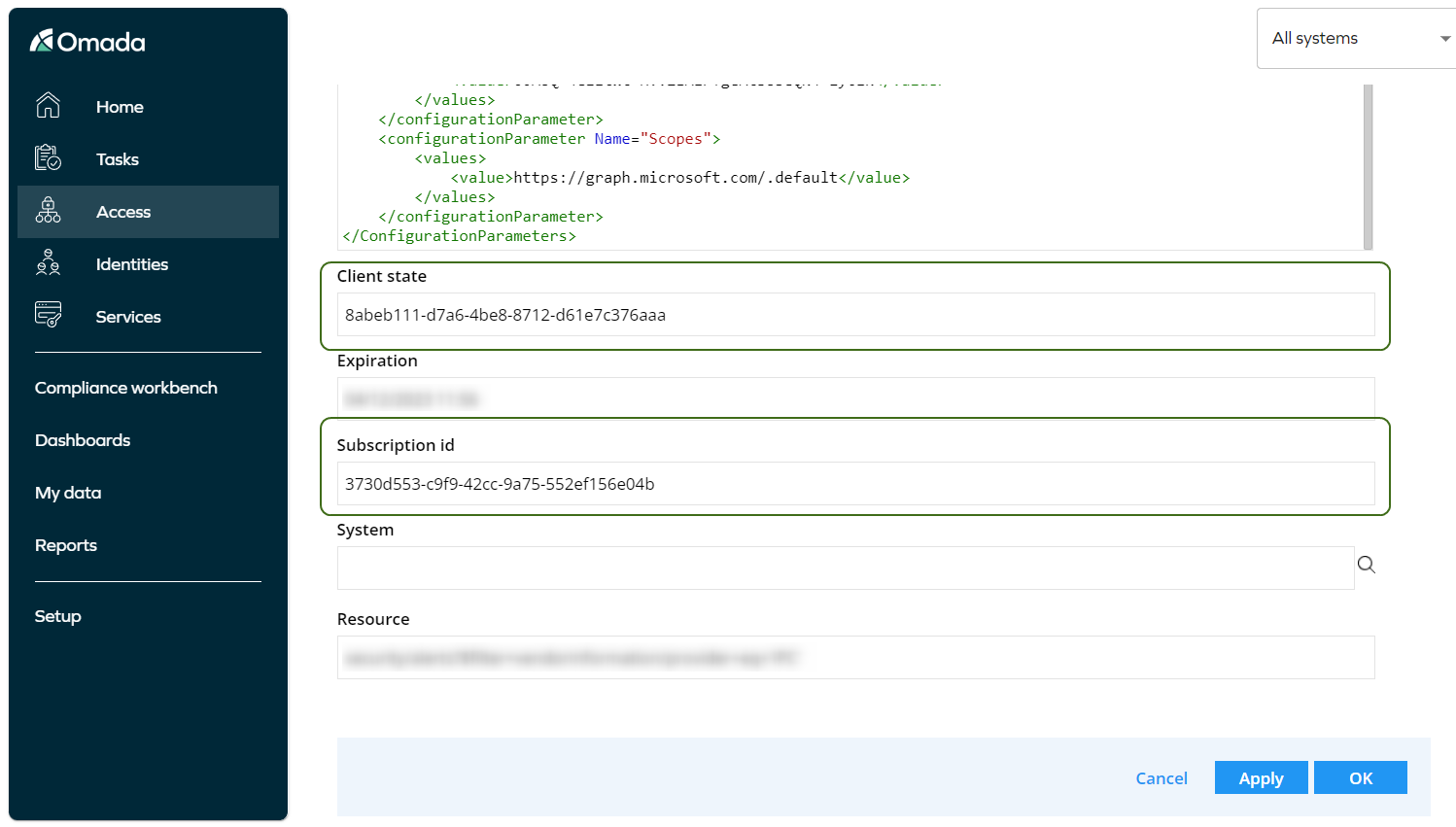
When you click the Apply button and save the subscription data connection, you will be provided with a new Subscription id value from the MS Graph and the Client state value.
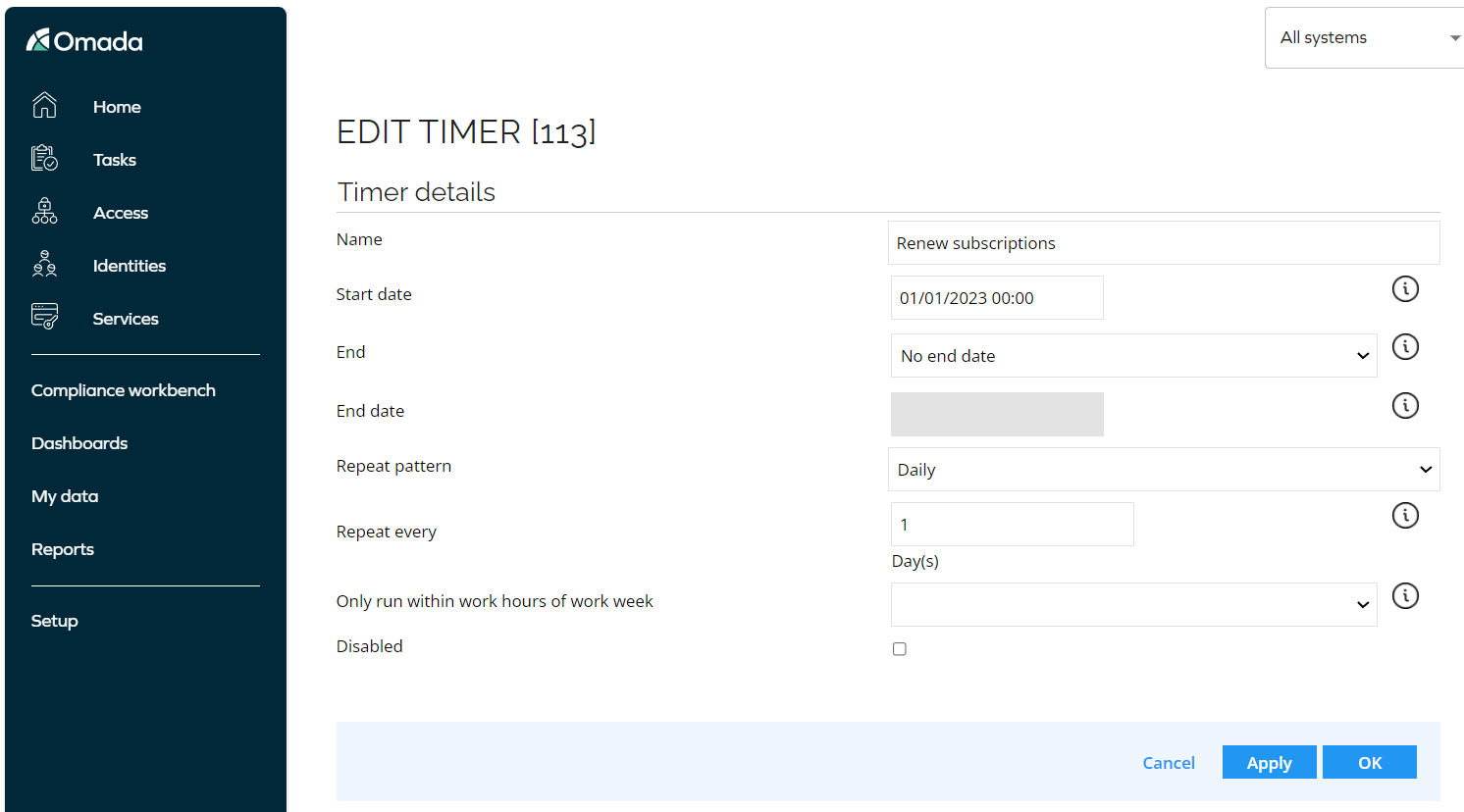
Enable the Renew Subscription timer
To refresh a subscription, you can enable the Renew Subscription timer. To do so:
-
Go to Setup and open the timer list.
-
Open the timer that is called Renew subscriptions.
-
Uncheck the Disabled checkbox.
-
Click the Apply button.
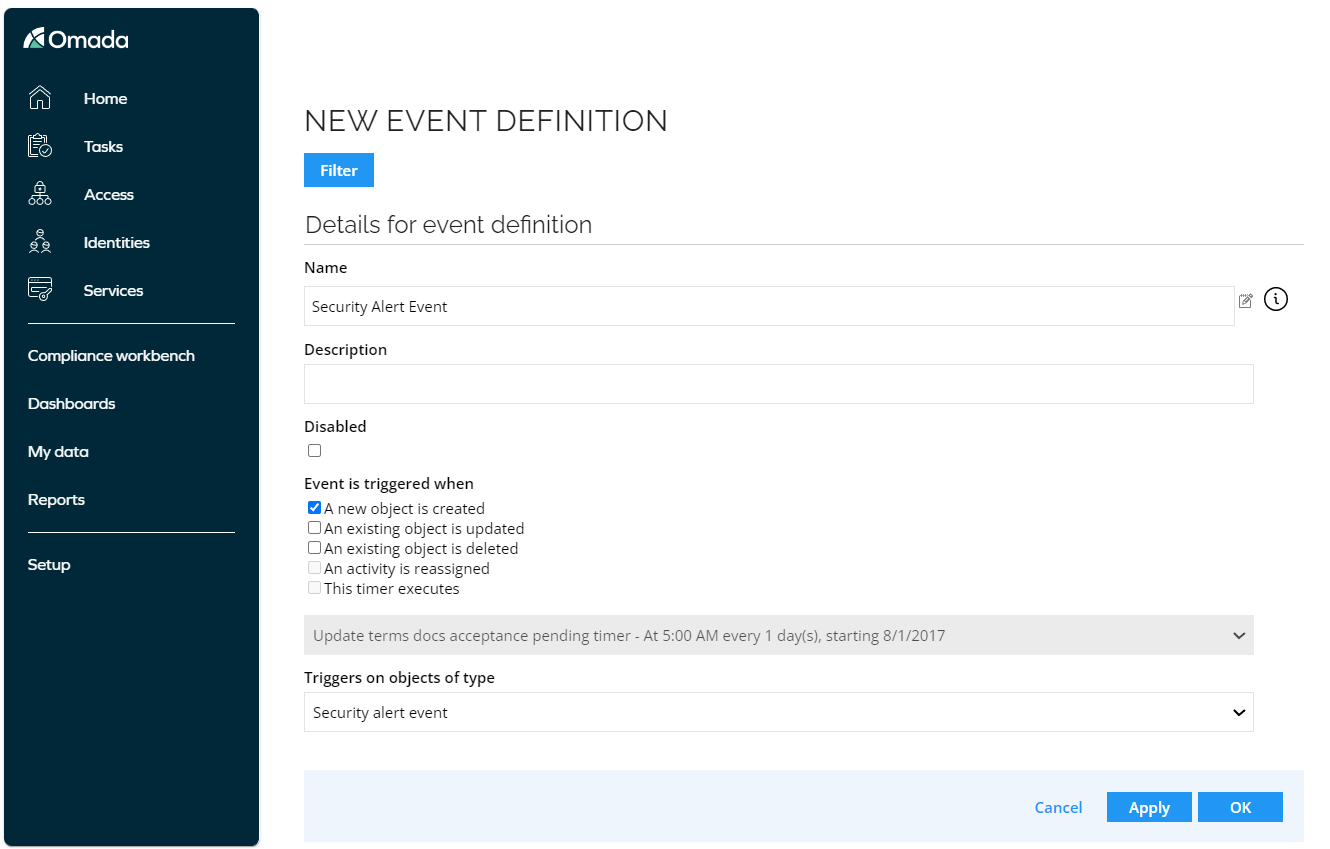
Create an event definition
To create an event definition to react on a security event:
-
Go to the Setup > Event definitions tab.
-
Click the New button.
-
Provide the Name of the new event definition.
-
In the Triggers on object of type dropdown menu, select the Security alert event option.
Configure the filter
The data object filter allows you to use filter expressions on event attributes. You can use it to filter a certain event category and to filter an event severity.
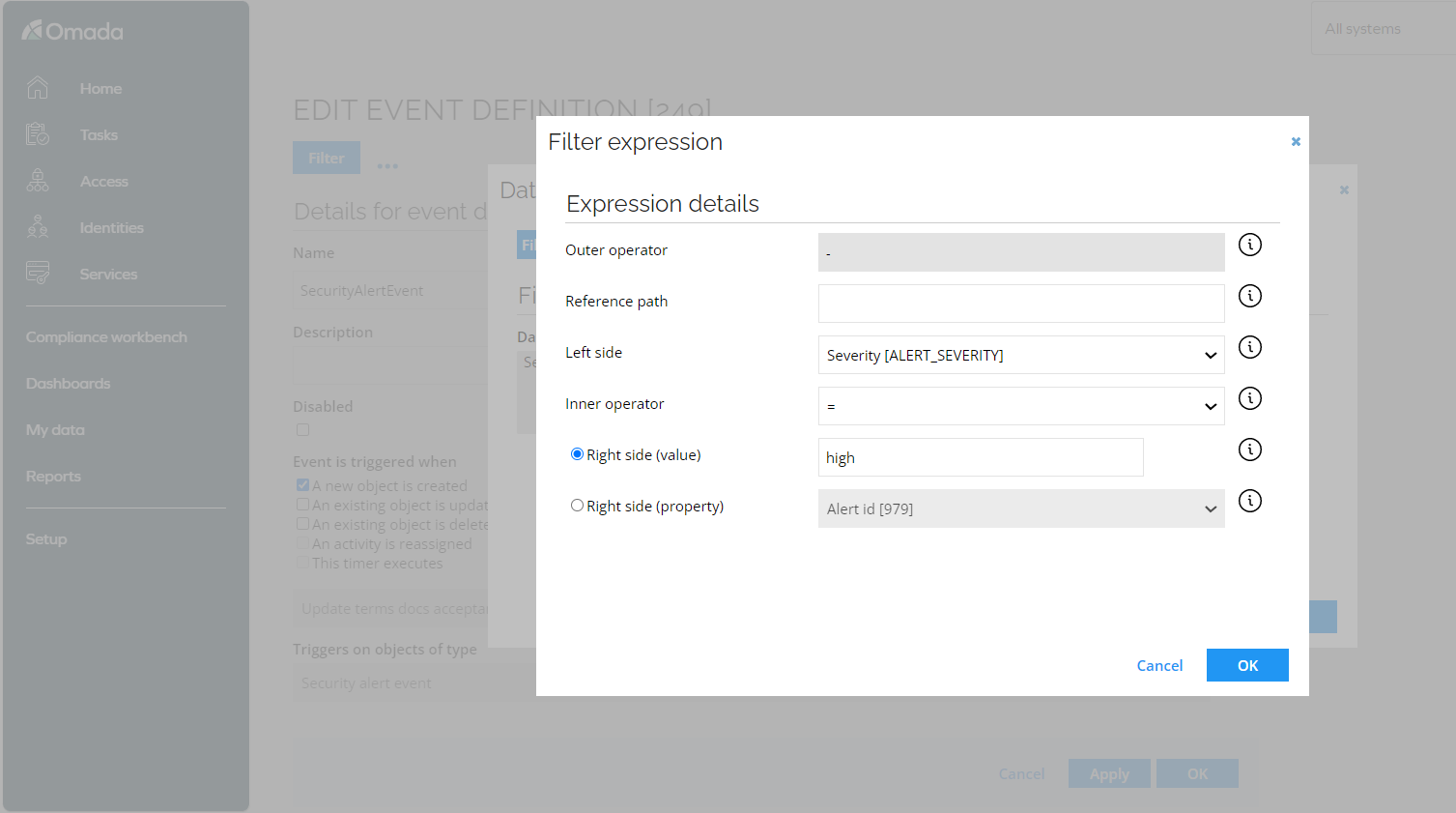
It is important to have different event definitions for situations when the Azure account is not known to Omada Identity or when the Azure account is unresolved.
For example, a filter expression can be configured with "Identity" not in "<empty>" values for event actions not handling unknown accounts.
A filter can also be configured with "Identity" not in "Identity, Unresolved" for event actions not targeted at orphan accounts.
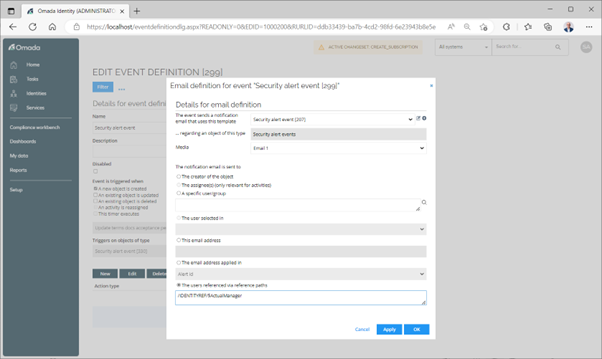
Configure the event action
To configure the event action:
- Go to the Event Actions tab and click the New button.
- Then, configure either Send email or Execute code method action.
For example: by configuring The users referenced via reference paths field to the /IDENTITYREF/\$ActualManager value, a e-mail can be sent to the manager of the identity referenced in the event.
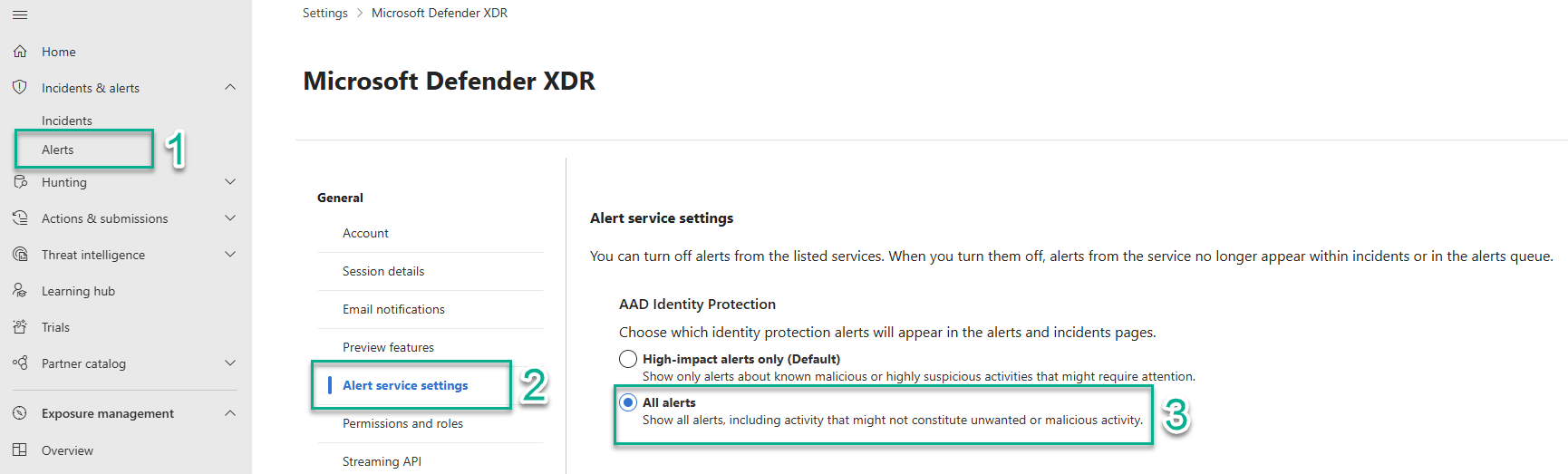
Security alerts in Microsoft Defender
Enable Microsoft Defender security alerts in the Microsoft Defender admin center:
- Below Incidents & alerts, select Alerts.
- Below General, select Alert service settings.
- Select All alerts.